Author: Lisa
Editor: Sherry
Background
On-chain messaging, as a special communication method in the blockchain world, has been frequently used in various security incidents in recent years. For example, recently, SlowMist assisted KiloEx in engaging in multiple rounds of communication with attackers through on-chain messaging, ultimately facilitating the return of all stolen funds amounting to 8.44 million USD. In an anonymous environment, on-chain messaging can serve as an effective tool for establishing initial dialogue, laying the groundwork for subsequent fund recovery.
In our previous article "On-chain Messaging in the Theft Emergency Rescue Guide," we detailed the messaging methods on Ethereum. The Bitcoin network also supports on-chain messaging, but the implementation methods differ slightly. The core tool for on-chain messaging in Bitcoin is the OP_RETURN instruction. It allows users to embed 80 bytes of custom data in a transaction, which will not be used by nodes for transaction validation and will not affect the UTXO status; it is purely for recording information and will be fully recorded on the blockchain.
How to Use OP_RETURN for On-chain Messaging
Step 1: Encode the Message Content
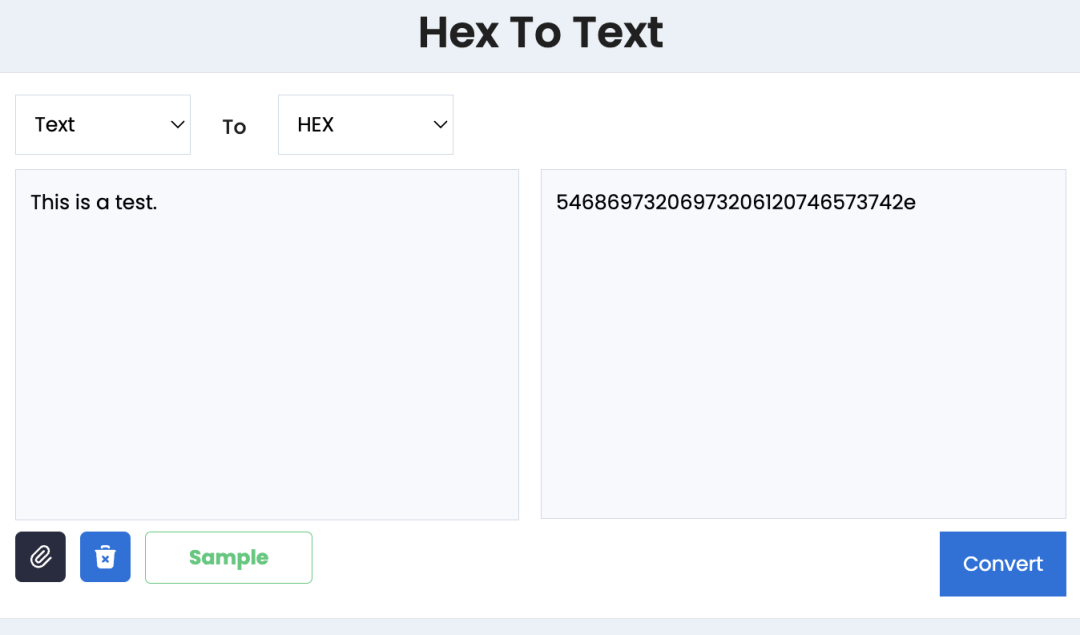
First, convert the text information to be sent into hexadecimal (HEX) format. The OP_RETURN instruction on the Bitcoin chain only accepts HEX format data.
For example, if you want to leave a message:
This is a test.
The converted HEX would be:
54686973206973206120746573742e
You can use online format conversion tools or complete it through a Python script:
text = "Hello, this is a test."
hex_text = text.encode("utf-8").hex()
print(hex_text)
The message content must be less than 160 hexadecimal characters, which is 80 bytes. If the length exceeds this, it is recommended to simplify the information or send multiple messages.
Step 2: Construct a Transaction with OP_RETURN
Next, you need to use a Bitcoin wallet or tool that supports custom transactions to create a transaction containing an OP_RETURN output.
Taking Bitcoin Core as an example, manually add the OP_RETURN output using createrawtransaction:
bitcoin-cli createrawtransaction '[{"txid":"your_input_txid","vout":0}]' '[{"data":"54686973206973206120746573742e"}]'
The constructed transaction will not actually transfer funds but will only write this message on-chain.
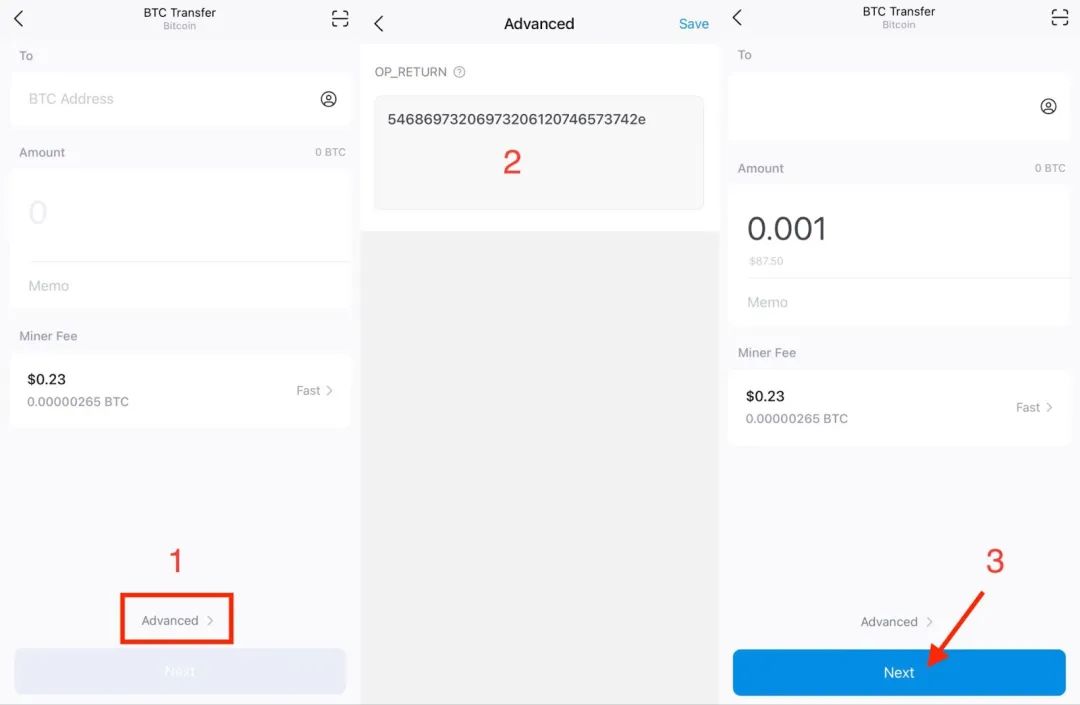
Taking the imToken wallet as another example, enter the BTC wallet transfer interface and open "Advanced Mode." In the "OPRETURN" input box, enter the hexadecimal information. Click "Next" to complete the transaction information confirmation, and enter the transaction password to successfully send the transaction with OPRETURN information. Please ensure that "Input Amount = Output Amount + Miner Fee."
Step 3: Broadcast the Transaction
Broadcast the signed transaction through the Bitcoin network. Since OP_RETURN transactions do not actually transfer funds, they must include a miner fee to be processed, waiting for miners to package it into a block. Once the transaction is confirmed, the message will be permanently stored in the Bitcoin blockchain.
Step 4: View the Message Content
After completing the transaction, you will receive a TXID, which can be viewed through a block explorer. The explorer will usually automatically decode the OP_RETURN hexadecimal data back to ASCII, for example:
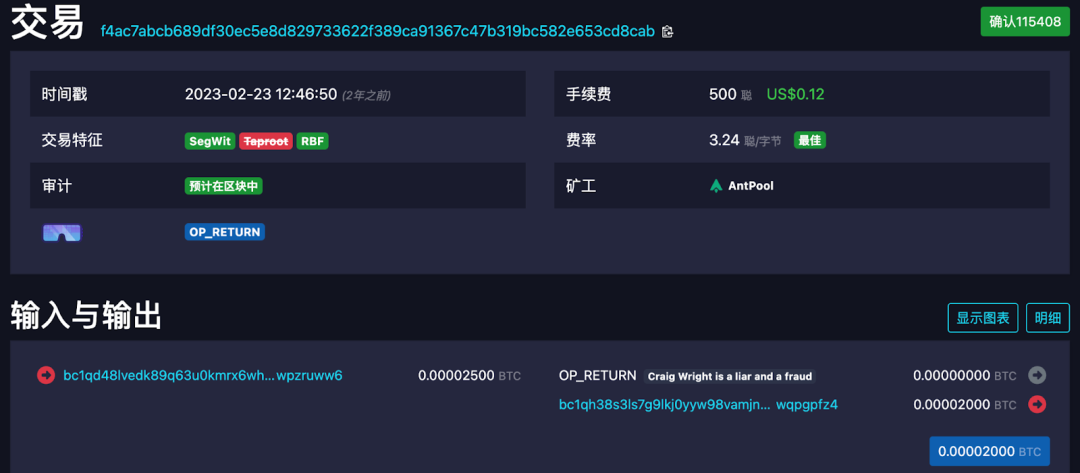
(https://mempool.space/tx/f4ac7abcb689df30ec5e8d829733622f389ca91367c47b319bc582e653cd8cab)
OP_RETURN Applications
In security incidents, some attackers leave messages on-chain using OPRETURN to actively express their intention to return funds to the project party, or project parties and white hat teams also use this method to reach out to attackers in an attempt to establish contact. In addition to being used in negotiation scenarios, OPRETURN is also used for "tagging" operations. For example, Chainalysis revealed that on the eve of the outbreak of the Russia-Ukraine war in 2022, an unidentified Bitcoin user used OP_RETURN on-chain messaging to tag nearly 1,000 addresses suspected of being linked to Russian security agencies. These messages were written in Russian and directly pointed out that these addresses might be involved in cyberattacks or espionage activities:
- "GRU to SVR. Used for hacking!"
- "GRU to GRU. Used for hacking!"
- "GRU to FSB. Used for hacking!"
- "Help Ukraine with money from the GRU Khakir"
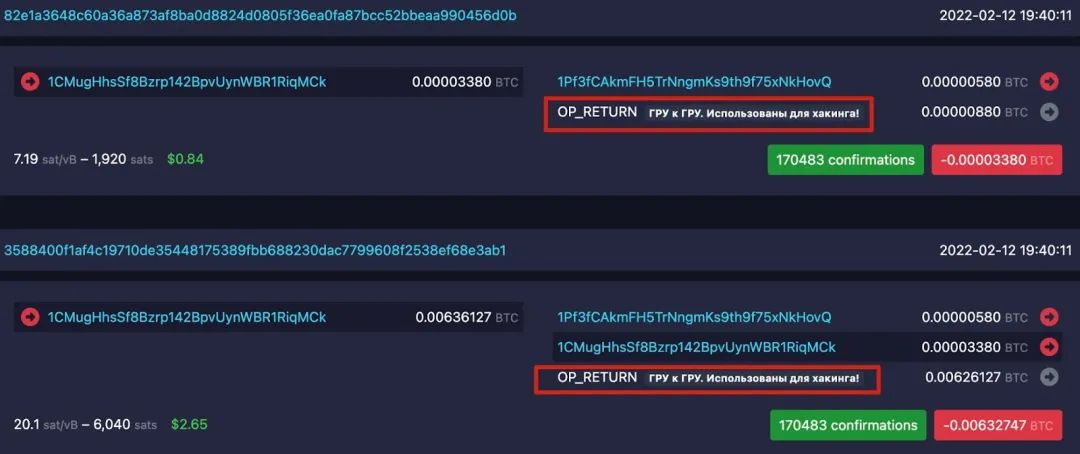
(https://mempool.space/address/1CMugHhsSf8Bzrp142BpvUynWBR1RiqMCk)
This user, when posting these warnings, was not merely leaving messages but also burned a large amount of Bitcoin. Due to the nature of OP_RETURN outputs, any Bitcoin sent to such transactions will be burned and cannot be used. It is reported that this user burned Bitcoin worth over 300,000 USD in this series of operations.
Conclusion
On-chain messaging, especially with OP_RETURN in the Bitcoin network, provides an anonymous, public, and immutable communication method, widely used in the initial contact and information transmission for fund recovery. However, it is important to note that on-chain messages may also be used by attackers to guide victims to malicious links or perform risky operations (such as entering private keys for decryption), so it is essential to remain vigilant and avoid viewing and processing suspicious information on untrusted devices. In the event of a security incident, it is recommended to contact a professional security team for assistance in analysis as soon as possible to improve the success rate of fund recovery. At the same time, users and project parties should continuously strengthen their security awareness to avoid becoming targets of attacks.
免责声明:本文章仅代表作者个人观点,不代表本平台的立场和观点。本文章仅供信息分享,不构成对任何人的任何投资建议。用户与作者之间的任何争议,与本平台无关。如网页中刊载的文章或图片涉及侵权,请提供相关的权利证明和身份证明发送邮件到support@aicoin.com,本平台相关工作人员将会进行核查。




