In the world of cryptocurrency, asset security has always been a Damocles sword hanging over users' heads. Due to the threshold for tracking on-chain funds, when victims are unfortunately stolen from, they often find it difficult to understand the complex on-chain transactions. Faced with a series of seemingly random characters and numbers, they cannot see the hidden flow of funds behind them. Therefore, many victims are at a loss after their funds are stolen, and some even passively give up. This incorrect approach not only misses the best opportunity to minimize losses but also leads to secondary losses of funds.
This article will explore how ordinary Web3 participants can minimize their losses after their cryptocurrency is stolen, and warn users against the passive attitude after being stolen, using real-life cases as examples.
Transfer Remaining Assets
Victims should first accept the fact that they have been stolen from and respond to the upcoming "challenge" with a positive attitude. Victims should immediately transfer the remaining cryptocurrency assets (tokens, NFTs, asset certificates, etc.) in their wallets to a new, secure wallet address. The purpose of this step is to place the remaining assets in a place beyond the reach of criminals, to prevent further losses.
The necessity of timely transferring remaining assets after being stolen is illustrated by a real case. In this case, the victim intended to participate in the 14-day lock-up pledge of the Moonbeam project to obtain a high POS annualized return, but inadvertently downloaded a fake wallet, putting the funds at risk of being stolen after unlocking. With the help of the Bitrace team, the victim successfully outpaced the hacker and recovered most of the losses. However, in the excitement, the victim did not take Bitrace's well-intentioned advice to heart—
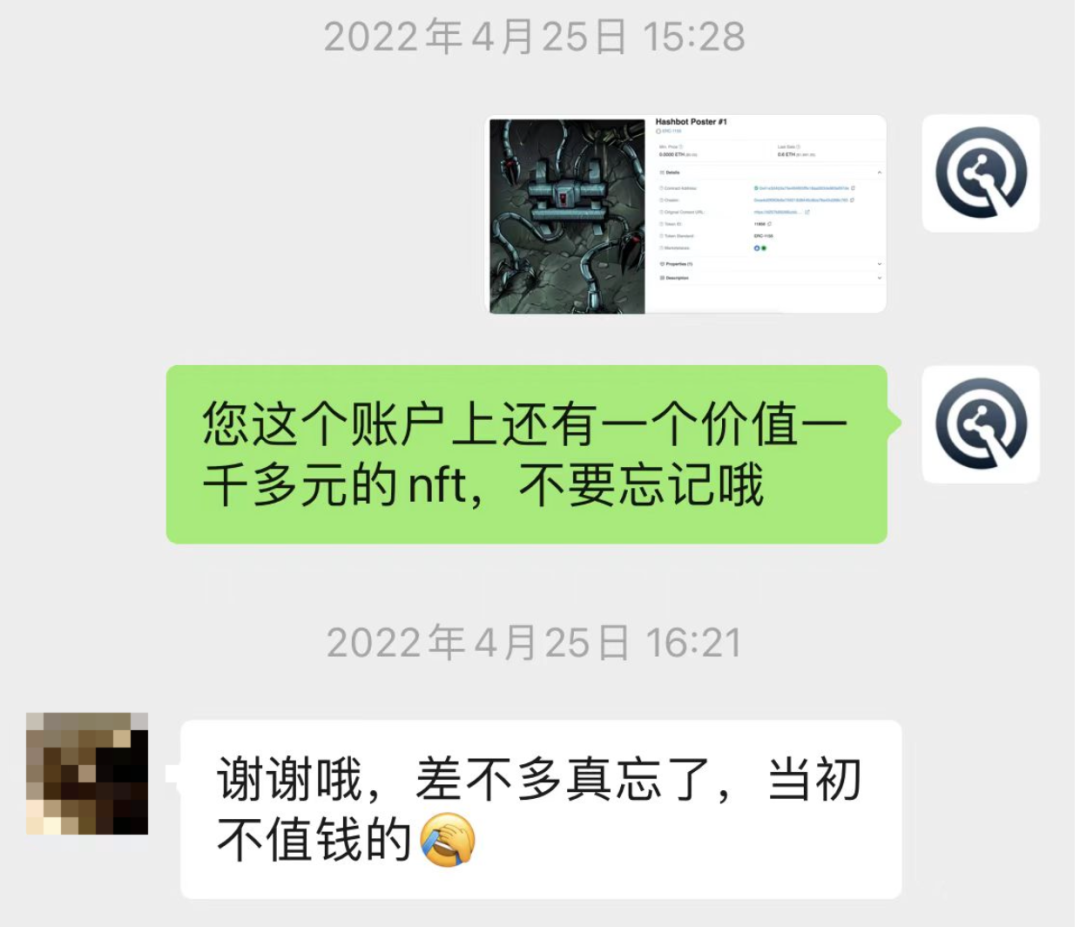
The victim is reminded to transfer NFTs in the wallet that may be used as future airdrop certificates for projects.
In May of the same year, the decentralized trading platform Hashflow announced its token economic model, stating that it would airdrop 6.75% of the tokens to NFT holders (the NFT mentioned in the chat screenshot) and early users. That night, the victim contacted Bitrace again, stating that the hacker had transferred the airdrop permissions of 38 addresses in the victim's wallet, totaling over 20,000 $HFT, and successfully claimed them. Based on the opening price of $HFT on Binance at the time, the victim further lost approximately 640,000 RMB due to not transferring the remaining assets in the stolen wallet in a timely manner. It can be seen that correctly mastering the stop-loss operation after being stolen is very important.
Timely Revoke Risk Authorization
When operating on the chain, smart contracts and decentralized applications (DApps) often require users to authorize certain operation permissions. After being stolen from, victims should immediately revoke the permissions of unreliable smart contracts or DApps to access their wallets. This can be done by accessing the relevant blockchain browser and using the "revoke" function, or by visiting the revoke.cash website to cancel the risk authorization.
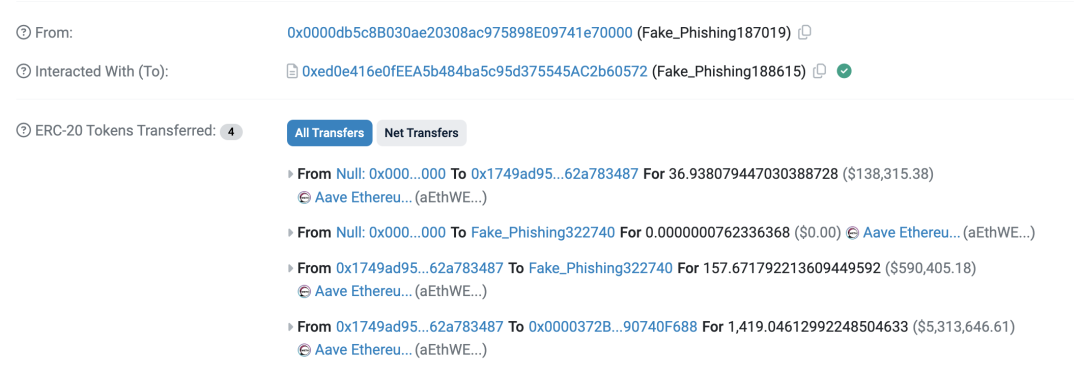
Taking the address 0x17…..3487 as an example, the victim approved a phishing link and had nearly 1,600 $ETH worth of token assets stolen. Unexpectedly, 1 day later, due to not revoking the authorization for the malicious contract in a timely manner, the victim had 158 Ethereum token assets (worth approximately 4 million RMB) stolen. However, this was an unnecessary loss that could have been avoided by timely revoking the authorization.
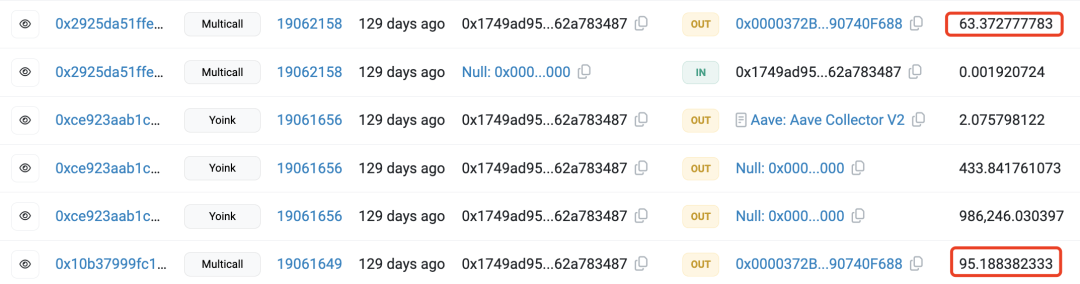
It can be seen that revoking risk authorization immediately after funds are stolen is crucial, as this action can immediately cut off any unauthorized third party or malicious smart contract's access to the victim's remaining wallet funds, preventing these authorizations from being used to execute further asset transfers and thus avoiding further losses.
Seek Help from Security Companies
On-chain tracking has a certain technical threshold, which is a difficult barrier for most non-professional users to overcome. Therefore, victims can seek the services of security companies to conduct blockchain analysis at the first opportunity. Professional blockchain security companies have the ability to track and analyze on-chain transactions.
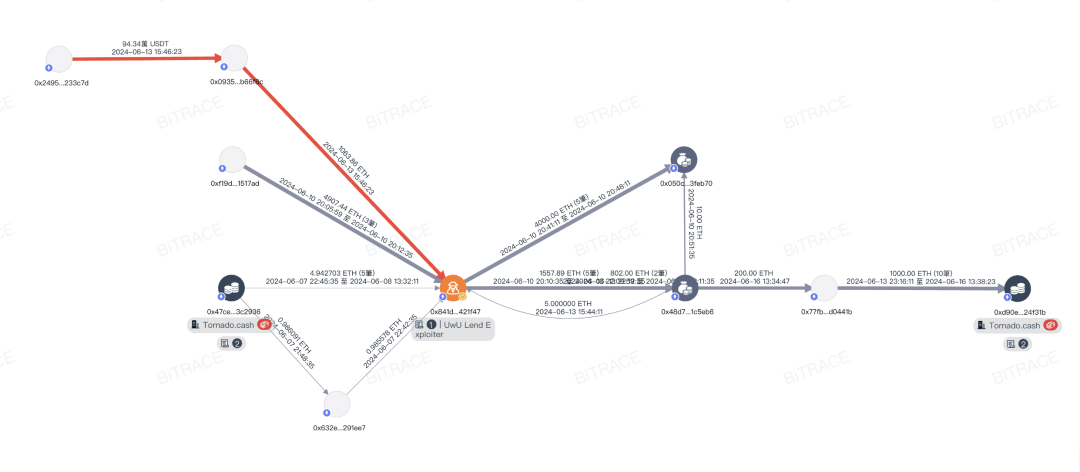
UwU's funds attacked twice
Based on the relevant transaction information and wallet addresses provided by the victim, security experts can use advanced analysis tools to track the flow of stolen funds and may help identify and track related criminal entities, thereby increasing the possibility of recovering the losses. In 2023, Bitrace intercepted and recovered over one billion US dollars' worth of encrypted funds lost by victims, including CEX, DeFi protocols, and ordinary investors.
Conclusion
Every unfortunate event brings us one step closer to a more secure Web3 digital world. Although the losses cannot be erased, correct actions and strategies can reduce the losses to a certain extent. Learning from misfortunes, enhancing personal security awareness, managing digital assets securely (such as using a hardware wallet to store funds), being vigilant against any form of phishing attacks, understanding the latest network threats and protection measures, can prevent stolen events from happening again.
免责声明:本文章仅代表作者个人观点,不代表本平台的立场和观点。本文章仅供信息分享,不构成对任何人的任何投资建议。用户与作者之间的任何争议,与本平台无关。如网页中刊载的文章或图片涉及侵权,请提供相关的权利证明和身份证明发送邮件到support@aicoin.com,本平台相关工作人员将会进行核查。




