Original Title: Crypto trader gets sandwich attacked in stablecoin swap, loses $215K
Original Author: Brayden Lindrea, Cointelegraph Author
Original Translation: ChatGPT
Editor's Note: This article reports on a sandwich attack incident that occurred in cryptocurrency trading, where a trader lost over $215,000 during a stablecoin swap. The article details the process of the attack, including how MEV bots profited from front-running trades, and explores potential money laundering activities. It also mentions the protective measures taken by the Uniswap platform to prevent such attacks and clarifies initial criticisms.
The following is the original content (reorganized for readability):
On March 12, a crypto trader became a victim of a sandwich attack while executing a $220,764 stablecoin transfer, nearly losing 98% of its value, amounting to $215,000, which was captured by MEV bots.
The $220,764 USDC stablecoin was exchanged for $5,271 worth of Tether USDT in just 8 seconds, as the MEV bot successfully front-ran the trade, profiting over $215,500.
Data from the Ethereum block explorer shows that this MEV attack occurred in the USDC-USDT liquidity pool on the decentralized exchange Uniswap v3, which locked assets worth $19.8 million.
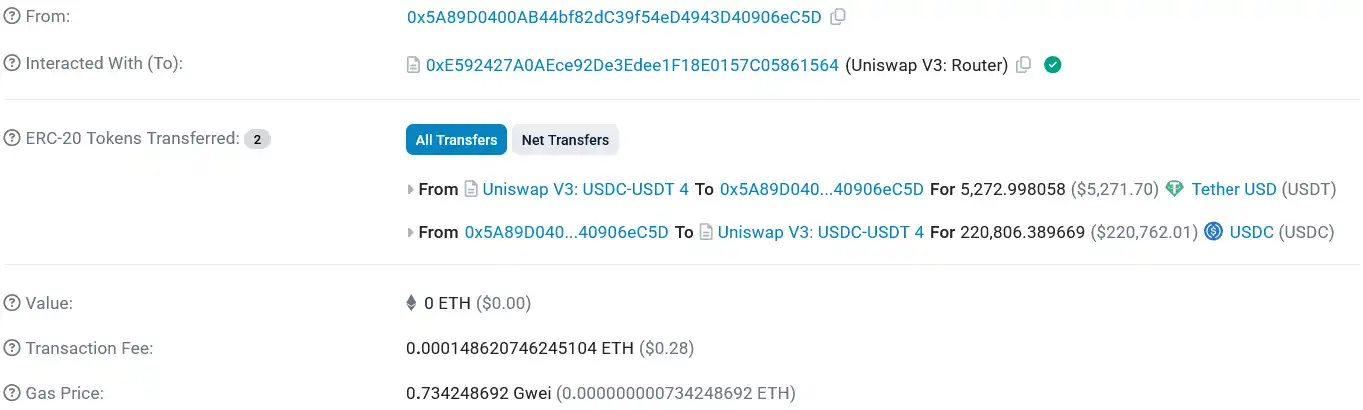
Details of the sandwich attack transaction Source: Etherscan
According to Michael Nadeau, founder of The DeFi Report, the MEV bot front-ran the trade by withdrawing all USDC liquidity from Uniswap v3's USDC-USDT pool and then putting it back after the trade was executed.
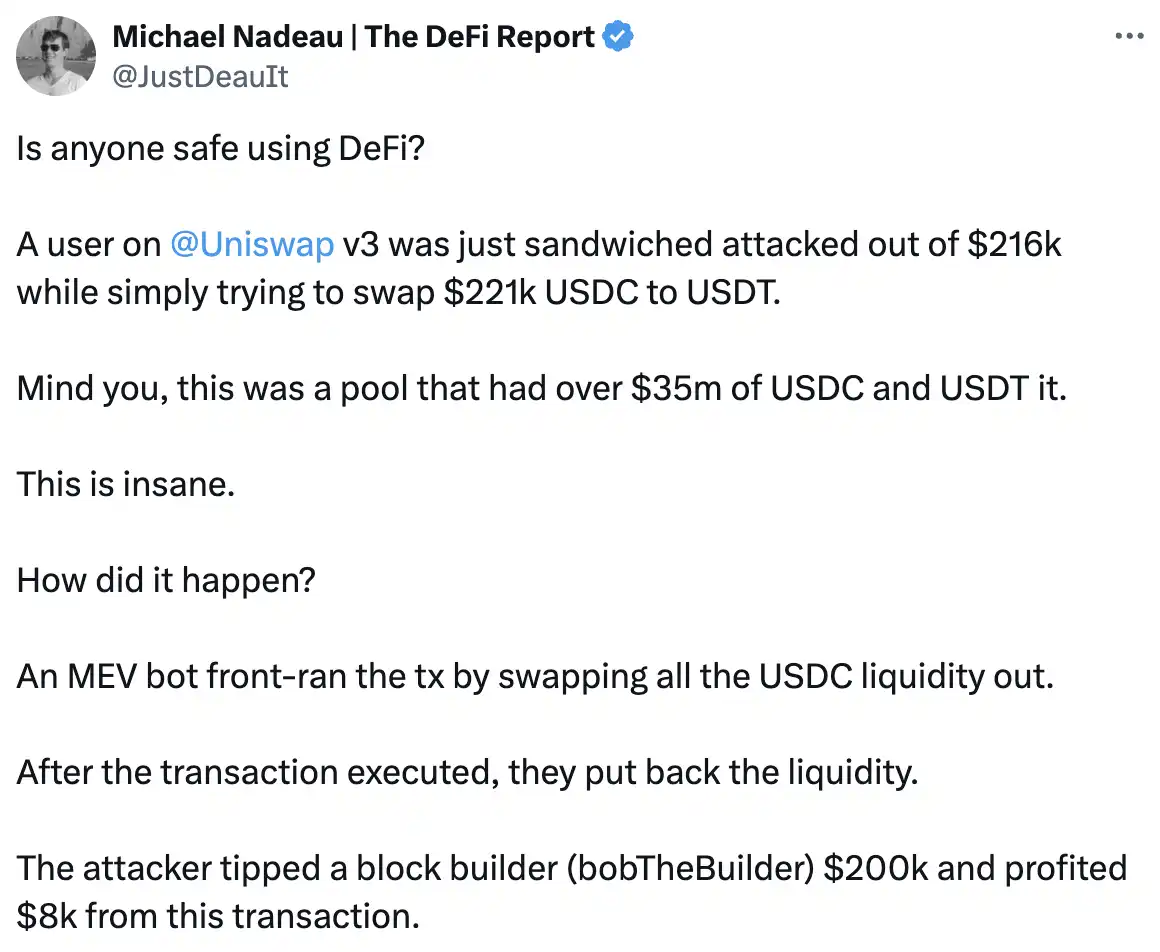
Nadeau stated that the attacker paid a $200,000 tip to Ethereum block builder "bob-the-builder.eth" from the $220,764 trade and profited $8,000 themselves.
DeFi researcher "DeFiac" speculated that the same trader using different wallets may have encountered a total of six sandwich attacks, citing "internal tools" as evidence. They noted that all funds came from the lending protocol Aave before being deposited into Uniswap.

Two of the wallets became victims of the MEV bot sandwich attack around 9 AM UTC on March 12. The Ethereum wallet addresses "0xDDe…42a6D" and "0x999…1D215" were sandwich attacked in trades that occurred three to four minutes prior, losing $138,838 and $128,003, respectively.
These two traders executed the same swap as the trader who made the $220,762 transfer in the Uniswap v3 liquidity pool.
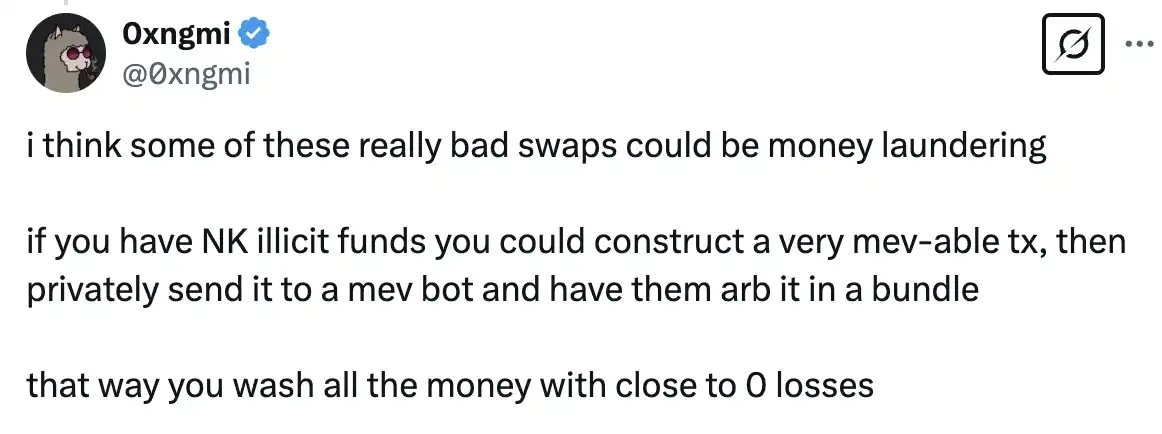
There is speculation that these trades may be related to money laundering.
0xngmi, founder of the crypto data dashboard DefiLlama, stated: "If you have NK illegal funds, you can construct a trade that is very easily susceptible to MEV attacks, then privately send it to an MEV bot and have them arbitrage it in a bundle. This way, you can wash all the money with almost zero loss."
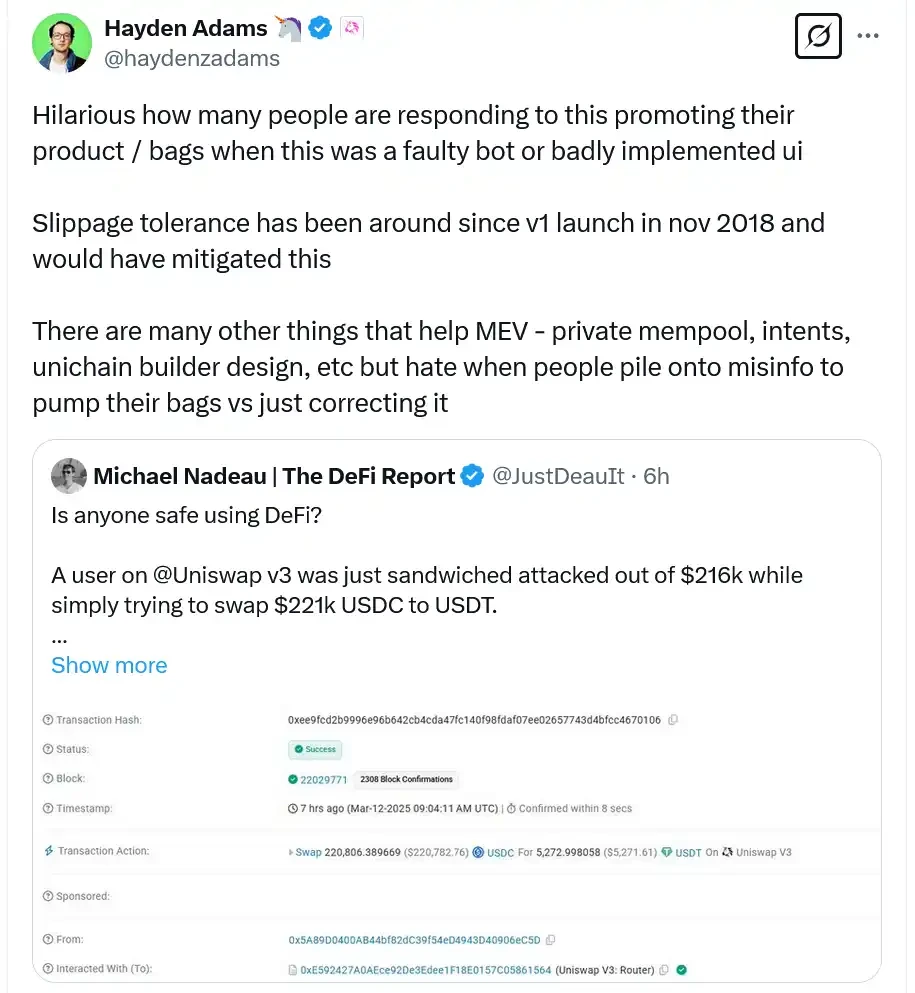
Although Nadeau initially criticized Uniswap, he later acknowledged that these trades did not originate from Uniswap's front end, which has MEV protection and default slippage settings.
After Uniswap CEO Hayden Adams and others clarified the protective measures taken by Uniswap to prevent sandwich attacks, Nadeau retracted his criticisms.
免责声明:本文章仅代表作者个人观点,不代表本平台的立场和观点。本文章仅供信息分享,不构成对任何人的任何投资建议。用户与作者之间的任何争议,与本平台无关。如网页中刊载的文章或图片涉及侵权,请提供相关的权利证明和身份证明发送邮件到support@aicoin.com,本平台相关工作人员将会进行核查。




