# I. Introduction: A Shocking Security Crisis in the On-Chain Trading Circle
In November 2024, a major security incident at the on-chain trading platform DEXX shook the entire industry. A hacker attack led to the large-scale theft of user assets, with losses quickly rising to tens of millions of dollars. This incident exposed fatal vulnerabilities in DEXX's security architecture, transforming it from a platform that touted its "non-custodial" features and was highly regarded by users for its convenient and efficient trading experience into a negative example discussed throughout the industry.
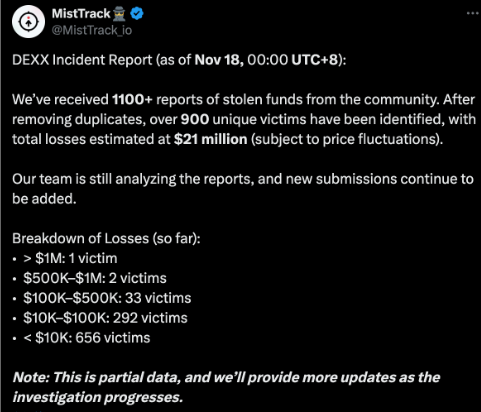
With the booming development of the DeFi ecosystem, on-chain trading tools have experienced explosive growth. These tools attract numerous users with their selling points of "decentralization" and "non-custodial" features. However, the DEXX incident proves that behind convenience often lies significant security risks.
Why is the DEXX incident worth the attention of every on-chain trader?
Reveals Systemic Security Risks: The incident exposed common vulnerabilities in the design and operation of on-chain trading tools.
Reflects on the Truth of "Non-Custodial": It unveiled how some platforms misuse the concept of "non-custodial" to cover up security issues.
Enhances User Risk Awareness: It provides valuable warnings for users and developers, emphasizing the importance of security education and prevention.
The DEXX incident is not just a security crisis; it is a profound inquiry into the current state of the industry: how to balance innovation and security within a decentralized framework?
# II. In-Depth Analysis of the DEXX Incident
Platform Positioning and Business Model
DEXX is a decentralized trading platform focused on on-chain meme coin trading, supporting multi-chain asset trading such as SOL, ETH, and BSC, and providing automated trading tools and liquidity management services. By implementing smart contracts to achieve a convenient trading experience, DEXX was once considered a benchmark for on-chain trading tools. However, this incident exposed fatal flaws in the platform's technical architecture.
Misconceptions of the "Non-Custodial" Concept
Although DEXX claims to adopt a "non-custodial" model that allows users to control their private keys, there are numerous risks in actual operations:
Plaintext Storage of Private Keys: Users export private keys without encryption, making them vulnerable to interception by hackers during transmission.
Centralized Permissions: The platform's permission management system is overly broad, granting the platform actual control over user assets.
Smart Contract Risks: Unverified smart contracts may contain backdoors, allowing unauthorized operations.
Security Vulnerability Analysis
From a technical perspective, DEXX has the following major security risks:
Improper Private Key Storage: The platform secretly records user private keys, allowing hackers to gain full control of assets once they infiltrate.
Weak Permission Management: Authorization logic lacks tiered or restricted access, leading to potential abuse of user assets by the platform.
Insufficient Code Auditing: Audit reports indicate multiple high-risk vulnerabilities on the platform, with the "centralization" issue being particularly severe.
Statistics of Affected Assets
According to on-chain data analysis, the asset losses from this incident include:
Mainstream Tokens: Such as ETH, SOL, etc.
Stablecoins: Such as USDT, USDC.
Meme Coins: Such as BAN, LUCE, which saw significant price drops due to selling pressure.
The DEXX incident not only caused economic losses to users but also dealt a devastating blow to the trustworthiness of the entire on-chain trading tool industry.
# III. The Alarm Bell: Common Issues in On-Chain Trading Tools
1. The Truth of "Non-Custodial"
"Non-custodial" tools are considered the safety benchmark for decentralized trading, but many platforms do not genuinely allow users to control their assets in practice:
Permission Abuse: Users are required to grant excessive permissions, leading to over-centralization of assets.
Implicit Custody: Private keys may be stored and managed by the platform, making security dependent on the platform's technical capabilities.
Contract Backdoors: Some smart contracts embed administrator permissions, allowing the platform to bypass user authorization.
2. The Security Dilemma of Trading Bots
Automated trading tools provide convenient trading but also introduce the following risks:
High Permission Requirements: Trading bots need access to user private keys or API keys, significantly increasing risk.
Logic Vulnerabilities: Complex trading logic may be exploited by attackers, leading to abnormal trades or market manipulation.
Centralized Control: Many bots store user assets under platform control to enhance trading speed, making them easy targets for attacks.
3. Technical Challenges in Private Key Management
Private key management, as the core of on-chain security, faces the following challenges:
Conflict Between Convenience and Security: Offline storage is highly secure but complex to operate; online storage is convenient but carries high risks.
Weak Backup Mechanisms: Users often face risks due to improper backups (e.g., storing in plaintext).
Improper Permission Allocation: Authorization logic lacks refined management, and once permissions are leaked, the consequences can be severe.
4. Common Problems Among Similar Platforms
Analysis shows that on-chain trading tools generally have the following issues:
Insufficient Auditing: Many platforms have not undergone comprehensive third-party security audits.
Weak Risk Control: There are no established comprehensive trading monitoring and emergency response mechanisms.
Lack of User Education: Users lack basic understanding of authorization logic and security operations, and platforms have failed to provide effective guidance.
The DEXX incident highlights the shortcomings of on-chain trading tools in terms of security. To promote healthy industry development, platforms, users, and regulatory bodies must work together to strengthen technical and operational standards.
# IV. User Emergency Self-Rescue Guide (Practical Edition)
The DEXX incident exposed security shortcomings in on-chain trading and served as a wake-up call for users. In the event of a similar crisis, users need to take swift action to minimize losses while establishing long-term security prevention mechanisms. Below is a detailed operational guide and safety recommendations.
Immediate Actions
Check Asset Damage
Use blockchain explorers (such as Etherscan, Solscan) to view wallet transaction records and confirm if there are any abnormal transfers.
Verify asset balances to assess if any assets have been stolen.
Check the authorization status of smart contracts to identify potentially risky authorization records.
Prioritize protecting high-value assets and formulate a transfer plan.
Emergency Asset Transfer Steps
Prepare a brand new and secure wallet address, ensuring its private key has not been leaked.
Transfer assets in order of importance (e.g., stablecoins, mainstream tokens).
Operate in a secure network environment, avoiding public Wi-Fi and infected devices.
Set appropriate gas fees to ensure the transfer transaction is completed quickly.
Revocation of Authorizations
Use tools (such as Revoke.cash) to check and revoke suspicious authorizations to prevent hackers from exploiting them.
Prioritize revoking authorizations for high-risk contracts and keep records of the operations for future investigation.
Increase gas fees to speed up the revocation of authorizations and prevent attackers from acting first.
Evidence Preservation
Take screenshots of relevant transaction records, including timestamps, transaction hashes, contract addresses, and other details.
Export the complete transaction history of the wallet as case materials.
Save all communication records with the platform (emails, announcements, social media screenshots).
Collect media reports and official statements for future rights protection and compensation requests.
Reporting and Rights Protection Guide
Report to local cyber police or cybersecurity departments, providing complete transaction records and event descriptions.
Contact professional blockchain security companies to assist in tracking stolen assets.
Keep the police report receipt and seek help from a professional legal team to plan cross-border or complex rights protection strategies.
Join victim rights protection groups to share information and action plans with other victims.
Ongoing Prevention
Best Practices for Secure Private Key Storage
Use hardware wallets (such as Ledger, Trezor) to store high-value assets, ensuring physical security.
Regularly back up mnemonic phrases or private keys, using multiple encryption protections and distributed storage.
Avoid storing private keys in cloud services or online devices to reduce the risk of theft.
Asset Diversification Management Strategies
Distinguish between hot wallets (for trading purposes) and cold wallets (for long-term storage).
Allocate assets based on usage, such as setting up separate wallets for investment and daily trading.
Regularly check asset distribution to ensure risks are appropriately diversified.
Security Tool Screening Criteria
Investigate the team background, technical strength, and security of the tools or platforms.
Confirm whether the platform has undergone security audits by authoritative organizations and read detailed audit reports.
Pay attention to community feedback to understand user evaluations of the tools and how historical security incidents were handled.
Daily Operation Security Checklist
Operate in a trusted network environment, avoiding public Wi-Fi.
Regularly update the security software on devices, enabling antivirus and firewall protection.
Be cautious with authorization requests, especially from unknown or unverified smart contracts.
Use account monitoring tools to set up transaction alerts to detect abnormal behavior in a timely manner.
Users are the first line of defense for on-chain assets. Through swift emergency actions and long-term security practices, users can effectively reduce the security risks of on-chain assets. Although the protection provided by technology and platforms continues to upgrade, enhancing security awareness and meticulous operational habits remain the best weapons to avoid becoming the next victim.
# V. Advanced Protection: Building a Security Moat for Personal Assets
The security issues of on-chain assets are long-term and complex, especially against the backdrop of frequent security incidents involving trading tools and platforms. To enhance security capabilities, users need to comprehensively establish a "security moat" from basic hardware to technical configurations. Below is an advanced protection guide tailored for users.
1. Hardware Wallet Usage Guide
Hardware wallets have become the best choice for protecting digital assets due to their offline storage characteristics, but correct usage is a prerequisite for ensuring security.
Purchasing Genuine Hardware Wallets
Buy mainstream brands (such as Ledger, Trezor, Onekey) through official channels to avoid counterfeit products.
Avoid using second-hand devices to prevent tampering.
Secure Startup and Initialization
- Complete the hardware wallet initialization in an offline environment, generate the mnemonic phrase, and ensure it is not recorded or leaked by others.
Backup of Mnemonic Phrase and Private Keys
- Record the mnemonic phrase on fireproof and waterproof media (such as metal plates or paper), and store it in multiple secure locations, avoiding digital storage.
Daily Usage Precautions
Connect the device only in trusted network environments, avoiding public Wi-Fi or insecure devices.
Regularly update the device firmware to fix known vulnerabilities.
2. Multi-Signature Wallet Configuration
Multi-signature wallets (Multi-Sig) are an advanced security tool suitable for managing high-net-worth assets, enhancing operational security through multi-party authorization.
Set Multi-Signature Thresholds
- Determine the authorization threshold for multi-signature (e.g., 3/5 or 2/3) to ensure a balance between security and convenience.
Configure Signatory Permissions
- Clearly define the permissions and responsibilities of each signatory to avoid centralization of permissions or single points of failure.
Establish Signature Rules
- Set differentiated authorization thresholds for different types of transactions (e.g., asset transfers, smart contract interactions).
Emergency Recovery Plan
- Configure backup signatories or emergency recovery permissions to ensure that assets are not permanently locked if the primary signatories are unable to operate.
3. Security Assessment Framework for Trading Tools
When selecting on-chain trading tools or platforms, users should systematically assess their security and credibility.
Code Open Source Level
- Prioritize open-source tools that allow the community to review the code and promptly discover and fix vulnerabilities.
Smart Contract Audit Status
- Check whether the tool has undergone security audits by authoritative organizations (such as SlowMist) and carefully read the relevant audit reports.
Team Background Investigation
- Understand the technical background and past project history of the development team to assess their credibility and professionalism.
Community Activity and User Feedback
- Analyze community feedback and activity regarding the tool, especially focusing on how historical security incidents were handled.
Risk Control Mechanisms
- Investigate whether the platform provides risk control measures such as multi-signature, transaction anomaly alerts, and whether it has asset insurance mechanisms.
4. Recommended On-Chain Security Monitoring Tools
Professional on-chain monitoring tools can help users keep real-time track of asset dynamics and promptly detect potential threats.
Asset Monitoring Tools
Recommended Tools: DeBank, Zapper
Functions: Multi-chain asset balance and transaction record tracking, helping users comprehensively control asset status.
Contract Monitoring Tools
Recommended Tools: Tenderly, Defender, Goplus
Functions: Real-time detection of the operational status of smart contracts, identifying potential vulnerabilities or abnormal behaviors.
Transaction Monitoring Tools
Recommended Tools: Nansen, Dune Analytics
Functions: Analyzing on-chain transaction data, tracking fund flows, and promptly detecting abnormal operations.
Risk Warning Tools
Recommended Tools: Forta Network
Functions: Providing real-time risk warnings and attack detection on-chain, helping users take protective measures immediately.
Users bear ultimate responsibility for the security of their assets. By utilizing hardware wallets, multi-signature wallets, and professional security tools, combined with reasonable security assessments and daily protective measures, users can significantly enhance the risk resistance of their personal assets. In this challenging on-chain world, "preparation before the rain" is the only effective strategy for asset protection.
# VI. Reflection and Outlook
The impact of the DEXX incident is not limited to the affected users; it has also sounded the alarm for the entire blockchain industry. It reveals the potential risks in the technical architecture and operational models of on-chain trading tools while providing profound reflections and improvement directions for project parties, users, and industry development.
1. Responsibilities of Project Parties
Project parties play a dual role as technical developers and operators in the on-chain ecosystem, with their responsibilities encompassing security, transparency, and risk management.
Basic Security Responsibilities
Code Security Audits: Regularly undergo authoritative third-party security audits to ensure the security of smart contracts and systems.
Vulnerability Bounty Programs: Attract the community and security experts to proactively discover vulnerabilities and provide solutions.
Risk Reserve Fund System: Establish a special fund to compensate users for losses in the event of security incidents.
Emergency Response Mechanism: Form a professional team to respond quickly and handle security incidents, minimizing the impact.
Information Disclosure Responsibilities
Risk Warning Obligations: Clearly inform users of potential risks and security recommendations before they authorize or use the platform.
Timeliness of Incident Reporting: Publicly disclose the situation to users and provide solutions immediately after a security incident occurs.
Loss Compensation Plans: Develop clear compensation rules to avoid trust collapse in the aftermath of incidents.
Transparency of Technical Architecture: Publicly disclose the platform's technical architecture and permission management mechanisms, subjecting them to user supervision.
2. Responsibilities and Credibility Assessment of KOL Promotion
As industry opinion leaders (KOLs), their promotional activities have a profound impact on user decision-making and trust. It is particularly important to clarify their responsibilities and assess their credibility.
Defining KOL Responsibilities
Due Diligence Obligations: Thoroughly understand the technical background and security of any project before promoting it.
Information Verification Responsibilities: Verify whether the project party's commitments align with actual conditions to avoid misleading users.
Disclosure of Conflicts of Interest: Publicly disclose relationships with project parties and commission models to ensure transparency.
Risk Warning Requirements: Include risk warnings in promotions to guide users in making independent judgments.
Credibility Assessment Indicators
Professional Background: Whether the KOL possesses professional knowledge and industry experience in the blockchain field.
Historical Promotion Record: Whether their past promoted projects are safe and reliable, and how users have evaluated them.
Conflicts of Interest: Whether there is excessive reliance on promotional income that affects objectivity.
Adequacy of Risk Warnings: Whether they provide a complete explanation of potential project risks and offer suggestions.
3. Awakening of User Security Awareness
Users are the final line of defense in the on-chain ecosystem. Enhancing user security awareness is key to preventing asset losses.
Basic Security Awareness
Private Key Security Management: Properly store private keys and mnemonic phrases, avoiding online storage or transmission through insecure channels.
Caution in Authorization Principles: Carefully evaluate smart contract authorization requests, avoiding excessive authorizations whenever possible.
Asset Diversification Storage: Distribute assets across multiple wallets to reduce the risk of single points of failure.
Risk Control Awareness: Regularly check authorization statuses, revoke unnecessary permissions, and maintain account security.
Advanced Security Practices
Use of Multi-Signatures: Increase the operational threshold for high-value assets through multi-signatures.
Security Tool Configuration: Use hardware wallets and on-chain monitoring tools to build a comprehensive protection system.
Regular Security Checks: Inspect wallet statuses, authorization records, and asset distributions to identify potential risks.
Emergency Plan Preparation: Develop clear emergency plans to take swift action in the event of asset theft.
4. Development Directions for On-Chain Trading Tools
Future on-chain trading tools need to achieve comprehensive optimization in technology and operations to regain user trust and promote industry development.
Optimization of Technical Architecture
Fine-Grained Permission Management: Limit the scope of permission grants to avoid excessive authorizations.
Multi-Factor Authentication Mechanisms: Introduce two-factor authentication or dynamic authorization to enhance operational security.
Intelligent Risk Control Systems: Combine real-time monitoring and automatic alerts to promptly detect and address abnormal behaviors.
Increased Decentralization: Reduce reliance on centralized components to truly achieve autonomous control of assets.
Improvement of Security Mechanisms
Introduction of Insurance Mechanisms: Provide security guarantees for user assets through insurance products.
Upgrading Risk Control Systems: Utilize AI and big data to build dynamic risk prevention and control mechanisms.
Normalization of Audits: Incorporate third-party security audits into the daily operational processes of projects to ensure continuous improvement.
Comprehensive Scenario Monitoring: Cover both on-chain and off-chain security scenarios to comprehensively reduce asset risks.
5. The Balance Between Security and Convenience
On-chain trading tools must find a balance between security and user experience to better meet user needs.
Technical Aspects
Simplifying Security Operation Processes: Reduce user operation difficulty through optimized interface design and guidance.
Optimizing User Experience: Enhance operational smoothness and efficiency without sacrificing security.
Automated Security Checks: Integrate intelligent tools to automatically alert users to potential security risks.
Personalized Risk Control Settings: Allow users to customize risk control rules based on their needs.
User Aspects
Differentiated Security Solutions: Provide tiered security solutions for different users.
Flexible Authorization Mechanisms: Support users in quickly adjusting authorization scopes in different scenarios to meet diverse needs.
Convenient Emergency Handling: Offer one-click authorization revocation and emergency lock features to ensure rapid response to security incidents.
Conclusion
The DEXX incident is not just a security accident but a profound reflection for the entire industry. It reminds us that technological innovation cannot come at the expense of security. Only by placing the protection of user assets at the core can the industry truly achieve long-term healthy development.
For users, this is a mandatory lesson in enhancing security awareness; for project parties, it is an urgent task to improve security mechanisms; for all parties in the industry, it is an opportunity to promote standardization and healthy competition. Only by finding the best balance between innovation and security can on-chain trading tools fulfill the promise of decentralization and create real value for users.
The DEXX incident will become a thing of the past, but the warnings it brings will guide the future. Let us learn from it and work together to push the blockchain ecosystem towards a safer, more mature, and trustworthy tomorrow.
About Us
Hotcoin Research, as the core investment research department of Hotcoin, is dedicated to providing detailed and professional analysis for the cryptocurrency market. Our goal is to offer clear market insights and practical operational guidelines for investors at different levels. Our professional content includes the "Play to Earn Web3" series of tutorials, in-depth analysis of cryptocurrency industry trends, detailed analyses of potential projects, and real-time market observations. Whether you are a newcomer exploring the crypto space for the first time or a seasoned investor seeking in-depth insights, Hotcoin will be your reliable partner in understanding and seizing market opportunities.
Risk Warning
The cryptocurrency market is highly volatile, and investing itself carries risks. We strongly recommend that investors conduct investments based on a complete understanding of these risks and within a strict risk management framework to ensure the safety of their funds.
Website: https://www.hotcoin.com/
Medium: medium.com/@hotcoinglobalofficial
免责声明:本文章仅代表作者个人观点,不代表本平台的立场和观点。本文章仅供信息分享,不构成对任何人的任何投资建议。用户与作者之间的任何争议,与本平台无关。如网页中刊载的文章或图片涉及侵权,请提供相关的权利证明和身份证明发送邮件到support@aicoin.com,本平台相关工作人员将会进行核查。




