1. The Harm of Hackers to the Cryptocurrency Market Has Never Stopped
The largest amount stolen by hackers in the history of the cryptocurrency world belongs to the "Mt. Gox" incident, which lost 850,000 BTC in 2014 (approximately $85 billion at current prices). Since 2017, the total amount of cryptocurrency assets stolen by hackers has exceeded $10 billion. The recent loss of $1.4 billion by Bybit has become the largest hacking incident in recent years.
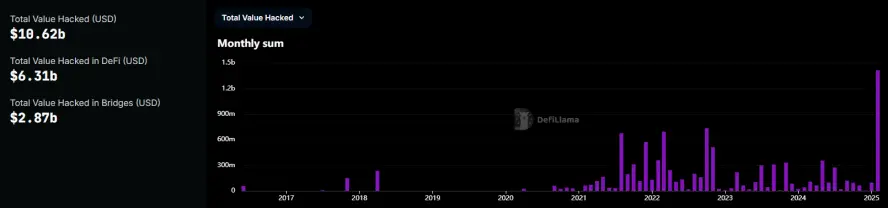
Amount stolen by hackers from 2017 to present (monthly)
Data source: https://defillama.com/hacks
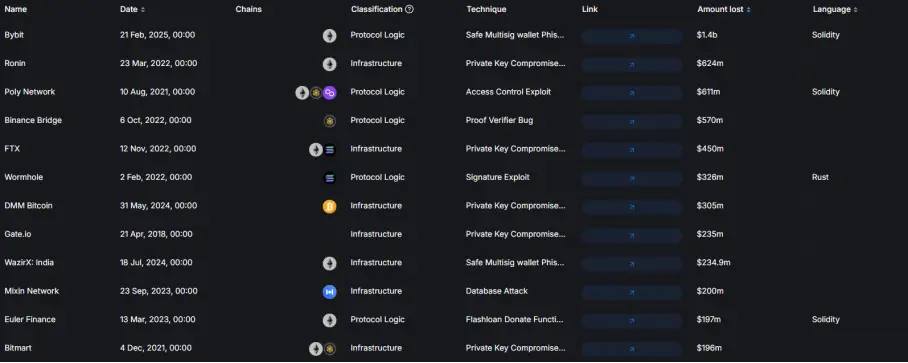
Large projects with amounts stolen by hackers from 2017 to present
Data source: https://defillama.com/hacks
2. Full Chain Infrastructure Can Effectively Reduce the Risk of Being Hacked
Web3 urgently needs more secure and convenient liquidity infrastructure. The recent hacking incident originated from the asset rebalancing between the exchange's cold wallet and hot wallet. For exchanges and some liquidity protocols, asset rebalancing is a routine operation. The purpose of this operation is to ensure asset security and improve asset utilization efficiency. Similar to traditional banks adjusting the total amount of savings and lending funds based on the reserve requirement ratio, in the exchange scenario, if the amount of ETH users deposit and withdraw from the exchange is roughly the same, the amount of ETH in the exchange will remain stable. However, if users withdraw significantly more ETH than they deposit in a short period, the amount of ETH in the exchange's hot wallet will decrease, and the exchange will need to transfer ETH from the cold wallet to the hot wallet to ensure there is enough ETH for users to withdraw. For example, if a bank branch has too much cash withdrawn, the head office needs to transport cash from the vault to that branch to avoid users being unable to withdraw money. Conversely, if a bank branch has too much cash, the head office will return the excess cash to the bank vault for security reasons. It is easy to understand that this is a very routine business; in addition to exchanges, cross-chain bridges and multi-chain applications often need to perform asset rebalancing. Therefore, secure and convenient liquidity infrastructure is extremely important.
Smart contracts control asset rebalancing. Both exchanges and cross-chain bridges can fully utilize smart contracts to achieve asset rebalancing. The total amount of liquidity pools is fixed, and when the assets in a certain pool (hot wallet, on-chain liquidity) drop below a certain threshold, the smart contract can automatically complete the liquidity rebalancing operation. Of course, this may still involve cross-chain bridges and centralized risks. A reward mechanism can be introduced to make the rebalancing operation more decentralized and secure. For example, when a certain asset pool drops to 20% of its original amount, the smart contract can initiate an on-chain task, and any user who adds liquidity to this pool can receive a reward. This way, many users or bots will automatically balance liquidity for the reward. This model can "outsource" the liquidity rebalancing business to third parties and "break it down into smaller parts," significantly reducing asset risk.
Full chain asset settlement will leave hackers with nothing to steal. Of course, relying solely on third parties to balance liquidity essentially just transfers the risk of being attacked. For example, in the past, banks transported funds themselves, but now they hire third-party security companies to transport funds with armored vehicles. Although this is more professional, it can still be robbed. So, is it possible to make it so that hackers can't steal any money? The answer is yes. This can be achieved through a complete chain settlement currency system. The current interbank credit settlement system adopts such a model. Interbank transmission is no longer in cash; what hackers steal is just an encrypted certificate, not assets. Without the user's signature authorization, they still cannot withdraw. For users, when one bank is short on cash, they can withdraw from another bank.
3. AI Agent + Full Chain Infrastructure Can Avoid Being "Scammed"
From the live broadcast after the Bybit incident, it was learned that Ben Zhou had conducted a strict review of the multi-signature content and checked it twice before the final multi-signature. Unfortunately, humans can only check the front-end displayed content, and there were no abnormalities shown on the front-end interface during the entire transaction process. Therefore, even the most cautious person can be deceived by the "facts in front of them."
But what if it is handed over to a robot? An AI Agent can directly analyze smart contract code or on-chain transaction data, and it can quickly identify anomalies by comparing back-end and on-chain data in detail.
This is not to suggest developing an AI Agent with a checking function specifically for risk alerts; after all, as long as humans are responsible for the final execution, there is still a possibility of being scammed. Today, we can completely entrust the AI Agent with the responsibility of checking and executing.
4. The Full Chain Asset Infrastructure Built by PicWe Can Reduce the Risk of Being Hacked
Currently deployed on Movement, PicWe has already achieved the following functions through its full chain asset infrastructure:
1. Smart contracts control asset rebalancing
2. Full chain asset settlement (WEUSD)
3. Empowering AI Agents with on-chain execution layers
From its inception, PicWe aims to better serve the Web3 world with fully decentralized full chain assets. It not only enhances the efficiency of full chain liquidity, allowing users across various chains and ecosystems to access simple, efficient, and low-cost liquidity services, but also enables AI Agents to execute on-chain operations, avoiding the difficulties of human learning and interacting with blockchain. At the same time, when AI Agents use full chain assets to provide liquidity services to users, it can greatly reduce the occurrence of similar hacking incidents.
免责声明:本文章仅代表作者个人观点,不代表本平台的立场和观点。本文章仅供信息分享,不构成对任何人的任何投资建议。用户与作者之间的任何争议,与本平台无关。如网页中刊载的文章或图片涉及侵权,请提供相关的权利证明和身份证明发送邮件到support@aicoin.com,本平台相关工作人员将会进行核查。




