Smart money not only needs to be played smartly but also needs to be stored smartly.
Written by: Pzai, Foresight News
An increasing number of players are flocking to the on-chain gold mine, striving to uncover their future opportunities. However, during the on-chain usage process, users may encounter certain operational errors, including but not limited to sending to the wrong address (some on-chain users have suffered huge losses by mistakenly sending nearly 8000 ezETH), signature losses (permit), and theft of authorizations, among others.
In addition to personal operations, external risks are also quietly approaching. Recently, a failure of an on-chain trading tool led to the transmission and theft of users' so-called "self-custody" wallet private keys through various means, casting a shadow over the asset security of many on-chain users. This article organizes the basic understanding of wallet usage, hoping to provide better wallet usage references for on-chain users.
Wallet Private Key
Most on-chain wallets are "self-custody" wallets, generally requiring users to self-manage their wallet private keys / mnemonic phrases. As for the storage of wallet private keys, the market offers a variety of solutions, with the following being the more mainstream methods of private key storage:
- Manual Type — Before using the wallet, users need to manually back up their wallet mnemonic phrases or private keys. Most software and hardware wallets adopt this model.
- Cloud Backup — Some wallets (such as Worldcoin or Ledger Recover) offer cloud backup features, allowing users to encrypt and back up their wallets to cloud services like Google Cloud or iCloud, which can be restored through cloud storage when account access is lost.
- No Private Key — Users create a no-private-key wallet through external media (such as a passkey or Google account) and access the chain through the wallet provider's services.
In terms of private key security, the manual type requires certain habits from users regarding storage, generally needing multiple backups and carrying the risk of losing backups. To reduce the difficulty of self-custody for users and lay the groundwork for large-scale applications, many wallet applications have turned to integrate with Web2 cloud services, providing services through relatively centralized security.
From a user experience perspective, the latter two are undoubtedly the most in line with user operation habits, also reducing certain risks of private key leakage on the user side. However, many on-chain tools today generate wallets directly within the tool, requiring users to back them up themselves. For users, high-frequency interactions generally need to be directly combined with on-chain functions, so private keys, as the most universal form, have the widest applicability. Generally, users will use computers or handwritten methods to back up private keys, but most private key storage on computers carries the risk of network attacks, so it is recommended that all self-custody wallet private keys be stored offline.
Hardware Wallets
On the other hand, many users also use hardware wallets to handle transactions. One major advantage of hardware wallets is that, compared to software wallets that interact online, hardware wallets can ensure that private keys do not leak outside the device.
Current hardware wallet interaction behaviors are mainly divided into two categories:
- QR Code Type: Users interact with the wallet using QR codes, where the device scans the transaction QR code, signs it, and then feeds it back to the wallet.
- Connection Type: Users connect the device to external devices such as computers or mobile phones via Bluetooth or data cables for transaction signing.
Taking Ledger as an example, several wallets in its product line support USB-C, Bluetooth, and QR code connections, with varying prices.
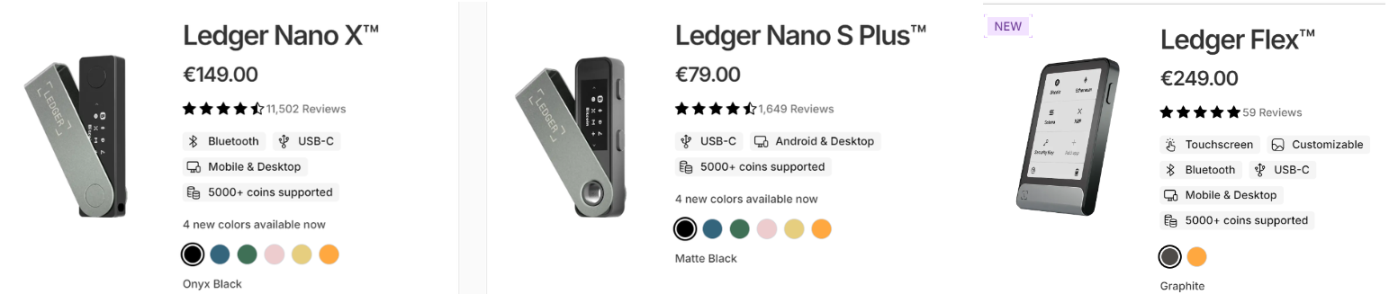
For hardware wallet users, QR code signing has the widest applicability but the highest hardware requirements, making it the most expensive. Relatively cheaper wallets require a data cable for use, which also limits their universality. However, as the current highest security wallet category, they still hold value for users with certain asset custody needs. Additionally, some solutions are transferring QR code signing functions to commonly used devices like smartphones (e.g., AirGap Wallet), but compared to pure hardware wallets, the requirement for devices to remain offline is relatively reduced.
Operational Habits
In addition to understanding wallets, users also need to pay sufficient attention to their own wallet usage habits. In many theft incidents, some risks can be avoided through user operations. Here, the author has compiled several beneficial operational habits.
Security Plugins
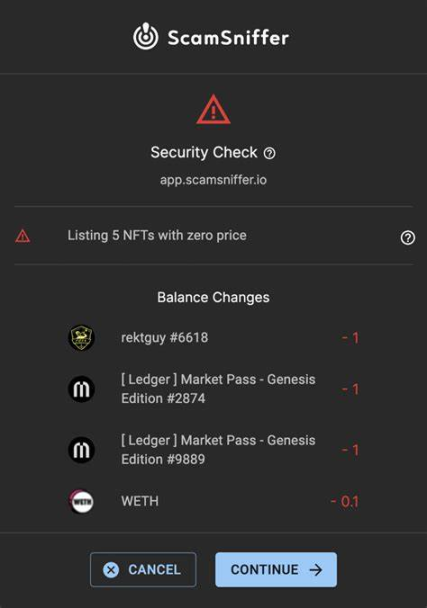
Using security plugins for transaction identification should be a consensus among all on-chain users. Existing security plugins (such as Scam Sniffer and AlphaOS) can cover prompts for front-end risks, authorization (signature) risks, and transaction risks, and can further analyze transactions, providing detailed risk alerts for assets.
Address Book
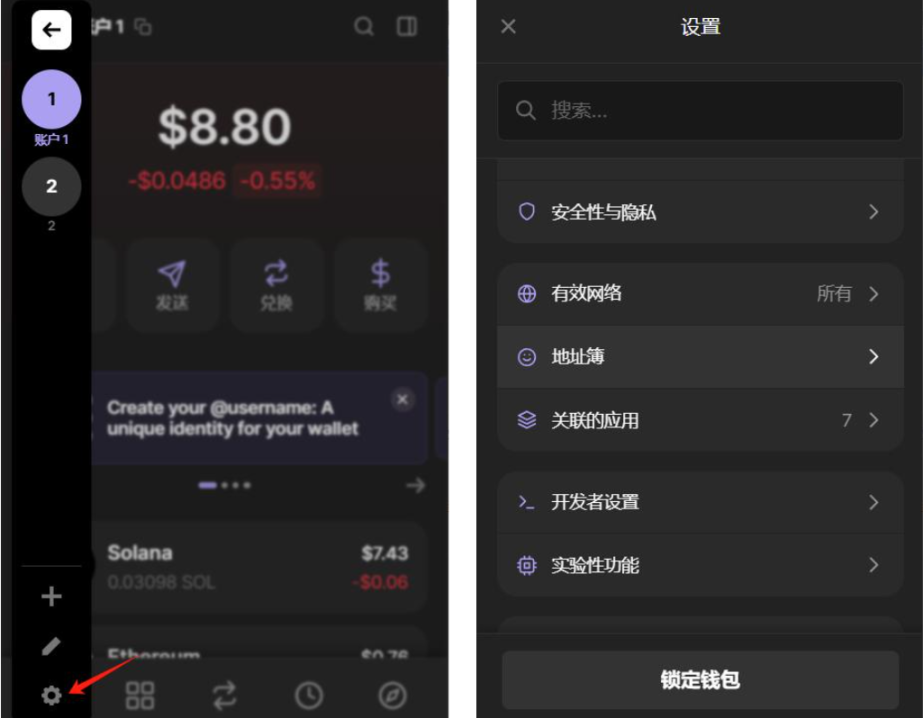
The address book, as one of the common functions of wallets, can significantly reduce the risk of transfer errors if users develop the habit of using it. However, since the interaction logic of each wallet is different, users' access to the address book may vary slightly. For example, in Phantom, users can click the upper left corner — Settings — Address Book to set it up. The settings in Metamask are similar.
Clipboard
The clipboard, as a storage place for users to copy and paste information, should not retain sensitive information for long. Some attackers use malicious software like "clipboard hijackers" to run in the clipboard, replacing copied wallet addresses (hence the need to remember the address book) or stealing private keys. In terms of user usage, the author suggests to avoid copying private keys to the clipboard as much as possible; if it is necessary, it should be done under offline conditions, and the clipboard should be cleared with a cleaning tool before going online.
免责声明:本文章仅代表作者个人观点,不代表本平台的立场和观点。本文章仅供信息分享,不构成对任何人的任何投资建议。用户与作者之间的任何争议,与本平台无关。如网页中刊载的文章或图片涉及侵权,请提供相关的权利证明和身份证明发送邮件到support@aicoin.com,本平台相关工作人员将会进行核查。



