Recently, the cryptocurrency market has experienced a series of "bloodbaths," and after the meme coin craze subsided, Solana's price not only failed to rise but users have also flocked to social media to complain about being "sandwiched."
X user @btc_798 claimed that after buying the $GANG token on the Solana chain, the token's price skyrocketed 100 times, and he subsequently sold his position. However, due to the routing service choosing the liquidity-poor Raydium trading pool (only 100 SOL) instead of the better Orca pool (4000 SOL), the selling price was far below the market price, resulting in the trader earning about 1000 SOL less. "Even the anti-sandwich nodes of SOL have started to do evil." @PinkPunkBotCN also mentioned that there are suspicions that the recent sandwich phenomenon is due to nodes intentionally "scamming users."
GMGN co-founder @haze0x also specifically posted to remind everyone: "There is a problem with the MEV facilities on the SOL chain, and the sandwiches are becoming rampant."
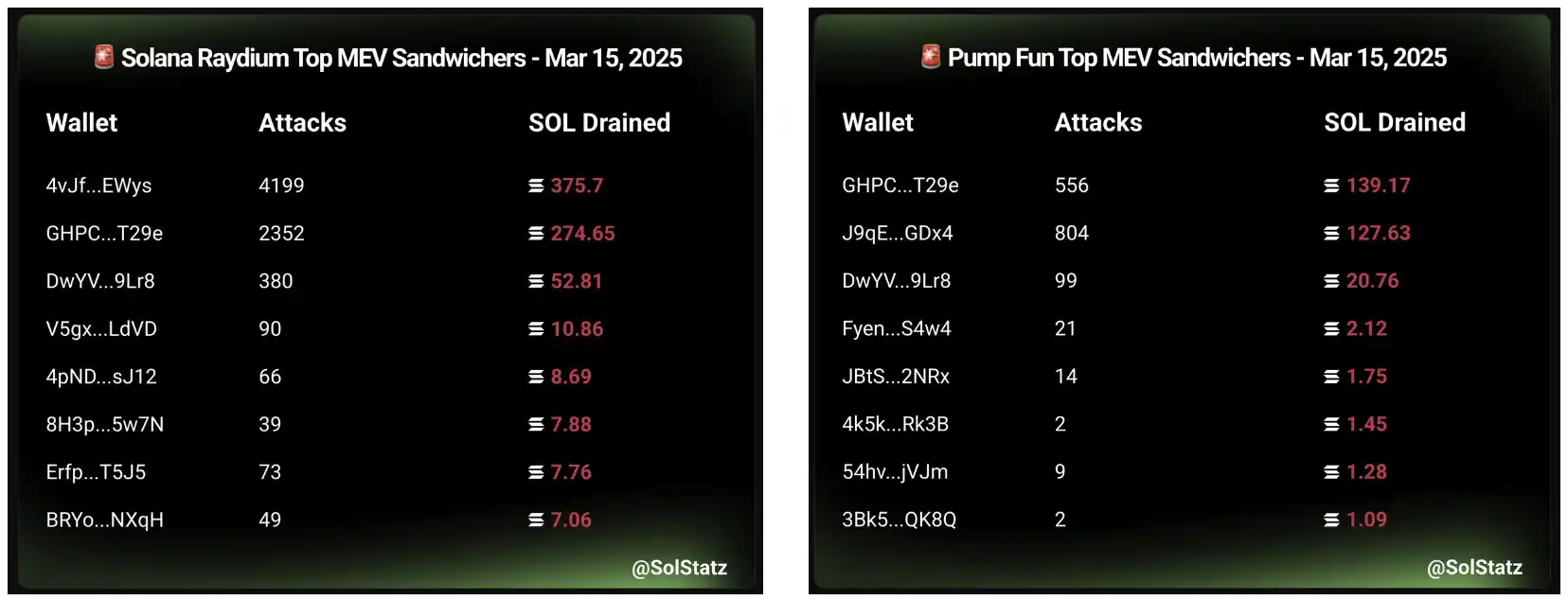
In response to these phenomena, crypto analyst @PepeBoost888 pointed out that some Jito validators have recently leaked data to sandwich attackers, allowing them to obtain anti-sandwich transaction data in advance. According to statistics from @solstatz, on March 15 alone, Raydium reported 10,633 attacks, resulting in a total loss of 916.63 SOL; Pump Fun reported 1,770 attacks, resulting in a total loss of 314.85 SOL.
Where is the problem?
In fact, being "sandwiched" is not a new occurrence on Solana. "Being sandwiched" refers to a sandwich attack, a common MEV (Maximum Extractable Value) strategy, and a widespread issue in the AMM market. In this type of attack, bots detect a transaction before it is bundled into a block, then execute a buy order ahead of the transaction, pushing the price up; after the transaction is completed, they immediately place a sell order to profit from the price difference. This forces users to buy tokens at a higher price, while the bots easily profit. Although MEV is not inherently without value, as it can prevent spam attacks through mechanisms like priority fees, it helps maintain the stability of the blockchain network. However, Solana seems to have left vulnerabilities for sandwich attacks due to its mechanism issues.
MEV on Solana was initially inconspicuous until Jito launched its MEV reward protocol, which brought it to the forefront. Now, over 66% of validators have adopted the Jito-Solana client, allowing users to pay "tips" to prioritize their transactions, while Jito also operates a mempool, which has allowed sandwich attackers to listen in on user transactions. Although Jito attempted to close the mempool in March 2024 to reduce such attacks, MEV bots can still listen to transactions by running RPC nodes, and the attacks have not ceased.
In June 2024, Tim Garcia, head of validator relations at the Solana Foundation, announced on Discord that they would take strong measures to eliminate over 30 validator nodes participating in sandwich attacks in an attempt to curb the issue, but this action did not completely resolve the frequent attacks. For example, the notorious "arsc" bot made over $30 million in profit within two months and continued to earn substantial profits through sandwich attacks even after the foundation's actions. Attackers quickly adapted to the network changes, possibly bypassing restrictions by running their own RPC nodes, continuing to listen in on and front-run user transactions.
Related: "Making $30 million in 2 months, why do sandwich attacks on Solana persist?"
Today, sandwich attacks remain a persistent issue on Solana. Users generally report that even when paying tips, they cannot completely avoid being "sandwiched." This is highly reminiscent of past situations, where attackers exploit Solana's high transaction processing speed and relatively predictable transaction ordering to continuously target transactions.
What is different from being "sandwiched" on Ethereum?
In fact, the phenomenon of being "sandwiched" is not rare in the blockchain world, as Ethereum also suffers from sandwich attacks. The reason sandwich attacks on Solana have become a persistent issue is closely related to its network design and operational mechanisms, which differ significantly from those of Ethereum.
On Ethereum, the source of MEV is mainly related to the visibility of unprocessed transactions. Due to the existence of a shared mempool, anyone can see the transaction information waiting to be added to the blockchain. It's like knowing in advance which goods are about to be snatched up in a public market. Thus, savvy traders can leverage this "foresight" to profit through arbitrage or reordering transactions, and attackers can spend extra gas fees to take precedence in transaction ordering, using fee competition to execute attacks.
In contrast, Solana does not have a mempool, meaning that information about unprocessed transactions is not as publicly available as it is on Ethereum, making it more difficult to obtain this information. However, opportunities still exist for validators. Validators are responsible for processing a round of transactions and can clearly see which transactions have not yet been bundled onto the blockchain. At this point, validators hold a hidden "trump card": they can quietly execute "sandwich attacks" like players on Ethereum and profit from them. But this advantage is private, known only to the "malicious" validators themselves, while other validators remain unaware.
In terms of countering sandwich attacks, the effectiveness of measures taken by Ethereum and Solana differs significantly. Ethereum has outsourced transaction ordering to professional builders through the MEV-Boost system, limiting validators' ability to manipulate transaction order, effectively reducing the occurrence of attacks. In contrast, while Solana's Jito system attempts a similar mechanism, attackers can still exploit loopholes by using private nodes to bypass restrictions. It can be said that Ethereum's MEV-Boost successfully constrains validator behavior, while Solana's Jito system appears somewhat powerless in curbing attacks.
Additionally, the network structure of Solana and Ethereum also determines the difficulty of prevention. Solana has only about 2,000 validators, leading to relatively centralized power, where a few malicious nodes can influence transaction ordering, providing opportunities for attackers. In contrast, Ethereum has over 500,000 validators, with a highly decentralized network, making it difficult for attackers to control enough nodes to execute attacks, serving as a natural barrier to such activities.
Related: "Talking to Solana nodes: Who is quietly profiting from memecoins?"
In summary, Solana is fast but centralized, and attackers exploit private nodes, while the Jito system fails to stop them. Ethereum relies on fee competition and MEV-Boost, along with a decentralized structure, to provide better prevention. For Solana to solve the problem, it needs to optimize its mechanisms and decentralize power.
How to avoid being "sandwiched"?
Before changes are made to Solana's mechanisms, it is crucial for users to understand how to effectively prevent sandwich attacks in their transactions.
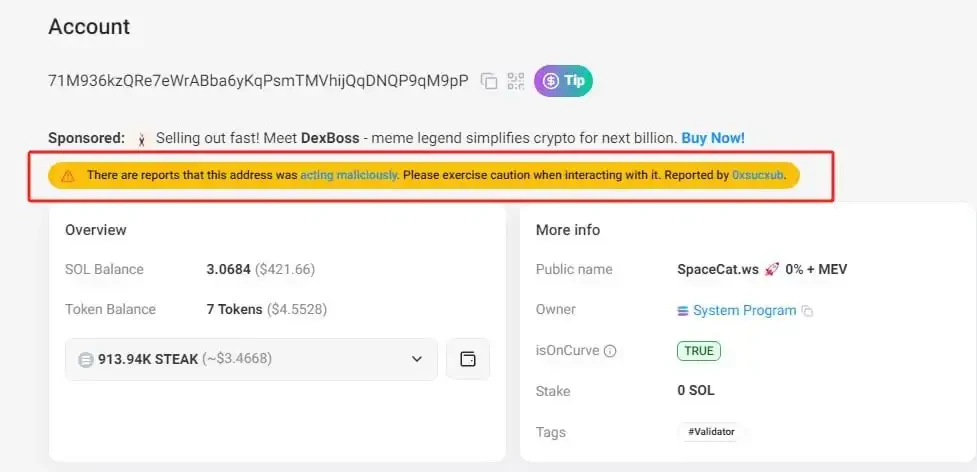
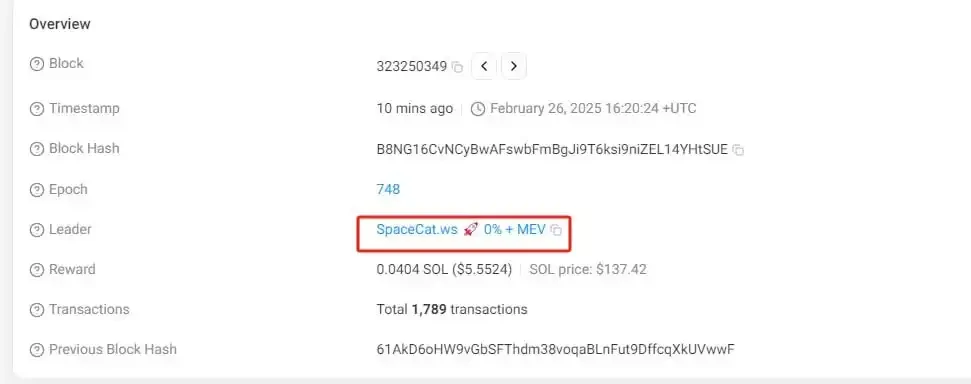
Crypto analyst @PepeBoost888 suggests that to determine whether their transaction was packaged by malicious validators leading to a sandwich attack, users can verify in the following way: first, click on the corresponding transaction's block number in the Solscan blockchain explorer, then find the "Leader" field on the block details page to check the validator node responsible for packaging that block. Currently, some malicious validators have been reported by the community and marked with risk warnings on the Solscan platform. Users can also cross-reference the validator address with the publicly maintained list of malicious nodes by @0xsucxub to confirm risks.
For P players, the primary principle when trading on-chain is to avoid setting too high slippage. It is recommended to rationally set a reasonable slippage range of 0.5%-1% based on market volatility. If using AMM for trading, users should actively enable anti-MEV protection features, which can significantly reduce the likelihood of their transactions being monitored and attacked by malicious nodes through techniques like obfuscating transaction paths and delaying broadcasts.
Related: "GMGN co-founder teaches you how to be a qualified P player"
The phenomenon of being "sandwiched" has once again sounded the alarm for the Solana ecosystem. This is not a problem unique to Solana but rather a growing pain that public chains generally encounter. However, if being "sandwiched" becomes the norm, Solana's reputation may be affected. After all, it has always been hailed as the "Ethereum killer," relying on high-speed performance and user experience. If users feel that this highway is plagued by various issues like toll fees, packaging fees, and protection fees, who would still be willing to use it? Especially in critical areas like DeFi, trust is the highest cost.
免责声明:本文章仅代表作者个人观点,不代表本平台的立场和观点。本文章仅供信息分享,不构成对任何人的任何投资建议。用户与作者之间的任何争议,与本平台无关。如网页中刊载的文章或图片涉及侵权,请提供相关的权利证明和身份证明发送邮件到support@aicoin.com,本平台相关工作人员将会进行核查。




