Tear Drop attacks utilize a method of reassembling fragmented data packets by sending overlapping fragments during transmission, causing the target system to fail to reconstruct these fragments correctly, resulting in a denial of service.
Written by: Onkar Singh, CoinTelegraph
Translated by: Deng Tong, Jinse Finance
1. What is a Tear Drop Attack in Cryptocurrency?
Tear Drop attacks utilize a method of reassembling fragmented data packets by sending overlapping fragments during transmission, causing the target system to fail to reconstruct these fragments correctly, resulting in a denial of service.
As the cryptocurrency ecosystem matures, the network threats targeting it have become increasingly complex. Tear Drop attacks are a type of Denial of Service (DoS) attack and are one of such network attacks. Originally a network-level vulnerability, their adaptation to cryptocurrency systems highlights the ingenuity and versatility of malicious actors.
Imagine cutting a letter into several parts and placing them in different envelopes. Someone at the destination reassembles the fragments to read the entire letter. A Tear Drop attack is like sending envelopes with missing or overlapping parts, making it impossible to recreate the original letter. Due to this confusion, the recipient may become overwhelmed and shut down.
But what does this have to do with cryptocurrency?
Cryptocurrency systems heavily rely on network communication. Transactions, block propagation, and other essential functions involve sending data in packet form over the internet. These packets are reassembled by nodes that maintain the blockchain and process transactions.
Tear Drop attacks targeting specific nodes or network participants attempt to disrupt normal operations to exploit vulnerabilities in wallets, exchanges, or blockchain networks. For example, by sending malformed packets, attackers can overwhelm the server's reassembly process, causing it to crash or become unresponsive.
If a Tear Drop attack is effective, it may open the door for other attacks. For instance, when a server is unavailable or unable to reassemble packets, attackers may attempt to exploit other vulnerabilities to gain unauthorized access or alter data.
Therefore, understanding and addressing the consequences of such attacks is crucial, as they have the potential to undermine the integrity of blockchain networks.
2. How Tear Drop Attacks Target Crypto Networks
In the cryptocurrency environment, Tear Drop attacks often target the decentralized nature of blockchain platforms. Even if they do not target the cryptographic algorithms of the blockchain, compromising the underlying peer-to-peer network infrastructure that cryptocurrencies rely on can lead to service disruptions, financial losses, and decreased user trust.
Attackers can disrupt consensus processes, transaction validation, or node-to-node communication by focusing on specific nodes or servers. This can lead to network fragmentation, processing delays, or even complete shutdowns.
For example, attackers may overwhelm key nodes in a permissionless blockchain (like Bitcoin) or validation nodes in a permissioned blockchain with erroneous packets, rendering them inoperable. Since nodes rely on regular communication to reach consensus, these disruptions can create vulnerabilities that attackers can exploit.
For instance, if certain nodes temporarily disconnect or become inoperable, attackers may attempt to manipulate data flows, triggering double-spending attacks or introducing erroneous transactions.
Additionally, Tear Drop attacks can target services associated with the blockchain ecosystem, such as wallet providers and cryptocurrency exchanges, rather than the blockchain infrastructure itself. These services primarily rely on continuous communication between users and servers to facilitate seamless transactions and service availability.
Tear Drop attacks on exchanges can disrupt trading, withdrawals, and other critical services. In addition to negatively impacting specific users, this can damage the exchange's reputation and potentially lead to losses for traders and investors. Furthermore, frequent attacks or prolonged outages may cause users to lose confidence in the platform, harming its user base.
3. The Impact of Tear Drop Attacks on Crypto Security and Users
Tear Drop attacks have profound implications for cryptocurrency systems. They not only jeopardize network security but also undermine user trust.
Key impacts include:
Operational Downtime: Network participants (such as nodes or validating entities) may experience interruptions, halting transaction processing.
Financial Losses: Traders and investors may suffer financial losses due to transaction delays or failures, especially during market volatility.
Data Integrity Risks: While Tear Drop attacks do not directly modify blockchain data, they may create opportunities for secondary attacks targeting ledger integrity.
Reputation Damage: Cryptocurrency networks, exchanges, or wallet providers may suffer from prolonged outages or repeated attacks.
Exploitation Windows: Attackers can exploit network disruptions to distract system administrators, enabling further attacks such as phishing or double spending.
4. How to Identify Tear Drop Attacks
To minimize the harm caused by Tear Drop attacks, early detection is essential. If system administrators can recognize the signs of risk, they can act more swiftly.
Here are the main signs of a Tear Drop attack:
Unexplained System Crashes: Unexpected frequent crashes may indicate that the system is under attack, targeting its ability to reassemble fragmented data packets.
Performance Degradation: Slower processing times or decreased responsiveness of nodes or servers may indicate an influx of malformed packets overwhelming the system.
Error Logs: A careful examination of system logs may reveal patterns of overlapping or incomplete packets, which are typical characteristics of Tear Drop attacks.
Abnormal Network Traffic: A sudden spike in fragmented packet traffic usually indicates a Tear Drop attack. Monitoring tools can help identify abnormal trends.
Connectivity Issues: If nodes in the network cannot communicate with each other, it may be a sign that the blockchain architecture is under attack.
5. Best Practices to Prevent Tear Drop Attacks in Cryptocurrency
A proactive strategy that combines operational focus and technical safeguards is needed to prevent Tear Drop attacks.
Packet filtering is often used in traditional networks to block disruptive attacks like DoS, which aim to overload the network with malicious data.
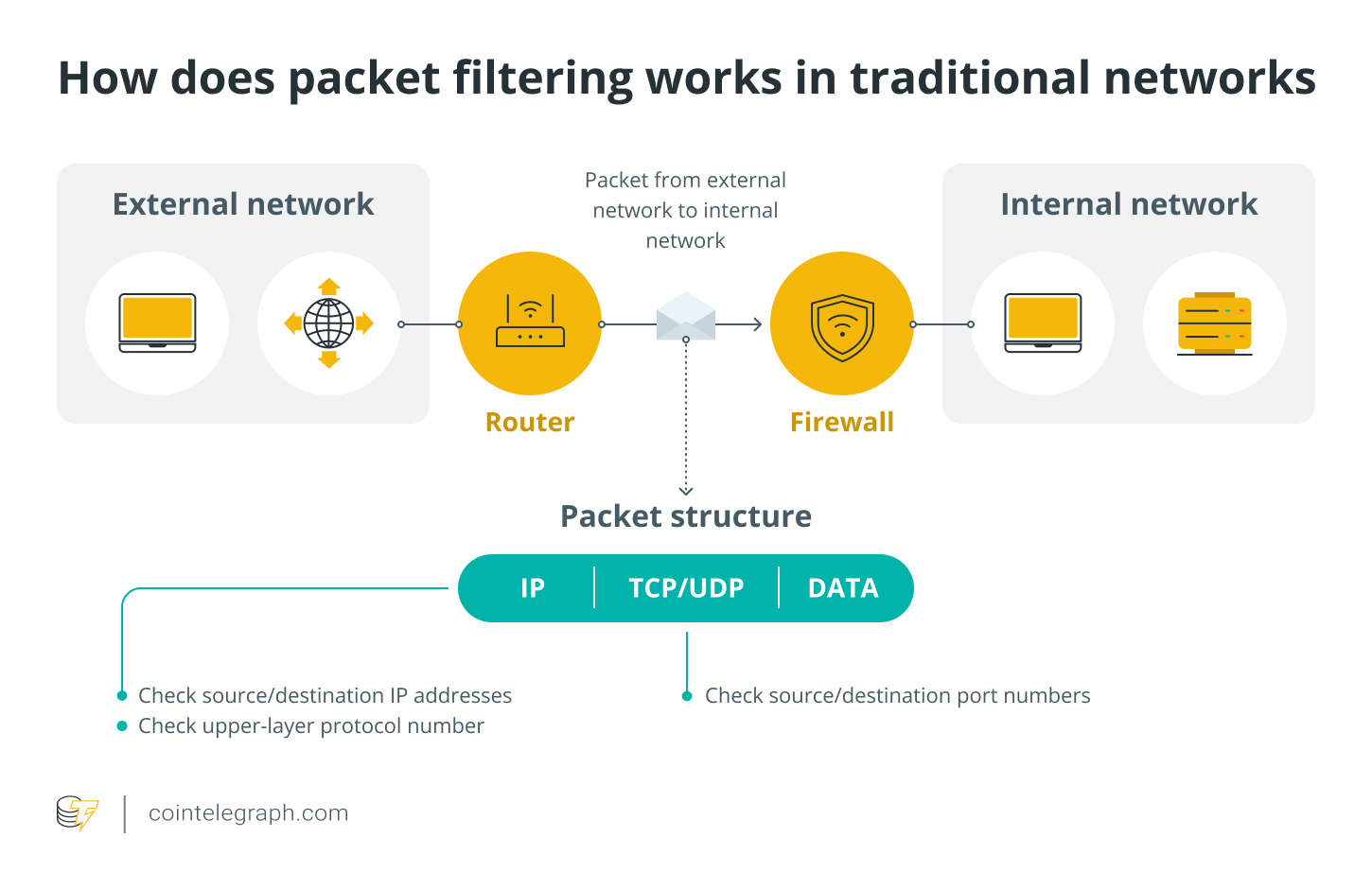
In simple terms, packet filtering acts as a security checkpoint for data transmitted over the network. Just as airport security personnel scan your luggage for dangerous items, packet filtering scans incoming packets to ensure they are safe.
In blockchain systems, it helps prevent malicious or faulty packets (such as those used in Tear Drop attacks) from entering network nodes.
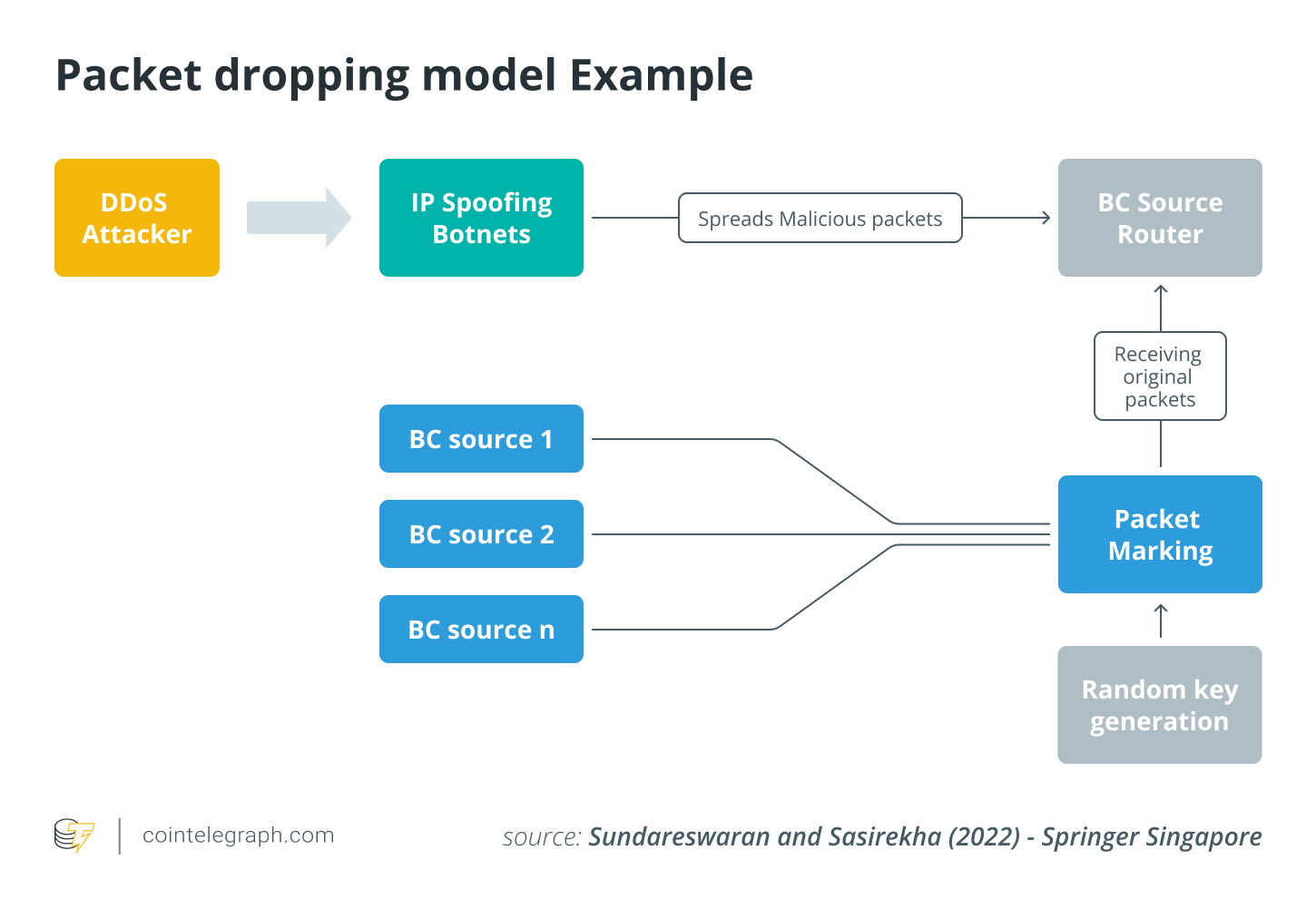
Here are some additional best practices to consider:
Resilience of Decentralized Architecture: Strengthen decentralized blockchain nodes to ensure redundancy and fallback mechanisms, allowing the network to operate normally even if certain nodes are attacked.
Rate Limiting and Traffic Shaping: Control the rate at which packets are transmitted to nodes to reduce the impact of flood attacks.
Regular Software Updates: Ensure that all blockchain software, wallets, and trading platforms are updated to patch known vulnerabilities.
Educate and Train Staff: Equip the team with knowledge to effectively identify and mitigate potential threats.
Combined with other defense technologies, packet filtering can provide a robust layer of protection, helping to ensure cryptocurrency systems are safeguarded against evolving threats.
6. What to Do If You Become a Victim of a Cryptocurrency Tear Drop Attack
Even with the strongest defenses, no system can be completely immune to network attacks. Timely action can mitigate the impact of a Tear Drop attack on your cryptocurrency system.
If you become a victim of a Tear Drop attack, you can take the following measures:
Isolate Affected Systems: To prevent the attack from spreading, disconnect the compromised nodes from the network.
Analyze and Mitigate: Companies can use forensic tools and detailed logs to investigate the nature of the attack. Apply necessary updates or patches to address the exploited vulnerabilities.
Hire an Incident Response Team: Leverage the expertise of cybersecurity professionals to help contain and recover from the attack.
Notify Stakeholders: Clearly explain the issue to consumers and relevant parties. Regular updates and transparency help maintain trust.
Strengthen Defenses: After the attack, assess the security architecture of the system and take preventive measures to avoid recurrence. Conduct penetration testing (simulated attacks to identify weaknesses) to find more vulnerabilities.
Document the Incident: Keep detailed records of the attack and response. This knowledge can be very helpful for future compliance and preparedness.
As can be seen, Tear Drop attacks highlight the vulnerabilities of cryptocurrency systems in the face of complex network threats. By taking swift action and strengthening security measures, you can mitigate the impact and protect your network from future disruptions.
免责声明:本文章仅代表作者个人观点,不代表本平台的立场和观点。本文章仅供信息分享,不构成对任何人的任何投资建议。用户与作者之间的任何争议,与本平台无关。如网页中刊载的文章或图片涉及侵权,请提供相关的权利证明和身份证明发送邮件到support@aicoin.com,本平台相关工作人员将会进行核查。



