Discussion on the DePIN Project and the Legal Issues to Pay Attention to
Author: Liu Honglin, Founder and Director of Shanghai Mankun Law Firm
01 Introduction
In the traditional Internet field, the sharing economy model represented by shared bicycles, shared routers, and storage service leasing has become very mature. In the Web3.0 field, there is also the DePIN (Decentralised Physical Infrastructure Networks) with the goal of improving resource utilization and breaking free from centralized monopolies.
In simple terms, DePIN uses blockchain to record the process of sharing data resources, aiming to build a global interconnected physical infrastructure network ecosystem.
According to data from Coingecko, as of February 2024, the liquidity of assets in the DePIN sector has exceeded $16 billion, and the Messari Report predicts that the market size of DePIN is expected to reach $35 trillion by 2028.
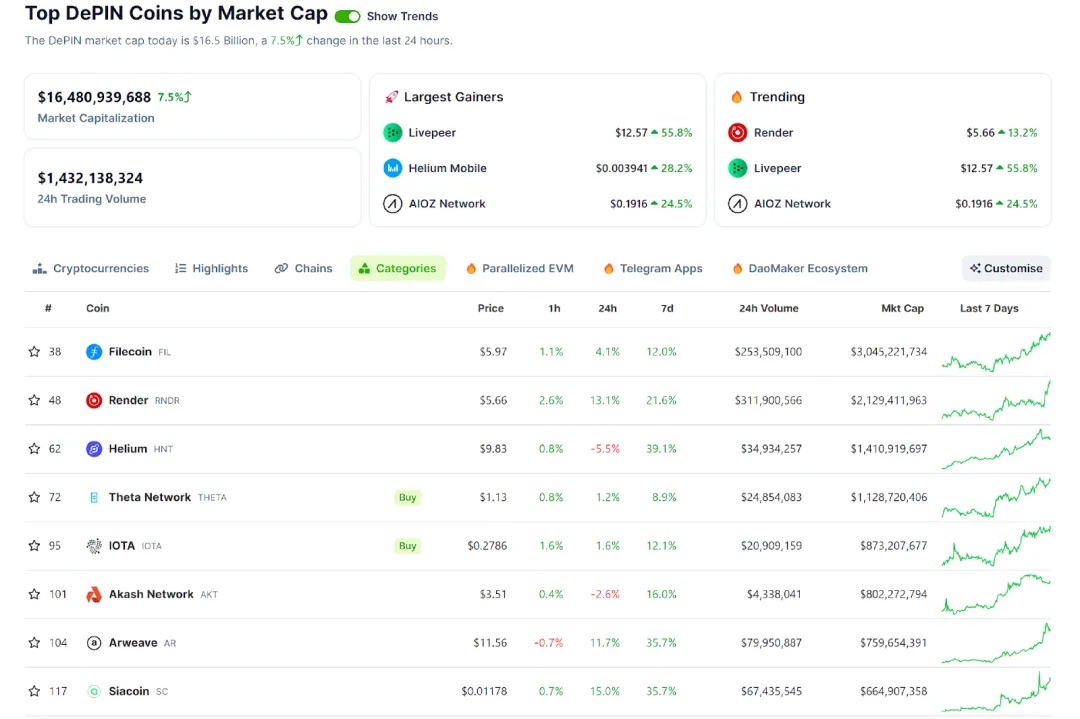 Source: Coingecko, data as of February 2024
Source: Coingecko, data as of February 2024
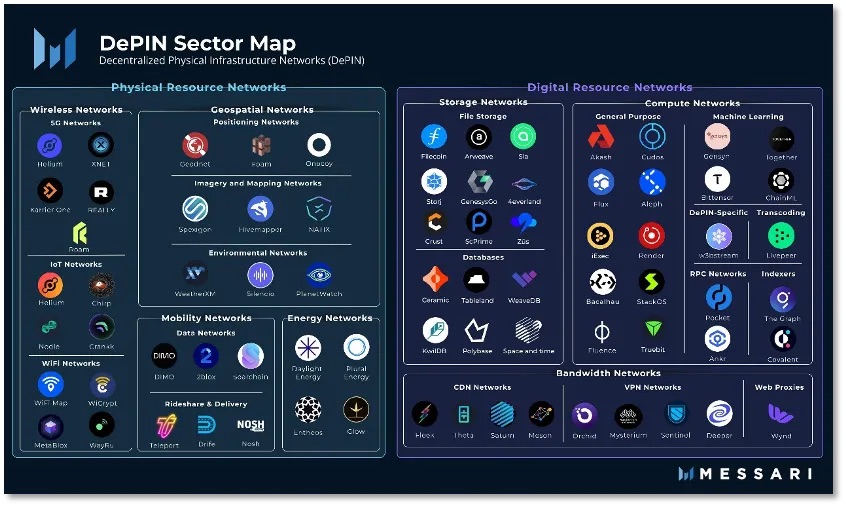 DePIN Project Overview (Image from Messari)
DePIN Project Overview (Image from Messari)
It can be seen that the DePIN track has attracted increasing attention and has become a focus for many projects. The Mankun team not only continues to pay attention to this track but also provides legal services to related projects. This article will discuss the legal issues that need to be considered when carrying out the DePIN project.
02 Analyzing DePIN Business Models from Typical Projects
Filecoin: Incentive Project for Shared Storage Space Filecoin can be considered a veteran DePIN project. As a decentralized storage network based on the InterPlanetary File System (IPFS) protocol, its main role is to connect users with idle storage space on hard drives to users who need space to store data. Through transactions between the two parties, the former provides their storage space to the latter in exchange for FIL tokens. The latter also gains access to storage space at a lower cost, maximizing the additional market value created by idle digital resources.
Render Network: Leader in the AI Sector Render Network (RNDR) is a blockchain-based distributed GPU rendering network platform owned by OTOY. Its main users are those with a large number of rendering tasks, and it provides users with idle GPU computing power. It builds a huge computing market by extending 3D rendering work and applications to the cloud, making it more convenient for users worldwide to provide or obtain high-quality rendering services.
Hivemapper: Decentralized Encrypted Maps Hivemapper is a blockchain-based map network that collects map data from around the world through Hivemapper dashcams installed by global users. Users can receive Honey coins as rewards for providing valuable map information.
The unique feature of Hivemapper lies in its cost advantage. Traditional mapping services like Google Maps use expensive cameras, vehicles, and manpower to map, resulting in high costs. In contrast, Hivemapper leverages a large number of users who frequently drive to collect street images from around the world. Additionally, because the only way to obtain Hivemapper map data is by consuming HONEY, this token also has practical value and sufficient user appeal.
In summary, the core elements of DePIN project business models include:
- Hardware devices purchased and deployed by users for project ecosystem deployment.
- Real goods/services/resources addressing real needs, promoting infrastructure maintenance and improvement.
- Token rewards for resource providers, which can be consumed by using real services or traded for other resources.
03 Legal Risk Analysis of DePIN Projects
1. Does the DePIN Project Violate Prohibitive Regulations in China? In the DePIN project, users earn tokens by maintaining and improving project infrastructure. These tokens can be traded on exchanges or through other means. It seems that the DePIN project is prone to touching upon the negative lists mentioned above.
In fact, although the process of obtaining tokens in DePIN projects is somewhat similar to the mining process under the PoW mechanism, it is not necessarily a resource-wasting industry that consumes a large amount of electricity and generates a large amount of carbon emissions. Instead, it can adjust supply and demand relationships and improve the efficiency of idle resource utilization.
Furthermore, while China prohibits token financing for virtual currencies, it does not deny the property attributes of virtual currencies and does not prohibit all transactions related to virtual currencies. In the past, we have also conducted detailed analyses on this, which can be found in "Three Points to Note for Blockchain Entrepreneurship without Financing."
However, from a judicial practice perspective, regulatory authorities still maintain relatively strict control over the behavior of individuals and entities obtaining tokens from DePIN-type projects.
Taking Filecoin as an example, we searched for disputes related to FIL coins over the past three years and found that the courts mostly cited the content of Notice 924 in their reasoning. They generally simply identified the behavior of the parties involved as "mining activities" and declared the relevant service contracts, commission contracts, and sales contracts invalid, thereby rejecting the plaintiff's claims or requiring the defendant to return the contract funds. There was no detailed analysis. For specific cases, please refer to case numbers (2022) Hu 0114 Min Chu 22068, (2023) Gui 0202 Min Chu 2287, and (2023) Yu 0235 Min Chu 2152.
2. Legal Issues in Data On-chain DePIN projects involve traditional infrastructure sectors, mainly involving the server (cloud) network, wireless network, sensor network, and energy network industries. It can be seen that these industries have a common characteristic: they involve the close collection and use of a large amount of data information. Since most DePIN projects involve overseas users or need to publish data overseas through blockchain, the issue of data exiting the country must be considered.
Taking the previously mentioned Hivemapper project as an example, within a year of its establishment, it mapped approximately 10% of the total global road mileage, collecting a wide range of geographic spatial information data. While it improves people's daily travel, it also brings risks of national data security and sensitive information leakage.
Interestingly, the National Security Department has also recognized this issue and released a public WeChat article in February this year.
3. DePIN Projects Beware of Improper Promotion
## 04 Mankun Lawyer's Compliance Suggestions
In order to better address the risks of DePIN project entrepreneurship, business owners can focus on the following aspects during the project advancement.
1. Designing a Suitable Organizational Structure
Since many activities are restricted in China, it may be better to seek development overseas. More and more project teams are choosing to establish companies and build teams overseas, turning to cryptocurrency-friendly regions such as Hong Kong, Singapore, and Dubai. Only a part of the team is retained in China:
- For teams wishing to conduct DePIN business, especially those with plans to issue tokens in the future, it is recommended to plan an overseas development strategy early and arrange the project company entity overseas.
- Due to the close integration of DePIN projects with hardware devices, production and sales activities related to hardware devices can be carried out in China.
2. Data Security and Cross-Border Compliance
Although DePIN projects are essentially decentralized, they still involve a certain degree of centralized management and coordination in actual operations, and cross-regional data linkage. Therefore, special consideration needs to be given to data compliance and data security:
Personal Information Protection
- Formulate a privacy policy: Explain to users the collection, use, storage, and transmission of personal information, ensuring that the privacy policy complies with legal requirements such as the Personal Information Protection Law (PIPL).
- Obtain user consent: Clearly inform users of the purpose, method, and scope of information processing before collecting and processing personal information, and obtain explicit consent from users.
- Principle of data minimization: Only collect and process the minimum amount of personal information necessary to achieve specific purposes.
Data Security
- Establish a data security management system: Develop and implement comprehensive data security management systems in accordance with the requirements of the Cybersecurity Law and the Data Security Law to ensure the security of data during storage, transmission, and processing.
- Data encryption: Use strong encryption technology to protect data in storage and transmission, preventing unauthorized access and data leakage.
- Regular security assessments: Conduct regular data security risk assessments and vulnerability scans, promptly patch security vulnerabilities, and enhance system security.
Data Storage and Cross-Border Transmission
- Data localization: For important data related to national security and public interests, it should be stored domestically in accordance with data localization requirements. Therefore, before starting the project, conduct a feasibility assessment based on this requirement.
- Cross-border data transmission assessment: Before conducting cross-border data transmission, conduct a security assessment to ensure compliance with the Cybersecurity Law, Data Security Law, and relevant departmental regulations.
- Filing and approval: When necessary, file and obtain approval for cross-border data transmission to ensure legality and compliance.
3. Preventing Financial Crime Risks
Compliance with anti-money laundering and anti-terrorist financing regulations, enhancing platform security, preventing fraudulent activities, protecting user interests, and improving the platform's legitimacy and compliance to promote healthy and sustainable project development:
Implementing KYC (Know Your Customer)
- Identity verification: Require users to provide identity documents (such as ID cards, passports, etc.) and address proof for identity verification.
- Background checks: Check whether users have a criminal record or a history of involvement in illegal activities.
- Continuous monitoring: Regularly update and review user information to ensure data accuracy and timeliness.
Implementing KYT (Know Your Transaction)
- Transaction monitoring: Real-time monitoring and analysis of transaction behavior using advanced technology tools and algorithms to identify abnormal and suspicious transactions.
- Risk scoring: Assign risk scores to each transaction and conduct in-depth review and investigation of high-risk transactions.
- Reporting mechanism: Establish internal and external reporting mechanisms to promptly report and handle suspicious transactions, ensuring compliance with anti-money laundering and anti-terrorist financing requirements.
4. Preventing Illegal Fundraising, Fraud, and Other Criminal Risks
From the perspective of avoiding financial regulation and risk prevention, in China, it is not recommended for DePIN projects to directly target domestic individual end customers during the hardware device sales process. Attention should be paid to the following during the sales process:
- Equipment sales: Provide hardware devices (such as storage mining machines) to enterprise users (B-end customers) to ensure that the business model does not involve financial investment or financial products, avoiding the risk of illegal fundraising.
- Sales contracts: Sign standardized sales contracts, clearly defining the rights and obligations of both parties, including product descriptions, prices, payment methods, delivery times, and after-sales services.
- Product quality assurance: Provide high-quality hardware devices and ensure good after-sales service to enhance customer trust and satisfaction.
- Avoiding guaranteed returns: Clearly state during the sales process that hardware device sales do not include any guaranteed returns or investment returns to prevent customer misunderstandings.
- Risk warnings: Provide clear risk warnings, informing customers of the potential risks and uncertainties of purchasing hardware devices to ensure that customers understand and accept these risks.
免责声明:本文章仅代表作者个人观点,不代表本平台的立场和观点。本文章仅供信息分享,不构成对任何人的任何投资建议。用户与作者之间的任何争议,与本平台无关。如网页中刊载的文章或图片涉及侵权,请提供相关的权利证明和身份证明发送邮件到support@aicoin.com,本平台相关工作人员将会进行核查。



