With the rapid development of the Web3.0 industry, the importance of desktop wallets in ensuring the security of user assets has become increasingly prominent. This report presents the details and conclusions of the technical analysis, aiming to enhance the security awareness of all Web3.0 members.
Written by: CertiK
Desktop wallets play a critical role in the Web3.0 ecosystem, providing users with reliable solutions to securely manage digital assets in a decentralized network. A report by Cointelegraph[1] indicates that, according to analysts from Bitfinex, the number of global cryptocurrency holders has significantly increased, rising from 432 million at the beginning of the year to 575 million as of December 1, 2023. In this newly added market, desktop wallets occupy an important share.
As the Web3.0 industry rapidly develops, the importance of desktop wallets in ensuring the security of user assets has become increasingly prominent. However, after conducting an in-depth technical analysis of multiple desktop wallets, the CertiK security team discovered some potential security vulnerabilities that could expose users to higher risks during use. This report presents the details and conclusions of the technical analysis, aiming to enhance the security awareness of all Web3.0 members. We hope to remind users to remain highly vigilant when using desktop wallets to protect their digital assets.
Security Risks from the Supply Chain
Desktop wallets are essential tools for Web3.0 users to manage and protect digital assets. However, in the context of supply chain attacks[2], their security is often overlooked. Supply chain attacks refer to cybercriminals targeting third-party vendors, service providers, or supply chain links that the target organization relies on. To prevent such security incidents, users are advised to verify the hash values of installation packages; even when downloading directly from official websites, the verification step should not be skipped, as only installation packages verified through this process can be deemed safe software. However, not all users possess the ability to perform such verification, especially when using certain desktop wallets, where insufficient user security measures may increase their risk of being attacked.
Specifically, some desktop wallets may inadvertently use modules or algorithms similar to backdoor software, leading to false positives from certain antivirus software. However, official websites usually provide reasonable explanations for these false positives, and users lacking hash verification capabilities may accept them unquestioningly, viewing antivirus warnings as normal. This misplaced trust creates potential vulnerabilities for malware disguised as legitimate wallet installation packages, putting users at greater risk.
As shown in the figure below, 65 antivirus software on VirusTotal analyzed a download file of a common desktop wallet, resulting in 19 software marking the sample as malicious.
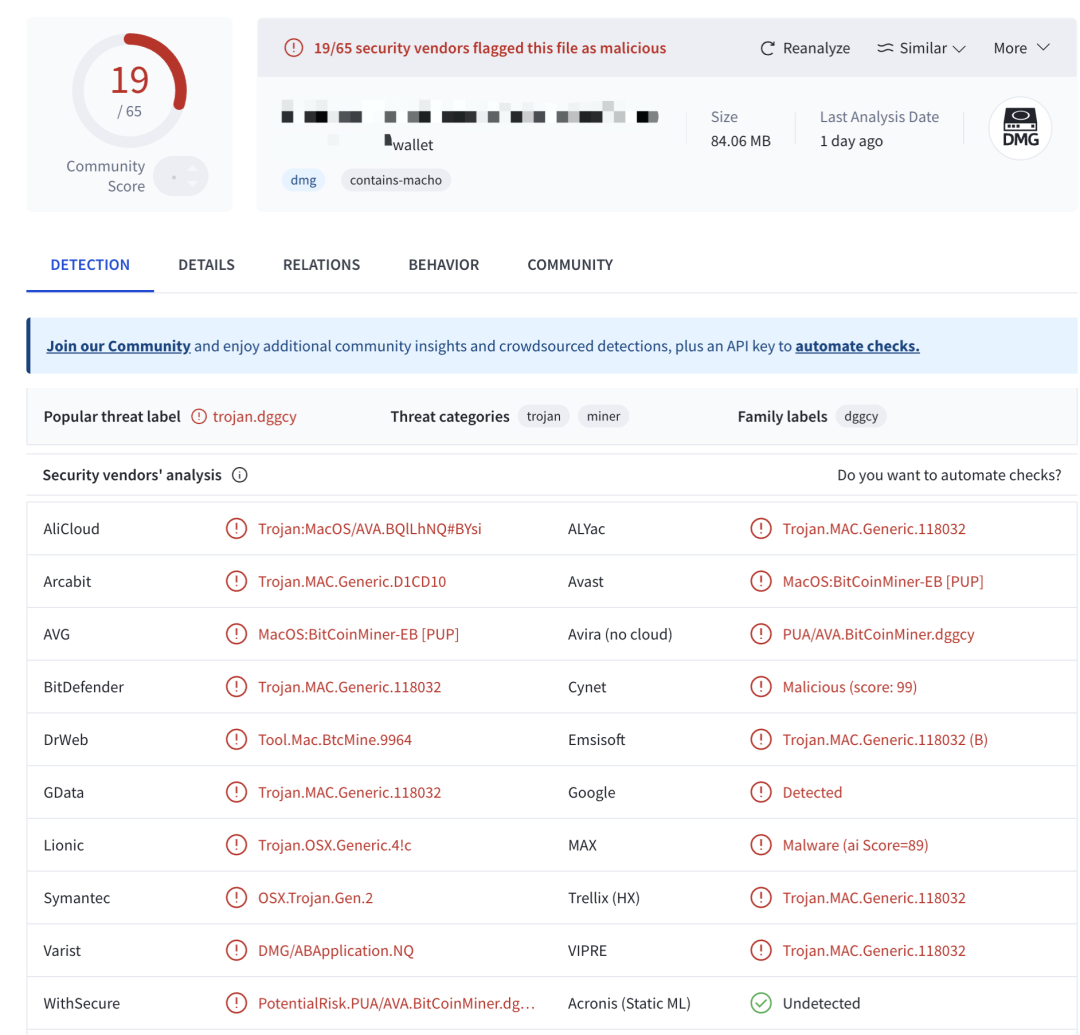
This analysis indicates that supply chain attacks are not merely theoretical risks. For users, the lack of technical means to verify the authenticity of software may lead them to inadvertently download and install malware. Even installation packages downloaded from official websites may trigger antivirus program warnings, making it difficult for users to assess their safety and embedding security risks.
Local File Storage Security Risks
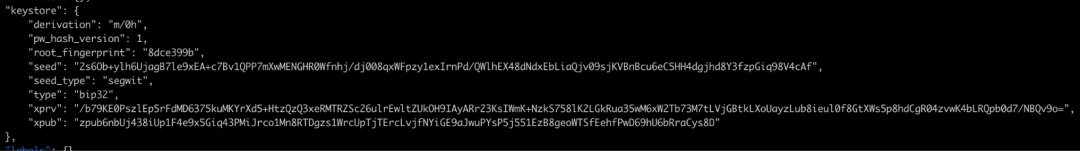
In our in-depth research, we found that certain desktop wallets allow users to store private keys in plaintext for specific business purposes. This practice significantly increases the security risk of users' digital assets, as once a user's computer is infected with a virus or malware, the plaintext private keys will be directly exposed to attackers, jeopardizing the security of their digital assets.
Unencrypted local files:
Encrypted local files:
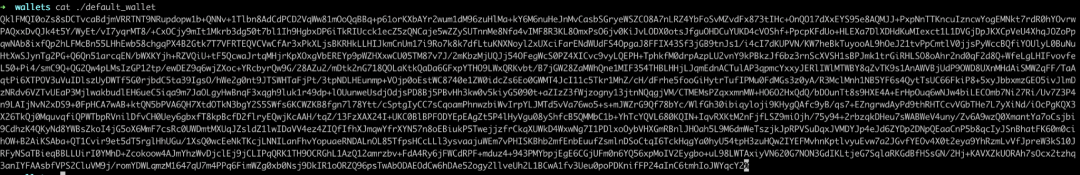
Even if users encrypt local files with a PIN code, the security of the keys cannot be fully guaranteed under the threat of malware. These wallets, whether running as standalone desktop applications or as browser extension plugins, may become targets for malware. However, users often trust desktop wallets due to their convenience and functionality, overlooking potential security vulnerabilities. Compared to the strict permission management and data isolation of mobile applications, desktop wallets appear relatively weak in protecting users' private keys. Therefore, users must remain vigilant about the security of their operating environment when using desktop wallets to avoid theft due to improper storage or insecure settings.
Security of PIN Code Encryption Algorithms
Another high-risk security issue is that many desktop wallets use vulnerable file encryption methods, making it easier for attackers to access and decrypt users' encrypted data. This encryption method means that the wallet does not bind file encryption to the hardware information of the device. This implies that even if the file is encrypted, attackers can still transfer the file to other devices for offline decryption, thereby bypassing the inherent security measures of the device.
Further analysis revealed that some wallets have weaknesses in their brute-force cracking algorithms when using PIN codes. The hash iteration count of the encryption algorithms used by many wallets is far below industry standards. For example, OWASP[3] recommends using 600,000 iterations to protect passwords, Apple has set 10,000,000 iterations for its backup keychain, and 1Password and LastPass use 650,000 and 600,000 iterations, respectively. However, some desktop wallets have set their encryption algorithm hash iteration count to only 5,000, which is far below these industry security benchmarks. In this case, attackers can obtain users' PIN codes through brute-force techniques, and even complex passwords may be easily cracked.
Additionally, we found during the audit that some wallet software's password protection mechanisms are insufficient to withstand complex attacks. Malicious attackers typically first steal users' encrypted data and then use powerful computing resources to decrypt it in an offline environment. Due to vulnerabilities in the choice of encryption algorithms in certain desktop wallets, their encrypted data is more easily cracked. This not only puts users' digital assets at risk but also poses new challenges to the overall security of the Web3.0 ecosystem.
Relatively Secure Desktop Wallet Solutions
When using desktop wallets, it is recommended to choose MPC (Multi-Party Computation) wallets or hardware wallets, as desktop systems (PC systems) have inherent security vulnerabilities compared to mobile devices. Although desktop wallets are simple to operate and easy to access, their continuous internet connection exposes them to more severe threats from hackers and malware. Therefore, for users requiring higher security, choosing other types of wallets is a wise decision.
MPC wallets have significant advantages in enhancing the security of digital assets and recovery functions. Utilizing Secure Multi-Party Computation technology, the wallet divides the private key into multiple segments and stores them separately among different participants or nodes. This design eliminates the risk of a single point of failure, ensuring that no single entity possesses the complete private key. Therefore, even if a user's desktop system is compromised, attackers cannot use any single key segment to steal assets. Only when the segments from multiple participants are combined can a valid transaction signature be generated. Thus, as long as not all key segments are stolen simultaneously, the user's assets remain secure.
In addition, the distributed key management system of MPC wallets provides greater operational flexibility and lower transaction costs. It supports hidden signatures and off-chain accountability mechanisms, further enhancing privacy and security. In this way, MPC wallets ensure that even in the event of partial system breaches, the security of digital assets is not threatened.
Another advantage of MPC wallets is their recovery functionality. If a user's device is lost or damaged, they can still recover their keys through third-party services. This process requires users to reconstruct the private key using key segments pre-distributed in different locations. Additionally, some MPC wallets offer social recovery features, allowing emergency contacts to assist users in regaining access to their wallets in extreme situations.
Desktop hardware wallets provide a physically isolated solution by storing private keys within a hardware device. This design ensures that all signing operations are completed offline within the hardware, meaning that even if a user's desktop system is compromised, attackers cannot access the stored private keys. This physical isolation significantly enhances asset security, as private keys are kept off the internet, reducing the risk of being hacked and stolen.
Today, most hardware wallets also offer recovery features to prevent asset loss due to hardware damage or loss. This recovery process typically involves creating backup mnemonic phrases or key segments, which users can securely store in different locations. If the hardware device is lost or damaged, users can use this backup information to regain access to their wallets and retrieve their assets.
Furthermore, some hardware wallets integrate biometric technology to enhance security. This means that even if unauthorized individuals obtain key segments, they cannot breach the user's wallet without biometric authentication. Biometric technologies may include fingerprint recognition, facial recognition, or voice recognition, adding an extra layer of security to hardware wallets.
For example, Zengo's MPC system uses multiple private key segments stored on different devices to enhance wallet security. The recovery function in the MPC system is crucial, allowing users to retrieve their wallets in case of device loss or damage. To ensure asset security, private key segments are tightly bound to accounts, meaning that assets are only at risk of loss if both the private key segments and the account are lost simultaneously.
Additionally, some hardware wallet manufacturers (such as Ledger) also offer identity-based key recovery services. For instance, Ledger's "Ledger Recover[4]" service divides the wallet recovery phrases into three encrypted segments and distributes them to three custodians. If users lose their mnemonic phrases, two segments can be combined after identity verification to regain access to locked funds. This service aims to provide additional security against the risk of losing digital asset keys, but it also raises concerns among some users, as this method requires online storage of mnemonic phrases associated with government-issued identification.
Multi-Party Computation (MPC) in Secure Desktop Wallets
When comparing the security of MPC wallets and hardware wallets, both have subtle advantages and disadvantages.
Due to the inherent limitations of hardware wallets—such as limited CPU performance, restricted network connectivity, and rudimentary user interfaces—there are challenges in displaying detailed transaction information. This makes it difficult for users to fully confirm transaction details when in-depth verification is needed. Therefore, in this context, MPC wallets become a relatively better choice. MPC wallets allow multiple parties to collaboratively compute and verify transaction data without exposing sensitive information, thus providing a more robust framework for validating transaction purposes and integrity. Unlike hardware wallets, MPC-based solutions[5] can leverage the computing and networking environments of mobile devices or other platforms, allowing for closer integration with backend systems and reducing risks associated with transaction verification.
Overall, desktop hardware wallets provide users with a secure and reliable means of asset protection through physical isolation and wallet recovery features. The introduction of biometric technology further enhances this protection, ensuring that users' assets are safeguarded even in extreme situations.
Comparison of Desktop Wallet Solutions
Based on the aforementioned risk and security analysis, we conducted a comparative assessment of multiple desktop wallets. The figure below summarizes the security mechanisms of these wallets and their protective measures against security risks. (S0 represents basic risks, with higher levels indicating more complex risks.)
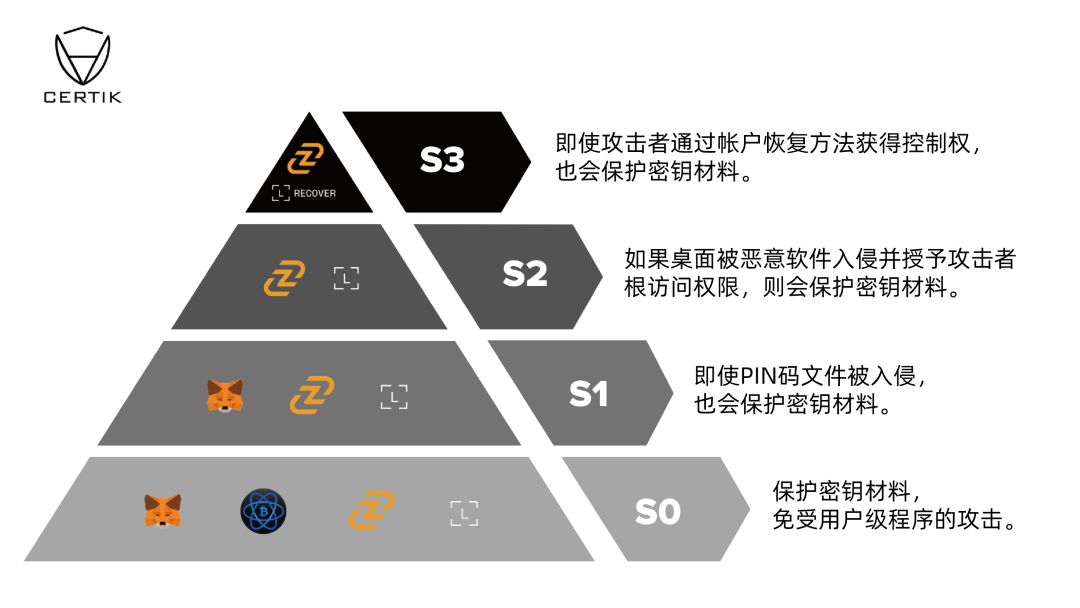
Summary
As important tools for managing digital assets, desktop wallets face multiple security challenges: false positives from antivirus software, lack of sandbox protection, and insufficient encryption algorithms can all expose user assets to theft risks. This is particularly dangerous for users lacking technical experience, as they may struggle to identify and respond to these risks. Therefore, wallet developers need to strengthen security measures to ensure the safety of the software.
At the same time, users should also enhance their risk awareness and adopt best practices for storing and managing digital assets. Through rigorous auditing and continuous improvement of desktop wallets, we can better protect the security of users' digital assets and promote the healthy development of the entire Web3.0 ecosystem.
[1] https://cointelegraph.com/news/crypto-users-1-billion-2024-bitfinex-analysts-prediction
[2] https://www.cloudflare.com/learning/security/what-is-a-supply-chain-attack/
[4] https://www.ledger.com/academy/what-is-ledger-recover
[5] https://zengo.com/introducing-zengo-desktop-the-most-secure-desktop-experience/
免责声明:本文章仅代表作者个人观点,不代表本平台的立场和观点。本文章仅供信息分享,不构成对任何人的任何投资建议。用户与作者之间的任何争议,与本平台无关。如网页中刊载的文章或图片涉及侵权,请提供相关的权利证明和身份证明发送邮件到support@aicoin.com,本平台相关工作人员将会进行核查。



