Zircuit has enabled the SLS mechanism, which aims to isolate "malicious transactions."
Written by: 0xTodd
With the official TGE of Zircuit's $ZRC, let's discuss an interesting mechanism regarding the sequencer in this project.
Zircuit has its own L2, characterized by a solution called "Sequencer Level Security / SLS."
We all know that currently, the entry and exit of L2 transactions are handled by the project's official sequencer. Of course, due to the existence of ZK/challenge proofs, we generally do not worry about the sequencer acting maliciously.
Overall, the sequencer plays a neutral role, always executing each transaction fairly.
So, even though the sequencer is neutral, can we make an effort to have it join the good camp?
Thus, Zircuit has enabled this SLS mechanism, which aims to isolate "malicious transactions."
Normally, how does an L2 transaction get on-chain? It's a simple four-step process:
The user initiates the transaction and broadcasts it.
The transaction enters the mempool and waits.
The sequencer, as a neutral party, helps package it into a block.
The transaction goes on-chain.
However, based on the SLS mechanism, this process changes to five steps:
The user initiates the transaction and broadcasts it.
The transaction enters the mempool and waits.
The sequencer, as a good party, uses some tools to check if the transaction is malicious.
If it is not malicious, it helps package it into a block.
The transaction goes on-chain.
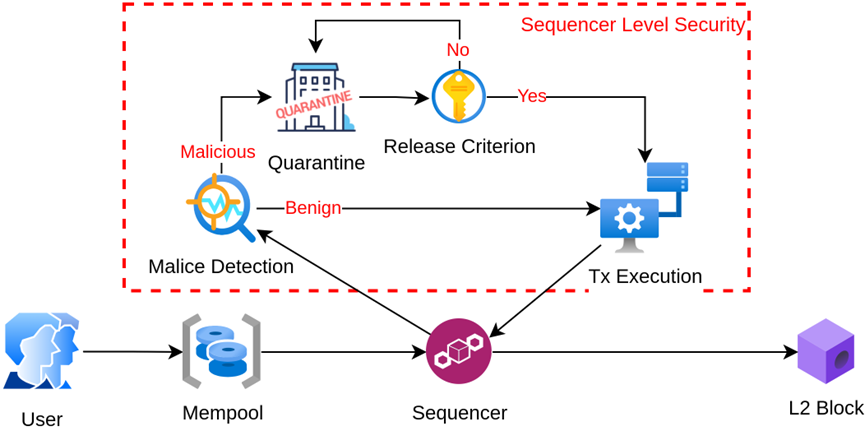
But what if there is a suspected malicious transaction? The changes start from step four:
If suspected malicious, it enters the isolation pool.
If the isolation pool verifies it is correct, the sequencer continues to help package it.
Or:
If suspected malicious, it enters the isolation pool.
If the isolation pool verifies it is indeed a malicious transaction, then it is refused to be packaged on-chain.
The standard for the SLS check for maliciousness may use some open-source libraries and allow AI to assist in the judgment.
In the future, it is hoped to achieve some effects, for example: stolen assets may never be able to be transferred or cross back to L1. This is still quite meaningful for the currently harsh dark forest environment on-chain.
Of course, since it is a transaction check, there may inevitably be some collateral damage. However, I understand that by improving the algorithm of the isolation pool, it can minimize such issues as much as possible.
This is a double-edged sword; blockchain emphasizes permissionless, which slightly contradicts SLS. From the perspective of normal users, such an L2 is indeed safer.
Overall, I feel that although it slightly impacts permissionless, the trade-off for increased security, especially in protecting inexperienced users, is still quite worthwhile.
In conclusion, here is the original paper on Zircuit's SLS mechanism: https://arxiv.org/html/2405.01819v1
免责声明:本文章仅代表作者个人观点,不代表本平台的立场和观点。本文章仅供信息分享,不构成对任何人的任何投资建议。用户与作者之间的任何争议,与本平台无关。如网页中刊载的文章或图片涉及侵权,请提供相关的权利证明和身份证明发送邮件到support@aicoin.com,本平台相关工作人员将会进行核查。




