WebAssembly runtime is the infrastructure for executing WebAssembly code, widely used as the execution engine for web browsers and blockchain systems.
Recently, Goplus's latest research results on vulnerability mining for WebAssembly virtual machines have been officially accepted for full presentation at ISSTA 2025!
ISSTA, as one of the top four conferences in the field of software engineering, is also recognized as an A-class international academic conference in the field of software engineering by the China Computer Federation (CCF), focusing on the latest cutting-edge advancements in software engineering and software testing from global research institutions and technology companies.

1. Problem Definition
WebAssembly runtime is the infrastructure for executing WebAssembly code, widely used as the execution engine for web browsers and blockchain systems. For example, Ethereum 2.0 and Polkadot have adopted WebAssembly runtime as the execution environment for smart contracts to enhance their efficiency and security. Despite the growing popularity of WebAssembly runtimes, they also introduce new attack surfaces. Flaws and defects in WebAssembly runtimes can lead to unexpected behaviors, erroneous results, and even severe security consequences, especially for blockchain platforms that rely on smart contracts compiled into WebAssembly bytecode.
2. Blockchain Smart Contract Virtual Machine Fuzzing Framework
For vulnerability mining in WebAssembly virtual machines, this paper designs a fuzzing framework called FreeWavm based on parse tree mutation and snapshot guidance.
FreeWavm consists of four key components.
(1) To capture the structured features of WebAssembly code, a WebAssembly module parser is developed to convert WebAssembly bytecode into a parse tree structure.
(2) Then, a structure-aware mutation module is designed to generate meaningful test inputs for the WebAssembly runtime. This involves using a custom node priority strategy to filter interesting nodes from the parse tree and then performing specific mutations on these nodes.
(3) To ensure the integrity of the mutated test inputs, an automatic repair mechanism is proposed to correct the mutated parse tree. This ensures that the module parser can successfully parse the newly generated test inputs, thereby ensuring the validity of continuous mutations.
(4) A snapshot pool is constructed to maintain unfinished parse tree structures that either trigger crashes or cover new execution paths in the target runtime, allowing previous knowledge to be used for subsequent mutations, thus increasing the probability of discovering deep vulnerabilities in the WebAssembly runtime.
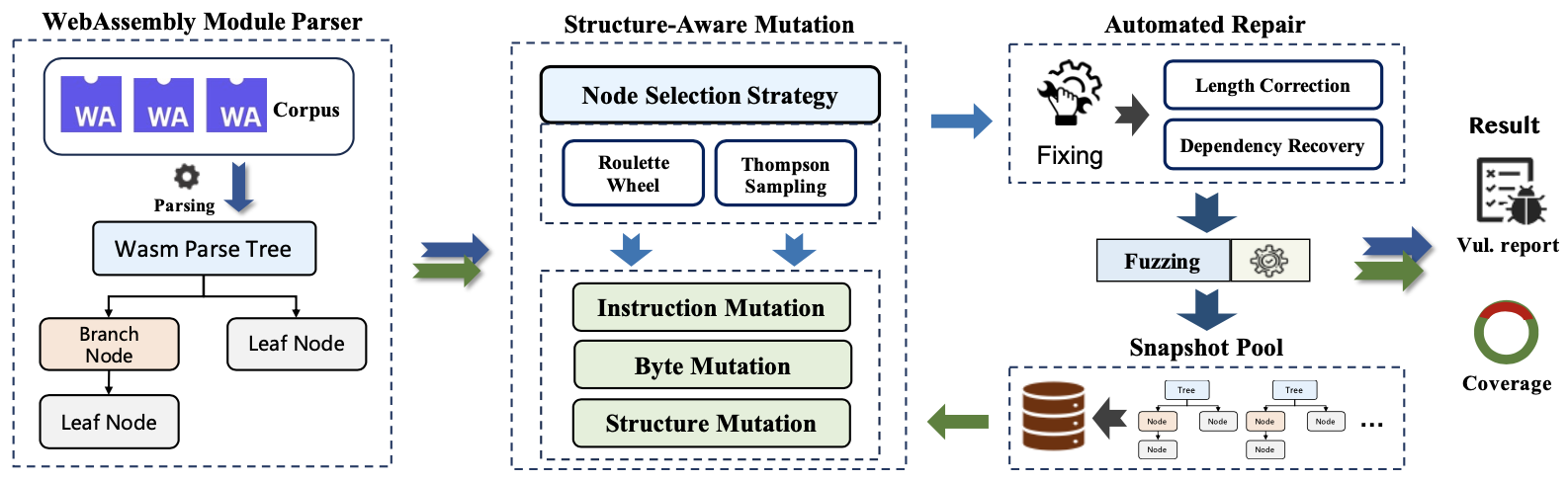
Overall Architecture of FreeWavm
Extensive experiments have been conducted on multiple WebAssembly virtual machines. FreeWavm has successfully discovered 69 new vulnerabilities, 24 of which have been assigned CVEs. In comparison, FreeWavm outperforms other similar products in terms of achieved code coverage and the number of vulnerabilities triggered during a 24-hour run.
免责声明:本文章仅代表作者个人观点,不代表本平台的立场和观点。本文章仅供信息分享,不构成对任何人的任何投资建议。用户与作者之间的任何争议,与本平台无关。如网页中刊载的文章或图片涉及侵权,请提供相关的权利证明和身份证明发送邮件到support@aicoin.com,本平台相关工作人员将会进行核查。



