In 2024, there were at least 47.16 billion data breaches reported globally throughout the year, a 354.3% increase from 10.38 billion in 2023. The most frightening aspect is that this trend is still growing and has not stagnated, which means that every piece of KYC-verified personal information is being repeatedly associated on the black market, leaving individuals completely exposed. This is no longer just a matter of frequently changing passwords; as privacy data runs rampant, once data breaches reach a certain level, it becomes impossible to trace which Internet Service Provider (ISP) was responsible for the leak. Consequently, the malicious criminal activities resulting from privacy leaks are becoming increasingly frequent worldwide, and even proactive data leakage crimes are difficult to trace. AML and KYC policies are useful but not ideal in their effectiveness. Innocent individuals have undergone KYC, while criminals remain at large. It is time to sound the alarm for global Internet users: who exactly do the current KYC and AML policies benefit? Who can we still trust? Is there any way for us to protect our identity and privacy?
1. Data breaches are the root cause of SIM swap attacks in the crypto space
The crypto market is always associated with telecom fraud, criminal networks, hacking attacks, and other illegal activities. Due to AML and KYC policies, the crypto market has indeed received sufficient protection; however, the opportunities for cybercriminals to succeed have not diminished, and the losses caused by leaked data in the crypto market continue to rise each year. In 2024, personal data from users of nine cryptocurrency exchanges was leaked, affecting over 500,000 customers and collecting a large amount of sensitive data, including: full usernames; credit card numbers; email addresses; IP addresses; and various authentication data. In December 2024, U.S. Bitcoin ATM operator Byte Federal disclosed a data breach incident where hackers exploited a GitLab vulnerability to infiltrate the system, leaking data from 58,000 customers. This is just a small incident of leaked data, but these leaks directly led to SIM swap attacks. The process is as follows:
(1) Target identification and information gathering: Attackers first identify their targets, usually choosing individuals who own cryptocurrencies, such as Vitalik Buterin and CZ, who have not escaped attacks. They gather personal information about the target, such as name, date of birth, ID number, phone number, and other KYC-required information, often by purchasing leaked data.
(2) Impersonating the victim to contact the carrier: After collecting sufficient information, attackers impersonate the victim to contact their mobile service provider. They may fabricate urgent or reasonable scenarios, such as claiming to have lost their phone, that their SIM card is damaged, or that they need to upgrade to a new device, in order to request the transfer of the victim's phone number to a new SIM card.
(3) Carrier's SIM swap operation: If the attacker successfully persuades the carrier's customer service representative, the carrier will associate the victim's phone number with the attacker's controlled new SIM card. At this point, the victim's original SIM card will be deactivated, and the attacker's new SIM card will take over that phone number.
(4) Receiving texts and calls: Once the attacker controls the victim's phone number, they can receive all texts and calls sent to that number, including verification codes used for two-factor authentication. This allows the attacker to bypass SMS 2FA, gain account access, and carry out further attacks and asset theft.
From this black industrial chain perspective, in a zero-trust network environment, KYC is necessary, but KYC data has also become a source of crime for criminals.
2. The means of proving oneself in the crypto world are so fragile, while the means of forgery are so convenient
In 2023, the collapse of the blockchain game Axie Infinity, once hailed as a poverty alleviation tool, shocked the world. At its peak, this "play-to-earn" game attracted over 2.7 million players in the Philippines (accounting for 40% of its global user base), who earned daily income through in-game tokens. However, when the value of the tokens plummeted, many found themselves unable to convert their digital assets into fiat currency due to the KYC requirements of centralized exchanges. This highlighted the paradox of Web3: the anonymity that empowers its utopian vision becomes its fatal weakness in the face of real-world compliance. This crisis exposed the core dilemma of Web3: anonymity grants freedom but sacrifices identity sovereignty; compliance requires verification but deprives privacy rights. Today, over 1 billion people globally lack traditional identity credentials, trapped outside the digital economy, as "proving you are you" still relies on phone numbers, ID cards, and bank accounts. With today's AI and large language model technologies, the cost of forging identities through facial recognition, voice, ID documents, etc., is extremely low. Technology has not effectively served to prove oneself and protect anonymity, but it can be maliciously exploited to seize sovereignty, which is the current state of identity verification supporting Web3—how ironic.
3. A new regulatory era of KYC and AML is about to emerge
It is well known that criminals use mixing tools like Tornado Cash to evade regulation and complete the money laundering process. Over the years, mixing has helped criminals launder money, and the real world has pointed fingers at Tornado Cash, leading to the arrest of its founder in 2022.
In 2024, over $2.2 billion in digital assets from the digital cryptocurrency industry were stolen by hackers. The Bybit hacking incident on February 21, 2025, saw hackers successfully steal digital assets worth over $1.5 billion, marking the largest theft in cryptocurrency history. Fortunately, Tornado Cash founder Alexey Pertsev had his pre-trial detention suspended by a Dutch court in February 2025. Although this is not true freedom, Ethereum co-founder Vitalik Buterin shared this news and expressed support. In March 2025, the U.S. Treasury removed Tornado Cash and several related digital wallet addresses from the OFAC Specially Designated Nationals (SDN) sanctions list, this ruling brings hope for the dawn of a KYC-free regulatory era. This ruling signifies a shift in the balance between privacy protection and government regulation. For individuals: the legal status of privacy rights is elevated, and the risks of using privacy tools are reduced. For governments: there is a need to seek a more refined balance between KYC requirements and technological neutrality, promoting the upgrade of regulatory tools. In the future, privacy protection may shift from "confronting regulation" to "compliance innovation," becoming a key period for the evolution of civil rights and national security in the digital age.
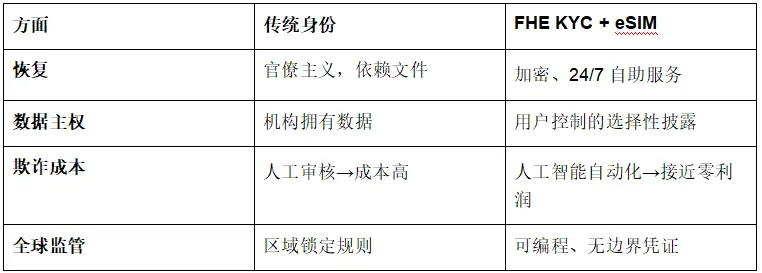
To commemorate this pivotal moment, the Privasea team has written this article in tribute to this moment, and we announce: KYC is not a means to protect crypto investors; the best way is to transform "your existence" into mathematically verifiable cryptographic objects. The original FHE KYC technology converts biometric features into immutable privacy protection credentials, anchored to the web2 world through anonymous identity devices (anonymous telecom SIM cards, anonymous credit cards, etc.), allowing personal information to become intangible; we are not just upgrading infrastructure—we are initiating a paradigm shift in digital identity sovereignty. We see the urgency of privacy protection, and Privasea will become a steadfast defender of privacy protection and autonomous identity.
4. FHE+KYC anonymous SIM cards will anchor digital identity to the web2 world
(1) FHE achieves the impossible in identity verification
User protection: Biometric information and documents remain end-to-end encrypted, eliminating the risk of leakage.
Compliance: Service providers use accurately matched plaintext methods to perform live checks, age verification, etc.
Regulatory balance: "Regulatory key sharding" allows for legal decryption in extreme cases (e.g., criminal investigations), balancing privacy and security.
(2) What is FHE
Fully Homomorphic Encryption (FHE) has long been regarded as the "crown jewel" of cryptography, solving a 30-year-old problem: performing computations on encrypted data without decrypting it.
Limitations of traditional encryption: Standard encryption (e.g., AES) protects static data. Any computation (e.g., identity checks) requires decryption, exposing the original data—this is the fundamental reason for the Facebook data breach.
Breakthrough of FHE: Imagine a locked safe (encrypted data). FHE allows external parties to classify, count, or perform complex operations on its contents without unlocking it. The data remains encrypted, but the results are verifiable.
(3) ImHuman: Redefining evidence of human existence
The innovation of ImHuman lies in transforming biometric verification into a cryptographic process executed entirely in an encrypted state:
Key sharding storage
Users generate client keys, which are divided into three segments through Shamir's secret sharing, stored locally, in the cloud, and on ImHuman servers. Retrieval requires two segments, eliminating single points of failure.
Active to NFT minting
An initial facial scan generates a 512-dimensional feature vector, encrypted with the client key and embedded into the ImHuman NFT. These NFTs do not store original biometric features but store homomorphically encrypted "cryptographic fingerprints."
Encrypted verification
During the verification process, a new facial scan generates a new vector. Privanetix nodes compute similarity scores entirely in encrypted form.
Dynamic threshold
If the similarity result exceeds a preset threshold, the decrypted similarity result will trigger a timestamped credential.
(4) FHE+KYC anonymous SIM cards will perfectly protect users' digital identities
Traditional SIM cards rely on centralized systems. eSIM + FHE KYC unlocks unprecedented possibilities:
Zero residual binding:
eSIM is bound to the ImHuman NFT credential rather than the original biometric information. Carriers can verify credentials without accessing phone numbers, ID cards, or facial data.
Loss recovery:
Lost your device? Recover through ImHuman:
Use two key segments to recover the client key.
Verify identity through encrypted checks.
No swap attacks:
Only the person holding their ImHuman NFT credential can reissue the original number, preventing any other means of changing the number's owner, thus avoiding SIM swap attacks.
Automatically issue new eSIM—no need for traditional KYC plaintext data or eKYC sensitive data.
(5) FHE+KYC anonymous SIM cards will anchor digital identity to the web2 world
With this anonymous SIM card, one can register for email services requiring a phone number, such as Gmail, Outlook, etc.; it can also be used to register for instant messaging tools like Telegram and WhatsApp; especially with a number that does not expose true identity and cannot be tampered with, it ensures the security of email, extending protection to many Internet services that only require email registration, such as social networking sites.
In some parts of the world, this anonymous SIM card can also facilitate local banking services, register for credit cards, etc.; it can also be used for payment and settlement services in countries like Nigeria.
In most Internet-developed countries, SIM cards serve as verification services, and with an anonymous SIM card, one can confidently register for 2FA verification services. The era of dedicated cards has arrived, and the underlying technology of FHE+KYC redefines digital identity sovereignty.
5. Why this is irreversible: Paradigm shift
People often think that cryptocurrency companies are similar to traditional financial services, and therefore the regulations they face are also similar to those of traditional financial services. The European Union has also confirmed that cryptocurrency exchanges should bear the same responsibilities as banks in maintaining the financial system. However, the U.S. Treasury's removal of Tornado Cash and several related digital wallet addresses from the OFAC Specially Designated Nationals (SDN) sanctions list indicates a shift in the new KYC and regulatory concepts involving cryptocurrency transactions. Cryptocurrency companies are not regulated like traditional financial services, and the charges against Tornado Cash founder Alexey Pertsev are all violations of anti-money laundering laws.
We are at a historic turning point: for the first time, humanity can secretly prove "I exist" using mathematical methods without relinquishing control over one's identity. This is the construction of a privacy layer that interoperates the crypto world with the real world, a great technological practice, and a battle to defend privacy rights. This is not just a technological leap but a milestone for digital human rights.
免责声明:本文章仅代表作者个人观点,不代表本平台的立场和观点。本文章仅供信息分享,不构成对任何人的任何投资建议。用户与作者之间的任何争议,与本平台无关。如网页中刊载的文章或图片涉及侵权,请提供相关的权利证明和身份证明发送邮件到support@aicoin.com,本平台相关工作人员将会进行核查。



