On February 21, 2025, the cryptocurrency exchange Bybit experienced a massive security breach, resulting in the theft of approximately $1.5 billion in assets from its Ethereum cold wallet. This incident is considered the largest single theft in cryptocurrency history, surpassing previous records such as Poly Network (2021, $611 million) and Ronin Network (2022, $620 million), causing a significant impact on the industry.
This article aims to introduce the hacking incident and its money laundering methods while warning of an impending wave of large-scale freezes targeting OTC groups and crypto payment companies in the coming months.
Theft Process
According to Bybit's Ben Zhou and preliminary investigations by Bitrace, the theft process is as follows:
Preparation for Attack: The hacker deployed a malicious smart contract (address: 0xbDd077f651EBe7f7b3cE16fe5F2b025BE2969516) at least three days before the incident (on February 19), laying the groundwork for the subsequent attack.
Infiltration of Multi-Signature System: Bybit's Ethereum cold wallet uses a multi-signature mechanism, which typically requires multiple authorized signatures to execute transactions. The hacker infiltrated the computer managing the multi-signature wallet through unknown means, possibly via a disguised interface or malware.
Disguised Transaction: On February 21, Bybit planned to transfer ETH from the cold wallet to the hot wallet to meet daily trading needs. The hacker took advantage of this opportunity, disguising the transaction interface as a normal operation, and induced the signers to confirm a seemingly legitimate transaction. However, the signature actually executed a command that altered the logic of the cold wallet's smart contract.
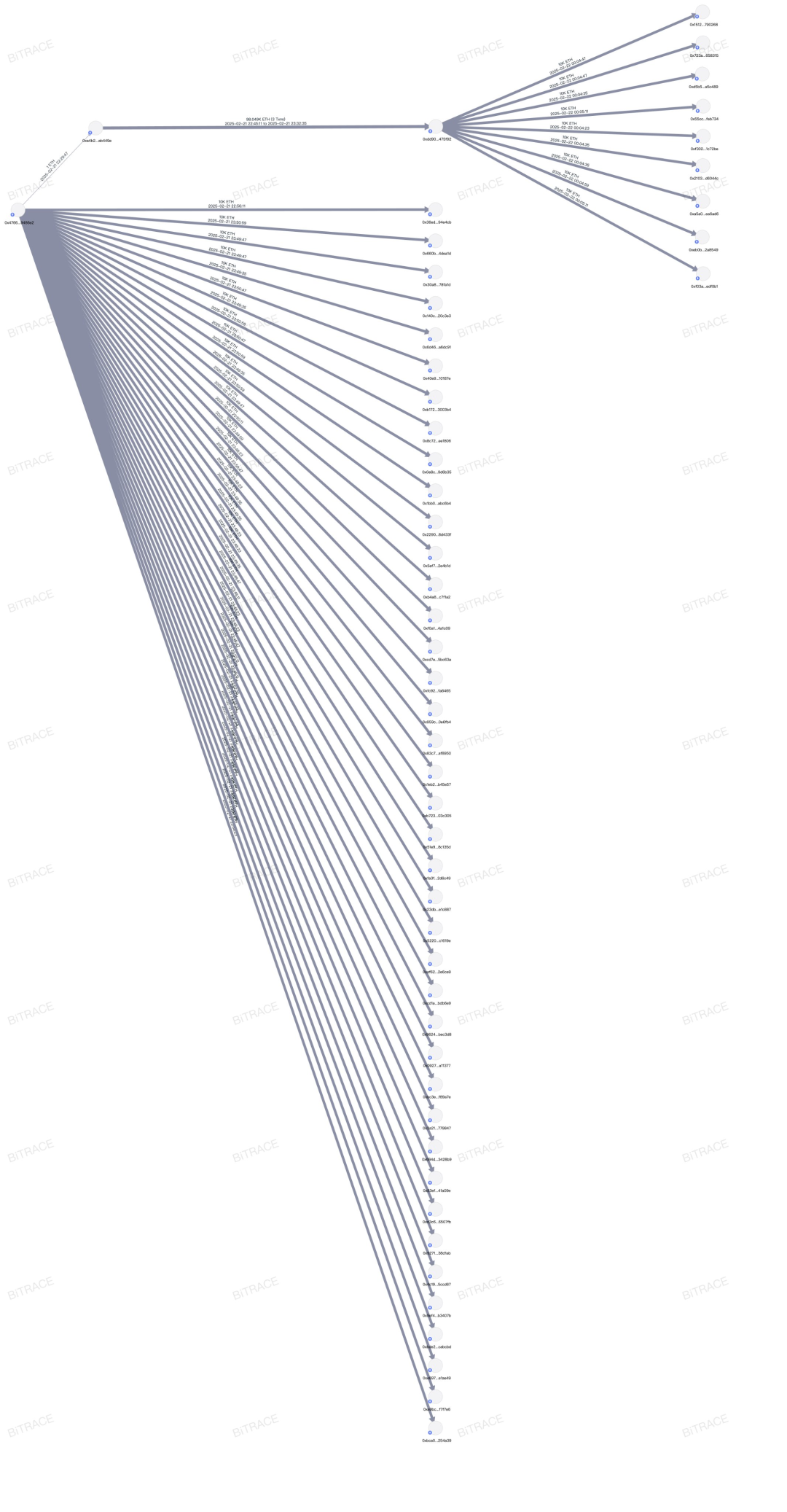
Fund Transfer: Once the command took effect, the hacker quickly took control of the cold wallet, transferring approximately $1.5 billion worth of ETH and ETH staking certificates to an unknown address (initially tracked address: 0x47666Fab8bd0Ac7003bce3f5C3585383F09486E2). Subsequently, the funds were dispersed to multiple wallets and began the money laundering process.
Money Laundering Methods
The money laundering process can be roughly divided into two phases:
The first phase is the early fund splitting phase, where the attackers quickly exchanged ETH staking certificate tokens for ETH tokens, rather than stablecoins that could be frozen. They then strictly split and transferred the ETH to subordinate addresses in preparation for laundering.
It was during this phase that the attackers' attempt to exchange 15,000 mETH for ETH was halted, allowing the industry to recover this portion of the loss.
The second phase involves the money laundering work. The attackers transfer the obtained ETH through centralized or decentralized industry infrastructures, including Chainflip, Thorchain, Uniswap, eXch, etc. Some protocols are used for fund exchange, while others are used for cross-chain fund transfers.
As of now, a large amount of stolen funds has been exchanged for BTC, DOGE, SOL, and other layer 1 tokens for transfer, and some have even issued memecoins or transferred funds to exchange addresses for obfuscation.
Bitrace is monitoring and tracking addresses related to the stolen funds, and this threat information will be synchronized and pushed in BitracePro and Detrust to prevent users from inadvertently receiving stolen funds.
Criminal Record Analysis
Analysis of the address 0x457 in the fund chain revealed that it is related to the theft incident at BingX exchange in October 2024 and the theft incident at Phemex exchange in January 2025, indicating that the mastermind behind these three attacks is the same entity.
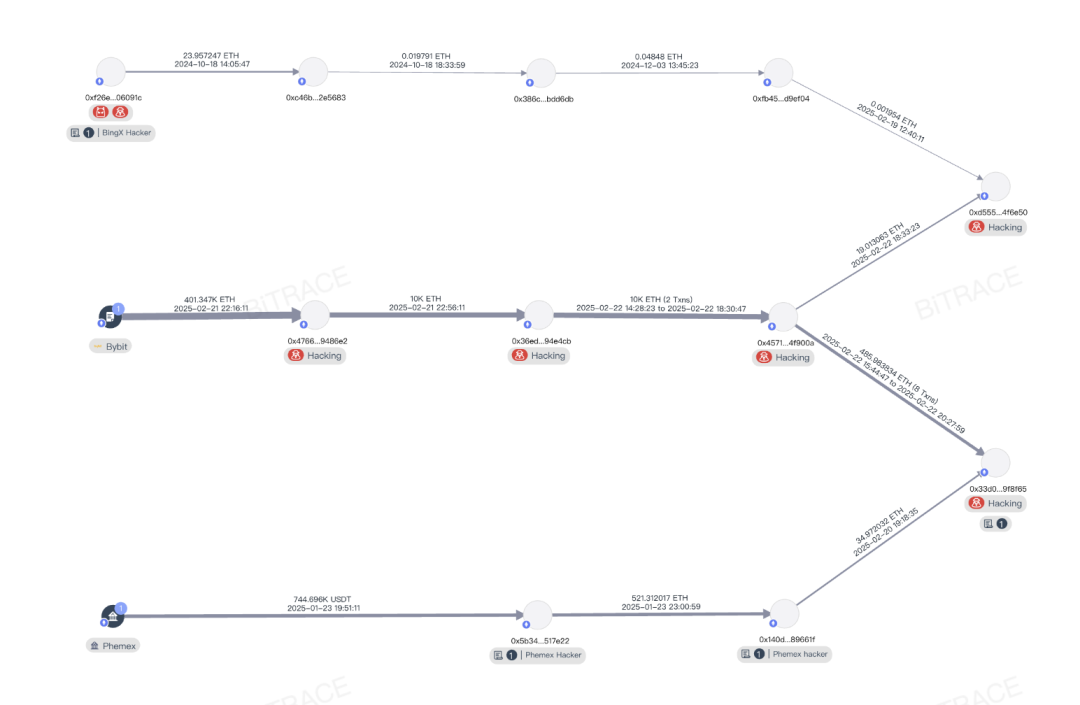
Combining its highly industrialized money laundering methods and attack techniques, some blockchain security professionals attribute this incident to the notorious hacker organization Lazarus, which has launched multiple cyberattacks on institutions or infrastructures in the crypto industry over the past few years, illegally seizing cryptocurrencies worth billions of dollars.
Freeze Crisis
In the course of Bitrace's investigations over the past few years, it has been found that this organization not only uses unlicensed industry infrastructures for money laundering but also heavily relies on centralized platforms for dumping, directly leading to many accounts of exchange users, who either intentionally or unintentionally received stolen funds, being subjected to risk control, and the business addresses of OTC merchants and payment institutions being frozen by Tether.
In 2024, the Japanese cryptocurrency exchange DMM was attacked by Lazarus, resulting in the illegal transfer of Bitcoin worth up to $600 million. The attackers bridged the funds to the Southeast Asian cryptocurrency payment institution HuionePay, causing the latter's hot wallet address to be frozen by Tether, locking over $29 million that could not be transferred;
In 2023, Poloniex was attacked, with the attackers suspected to be from the Lazarus group, resulting in the illegal transfer of over $100 million in funds. Some of the funds were laundered through over-the-counter trading, leading to the freezing of many OTC merchants' business addresses or the risk control of exchange accounts used to store business funds, significantly impacting business activities.
Conclusion
Frequent hacking incidents have caused significant losses to our industry, and subsequent money laundering activities have further polluted more personal and institutional addresses. For these innocent parties and potential victims, it is crucial to pay attention to these threat funds in business activities to prevent being affected.
免责声明:本文章仅代表作者个人观点,不代表本平台的立场和观点。本文章仅供信息分享,不构成对任何人的任何投资建议。用户与作者之间的任何争议,与本平台无关。如网页中刊载的文章或图片涉及侵权,请提供相关的权利证明和身份证明发送邮件到support@aicoin.com,本平台相关工作人员将会进行核查。




