From the release of ZK compression to the future launch of various system calls, the importance of ZK in Solana cannot be underestimated.
Written by: Yash Agarwal & 0xIchigo
Compiled & Organized by: Pzai, Foresight News
Broadly speaking, Solana's infrastructure helps developers save costs on network performance, provides asynchronous execution and state growth solutions; in terms of security, Solana offers privacy and confidentiality for on-chain applications, as well as verifiability and decentralized proof networks. Let's explore more of these aspects one by one.
Privacy and Verifiability
Arcium helps achieve privacy for on-chain applications by providing a trustless, verifiable, and efficient framework for running cryptographic computations. For example, AI models can be trained on private data, while DeFi can use it for private transactions.
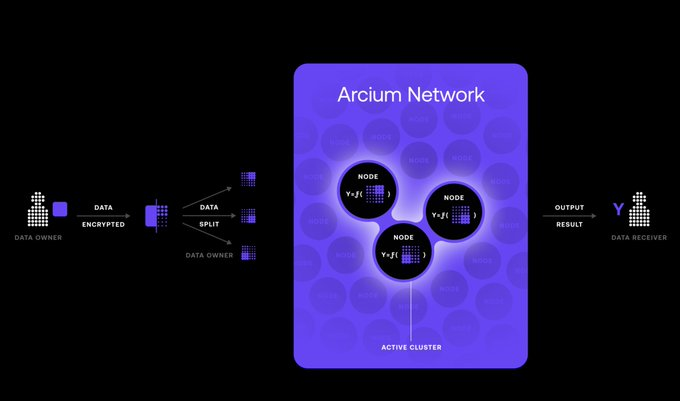
Anagram's Bonsol is Solana's native verifiable computing system, enabling developers to create fully verifiable executables for private and public data, mathematically guaranteeing their validity, and integrating the results into Solana smart contracts for on-chain proof.
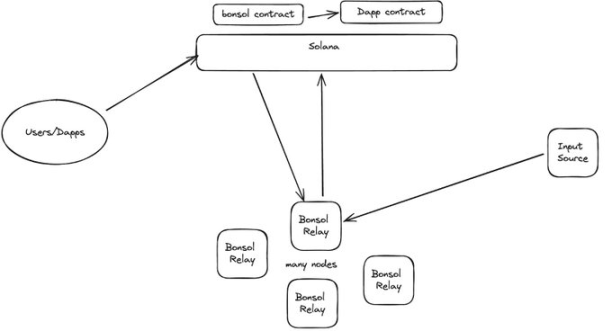
Anonymity and ZK-based Scalability
Darklake has built a privacy AMM trading application aimed at becoming Solana's first DEX that offers real-time, MEV-resistant order execution.
Dark Protocol has developed a market-governed anonymous protocol powered by ZK-SNARKS.
ZK Compression, developed by the ZK proof protocol LightProtocol and Helius, is a new Solana account primitive that features zk proofs and state compression mechanisms, reducing the rent costs for Solana application developers and providing state growth solutions.
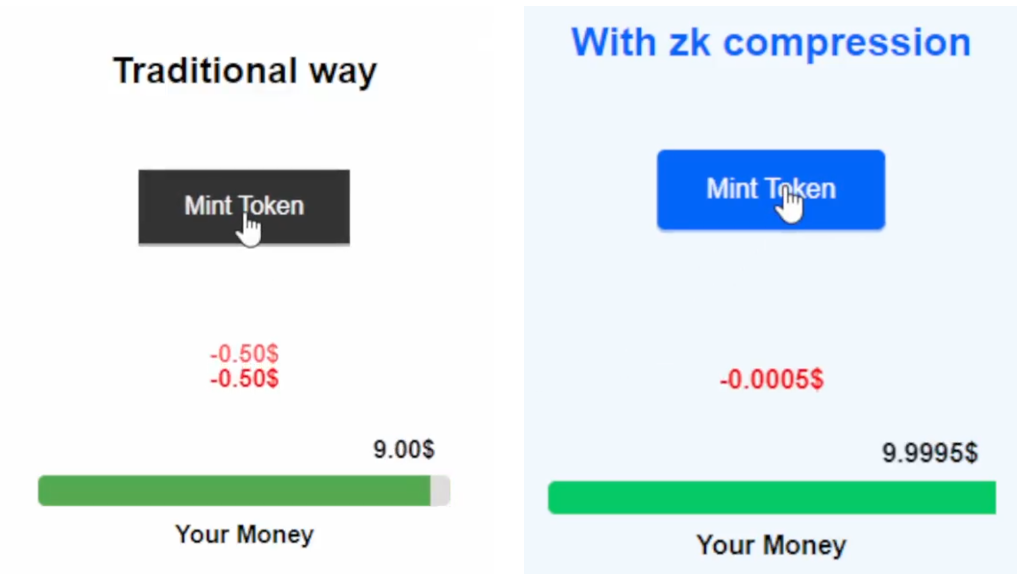
ZK compressed state is stored in compressed accounts. These accounts are similar to regular Solana accounts. Other initiatives include the ZK Token Proof program, which supports privacy transfers through Anza—encrypting SPL token balances and transaction amounts to protect the privacy of payment use cases. Homomorphic encryption allows computations to be performed on encrypted data without decrypting it. For this, privacy transfers use Twisted ElGamal encryption to perform hidden mathematical operations on ciphertext and employ the Sigma protocol to verify these transfers without leaking sensitive information. Only account holders with the decryption key can view their encrypted balances. However, the Global Auditor System on Solana allows selective read access through a separate decryption key for compliance and auditing. There are several key differences that can enhance efficiency and scalability:
Hash Identification: Each compressed account can be identified by its hash value.
Hash Change on Write: Any write operation to a compressed account will change its hash.
Optional Address: An address can optionally be set as a permanent unique ID for the compressed account. This is particularly useful for certain use cases (e.g., NFTs). The reason this field is optional is to avoid computational overhead, as compressed accounts can be referenced by their hash value.
Sparse State Tree: All compressed accounts are stored in a Merkle tree, with only the state root of the tree (i.e., the Merkle root) stored in the on-chain account space. More specifically, the state tree is a concurrent Merkle tree based on Poseidon hash.
Many Solana teams are building ZK compression use cases in the following areas:
Backpack wallet users can hold tokens without paying rent (Gas).
Consumer social applications, such as Tribe.fun, allow creators to send tokens at low cost.
Airdrop tools like Helius Airship.
ZKVM and Network Scalability Stack
RiscZero and SuccinctLabs can help prove arbitrary computations on-chain, unrestricted by chain computation limits. This can enhance ZK-driven Solana light clients, enable streamlined DePIN networks, and secure seamless ZK logins.
Additionally, zkSVM is being used in many use cases:
Solforge Network uses the ZKP network scalability stack and zk compression to enable the transfer of state update proof scalability, optimized for proof generation through LightSVM.
The SVM network deployment platform Terminaxyz targets specific use cases by reducing latency, enhancing privacy, and lowering computation costs.
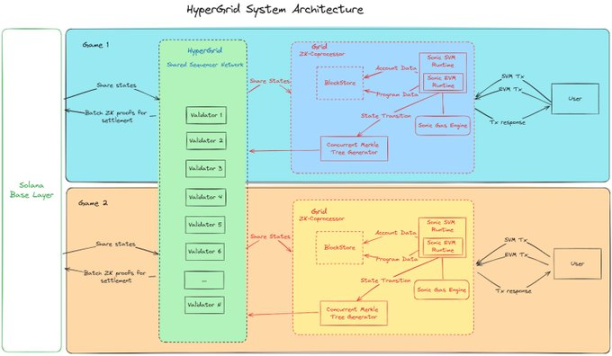
The SVM stack for games and applications, SonicSVM, is also focused on scaling through zk and Hypergrid.
ZetaMarkets Bullet L2 is scaling to extremely high throughput, with all state transitions being provable.
Moreover, teams like Aerius are experimenting with zk proofs.
Other initiatives include the ZK Token Proof program, which supports privacy transfers through Anza—encrypting SPL token balances and transaction amounts to protect the privacy of payment use cases. Homomorphic encryption allows computations to be performed on encrypted data without decrypting it. For this, privacy transfers use Twisted ElGamal encryption to perform hidden mathematical operations on ciphertext and employ the Sigma protocol to verify these transfers without leaking sensitive information. Only account holders with the decryption key can view their encrypted balances. However, the Global Auditor System on Solana allows selective read access through a separate decryption key for compliance and auditing.
免责声明:本文章仅代表作者个人观点,不代表本平台的立场和观点。本文章仅供信息分享,不构成对任何人的任何投资建议。用户与作者之间的任何争议,与本平台无关。如网页中刊载的文章或图片涉及侵权,请提供相关的权利证明和身份证明发送邮件到support@aicoin.com,本平台相关工作人员将会进行核查。



