In the dark forest world of blockchain, please remember two major security principles: Zero Trust and Continuous Verification.
This article serves as a guide, with the complete content available on GitHub.
Original Title: "SlowMist Production | Yuxian: A Self-Rescue Manual for the Blockchain Dark Forest"
Author: Yuxian, Founder of SlowMist Technology
Originally published on April 12, 2022
Blockchain is a great invention that has brought about changes in certain production relationships, partially addressing the precious issue of "trust." However, the reality is harsh; there are many misconceptions about blockchain. These misconceptions have allowed bad actors to easily exploit loopholes, frequently reaching into people's wallets and causing significant financial losses. This has long been a dark forest.
Based on this, Yuxian, the founder of SlowMist Technology, has passionately produced the "Self-Rescue Manual for the Blockchain Dark Forest."

This manual (current V1 Beta) contains approximately 37,000 words. Due to space limitations, only the key directory structure of the manual is listed here as a form of guidance. The complete content can be found on GitHub.
We chose GitHub as the primary platform for releasing this manual because it facilitates collaboration and allows for viewing historical updates. You can Watch, Fork, and Star it; of course, we hope you will also contribute.
Alright, let's begin the guide…
Introduction
If you hold cryptocurrency or are interested in this world, and may hold cryptocurrency in the future, this manual is worth reading repeatedly and practicing with caution. Reading this manual requires a certain knowledge background, and we hope beginners need not fear these knowledge barriers, as much of it can be "played" out.
In the dark forest world of blockchain, always remember these two major security principles:
- Zero Trust: Simply put, it means to remain skeptical, and to always remain skeptical.
- Continuous Verification: If you believe, you must have the ability to verify your points of suspicion and make this ability a habit.
Key Content
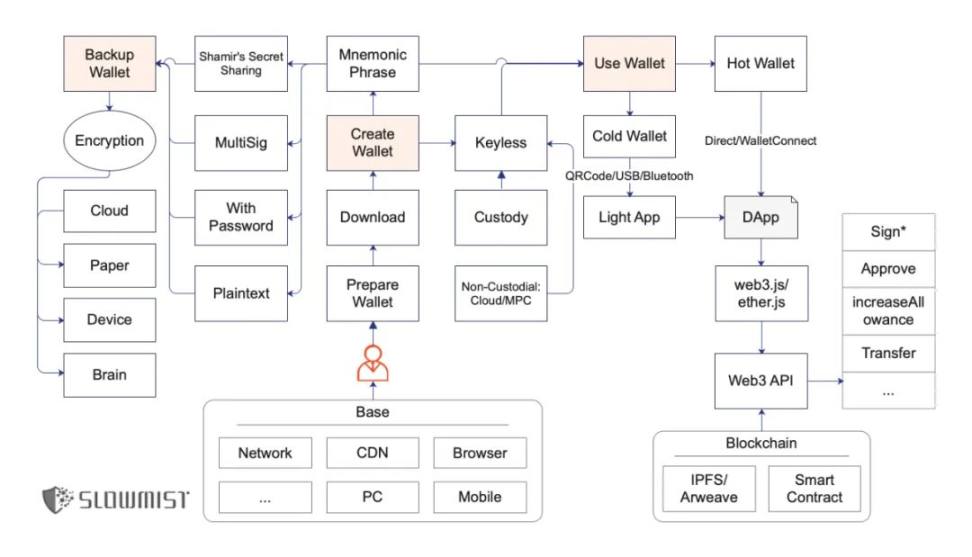
1. Creating a Wallet
Download
- Find the correct official website
- Industry-recognized listings, such as CoinMarketCap
- Ask some trusted individuals
- Download and install the application
- PC Wallet: It is recommended to perform a tampering check (file consistency check)
- Browser Extension Wallet: Pay attention to the number of users and ratings on the target extension download page
- Mobile Wallet: The judgment method is similar to that of extension wallets
- Hardware Wallet: Purchase under the guidance of the official website, and be aware of any signs of tampering
- Web Wallet: It is not recommended to use this type of online wallet
Mnemonic Phrase
When creating a wallet, the appearance of the mnemonic phrase is very sensitive. Please ensure that no one is around you, including cameras or anything that could lead to peeping. Also, check if the mnemonic phrase appears random enough.
Keyless
- Two main scenarios of Keyless (this distinction is made for ease of explanation)
- Custody, i.e., custodial method. For example, centralized exchanges and wallets, where users only need to register an account and do not own private keys; security relies entirely on these centralized platforms.
- Non-Custodial, i.e., non-custodial method. Users uniquely hold the power similar to private keys, but it is not the direct cryptocurrency private key (or mnemonic phrase).
- Advantages and disadvantages of MPC-based Keyless solutions.
2. Backing Up Your Wallet
Mnemonic Phrase / Private Key Types
Plain text: Primarily 12 English words.
With password: Adding a password to the mnemonic phrase will yield a different seed, which will then be used to derive a series of private keys, public keys, and corresponding addresses.
Multi-signature: Can be understood as requiring multiple signatures from different individuals to authorize the use of target funds; multi-signature is very flexible and can set approval strategies.
Shamir's Secret Sharing: The Shamir secret sharing scheme, which splits the seed into multiple shares; to recover the wallet, a specified number of shares must be used.
Encryption
- Multiple backups
- Cloud: Google/Apple/Microsoft, combined with GPG/1Password, etc.
- Paper: Write down the mnemonic phrase (in plain text, SSS, etc.) on paper cards.
- Device: Computer/iPad/iPhone/external hard drive/USB drive, etc.
- Brain: Be aware of the risks of memorization (memory/unexpected events).
- Encryption
- Regularly verify backups.
- Partial verification is also acceptable.
- Ensure the confidentiality and security of the verification process.
3. Using Your Wallet
AML
On-chain freezing.
Choose reputable platforms, individuals, etc., as your trading counterpart.
Cold Wallet
- How to use a cold wallet
- Receiving cryptocurrency: Use alongside wallet observation tools, such as imToken, Trust Wallet, etc.
- Sending cryptocurrency: QR Code/USB/Bluetooth.
- Risks of cold wallets
- Lack of user interaction security mechanisms like "what you see is what you sign."
- Users may lack relevant knowledge background.
Hot Wallet
Interacting with DApps (DeFi, NFT, GameFi, etc.)
Malicious code or backdoor exploitation methods
- While the wallet is running, malicious code may directly upload relevant mnemonic phrases to a hacker-controlled server.
- While the wallet is running, when a user initiates a transfer, the wallet backend may secretly replace the target address and amount, making it difficult for the user to notice.
- Compromising the entropy of random numbers related to mnemonic phrase generation, making these phrases easier to crack.
What is DeFi Security?
- Smart contract security
- Excessive permissions: Add time locks (Timelock)/use multi-signature for admin, etc.
- Gradually learn to read security audit reports.
Basic blockchain security: consensus ledger security/virtual machine security, etc.
Frontend security
- Internal malfeasance: The target smart contract address in the frontend page is replaced/injected with authorization phishing scripts.
- Third-party malfeasance: Supply chain attacks/frontend pages introducing malicious or hacked third-party remote JavaScript files.
- Communication security
- HTTPS security.
- Example: MyEtherWallet security incident.
- Security solutions: HSTS.
Human security: such as internal malfeasance by project parties.
Financial security: cryptocurrency prices, annualized returns, etc.
Compliance security
- AML/KYC/sanctioned area restrictions/securities risk-related content, etc.
- AOPP.
NFT Security
Metadata security.
Signature security.
Be Cautious with Signatures / Counterintuitive Signatures
What you see is what you sign.
Several well-known NFT theft incidents on OpenSea.
- Users authorized NFTs (listed) on OpenSea.
- Hackers phished to obtain relevant user signatures.
- Revoke authorization (approve).
- Token Approvals.
- Revoke.cash.
- APPROVED.zone.
- Rabby extension wallet.
- Counterintuitive real cases.
Some Advanced Attack Methods
Targeted phishing.
Broad-spectrum phishing.
Combining techniques like XSS, CSRF, Reverse Proxy, etc. (e.g., Cloudflare man-in-the-middle attacks).
4. Traditional Privacy Protection
Operating System
Pay attention to system security updates; act immediately when there are security updates.
Avoid downloading random programs.
Set up disk encryption protection.
Mobile Phones
Pay attention to system security updates and downloads.
Do not jailbreak or root unless you are doing security research; otherwise, it is unnecessary.
Do not download apps from unofficial markets.
The premise for using official cloud synchronization: you are confident that your account security is not an issue.
Network
In terms of networking, try to choose secure options, such as avoiding connecting to unknown Wi-Fi.
Choose reputable routers and service providers; do not be tempted by cheap options, and hope that there will be no advanced malicious behavior at the router or service provider level.
Browser
Update promptly.
Do not install extensions unless necessary.
Multiple browsers can coexist.
Use well-known privacy protection extensions.
Password Manager
Do not forget your master password.
Ensure your email security.
1Password/Bitwarden, etc.
Two-Factor Authentication
Google Authenticator/Microsoft Authenticator, etc.
Scientific Internet Access
Scientific internet access, secure internet access.
Secure and well-known: Gmail/Outlook/QQ Mail, etc.
Privacy-focused: ProtonMail/Tutanota.
SIM Card
SIM card attacks.
Defense suggestions.
- Enable well-known 2FA tools.
- Set a PIN code.
GPG
- Distinctions.
- PGP stands for Pretty Good Privacy, a commercial encryption software that has been around for over 30 years and is now under Symantec.
- OpenPGP is an encryption standard derived from PGP.
- GPG, short for GnuPG, is open-source encryption software based on the OpenPGP standard.
Isolated Environment
Adopt a zero-trust security mindset.
Maintain good isolation habits.
Privacy is not something to be protected; privacy is something to be controlled.
5. Human Security
- Telegram.
- Discord.
- Phishing from "official" sources.
- Web3 privacy issues.
6. Blockchain Malicious Behaviors
Theft, malicious mining, ransomware, dark web trading, C2 relay of Trojans, money laundering, Ponzi schemes, gambling, etc.
SlowMist Hacked Blockchain Hacking Archive.
7. What to Do If You Are Hacked
- Stop losses first.
- Protect the scene.
- Analyze the cause.
- Trace the source.
- Close the case.
8. Misconceptions
- Code Is Law.
- Not Your Keys, Not Your Coins.
- In Blockchain We Trust.
- Cryptographic security equals security.
- Being hacked is embarrassing.
- Update immediately.
Conclusion
After reading this manual, you must practice, become proficient, and apply what you've learned. If you have your own discoveries or experiences later, we hope you can contribute them. If you feel sensitive, you can appropriately desensitize or remain anonymous. Additionally, thanks to the maturity of legislation and law enforcement related to security and privacy worldwide; to all deserving cryptographers, engineers, ethical hackers, and everyone who contributes to making this world a better place, including Satoshi Nakamoto. Finally, thanks to the contributors; this list will continue to be updated, and if you have any thoughts, we hope you will contact us.
免责声明:本文章仅代表作者个人观点,不代表本平台的立场和观点。本文章仅供信息分享,不构成对任何人的任何投资建议。用户与作者之间的任何争议,与本平台无关。如网页中刊载的文章或图片涉及侵权,请提供相关的权利证明和身份证明发送邮件到support@aicoin.com,本平台相关工作人员将会进行核查。




