This article will introduce two common methods of hardware wallet theft - hardware wallet manual fraud and hardware wallet modification disguise scams.
Written by: Bitrace
A hardware wallet is a physical device specifically designed for storing cryptocurrencies, considered an important means of securely managing crypto assets. Its built-in security chip stores private keys offline, ensuring that users have complete control over their cryptocurrencies. Hardware wallets typically operate in an offline state, further reducing the risk of being attacked by internet hackers.
However, in a context where investors generally lack understanding, a large number of fraud incidents targeting novice users still occur, leading to the loss of assets stored in hardware wallets. This article will introduce two common methods of hardware wallet theft - hardware wallet manual fraud and hardware wallet modification disguise scams.
Hardware Wallet Manual Fraud
The core of this type of theft method is to exploit ordinary investors' lack of understanding of how to use hardware wallets by replacing the genuine manual with a fake one, misleading victims into transferring funds to phishing addresses. Victims purchase hardware wallets from third-party e-commerce platforms, open the packaging, and follow the "initial PIN code" indicated in the "manual" to access the hardware wallet. After backing up the "mnemonic phrase" printed in the "manual," they deposit a large amount of funds into the wallet address, ultimately resulting in theft.
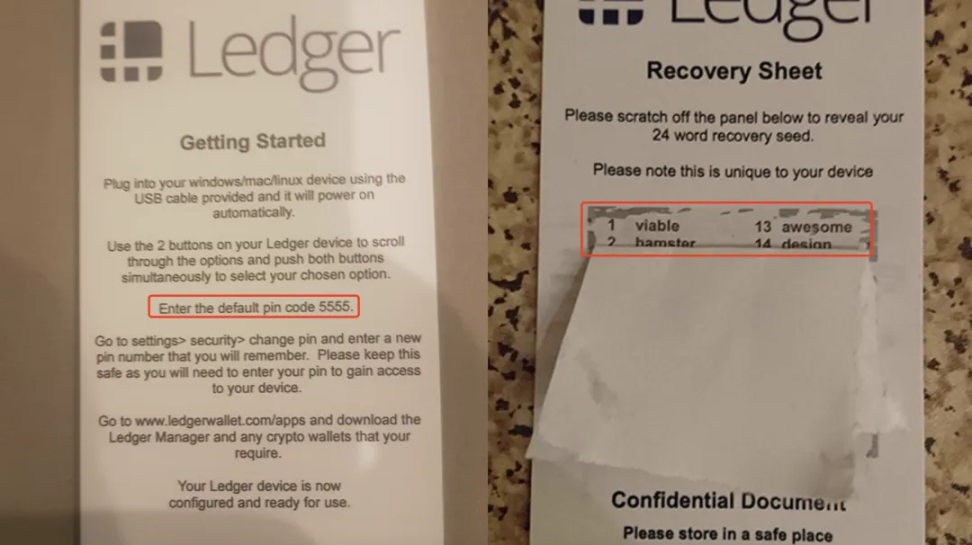
The reason is not that the wallet has been compromised at the hardware level, but that the thieves activate the wallet in advance to obtain the address mnemonic phrase, forge a fake manual for repackaging, and then sell the activated hardware wallet to victims through unofficial channels. Once the target transfers crypto assets to the address, it enters the standard fake wallet theft process.
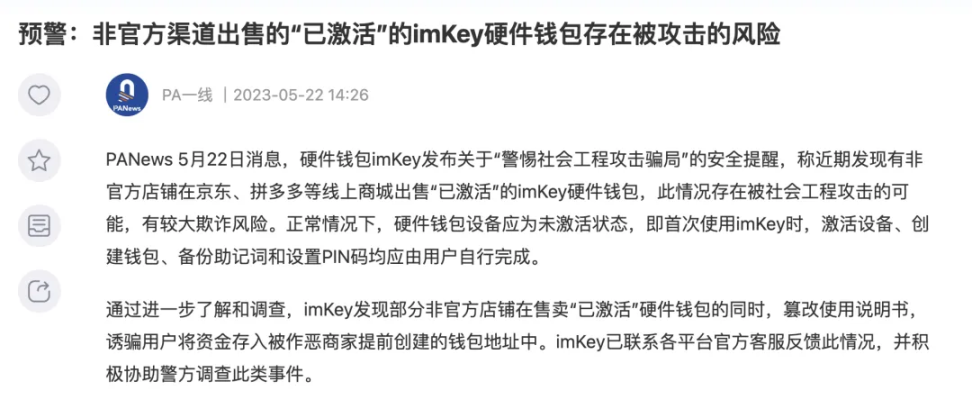
Similar risks also exist in the secondary market in Chinese-speaking regions. The well-known hardware wallet manufacturer imkey has issued warnings - discovering that some unofficial stores are selling "activated" hardware wallets while tampering with the user manual, tricking users into depositing funds into wallet addresses created in advance by malicious merchants. This highlights the importance of identifying official e-commerce stores, which is as crucial as recognizing the official website.
Hardware Wallet Device Modification
A Ledger user received a package containing a brand new Ledger X hardware wallet and a letter, despite not having placed an order. The letter stated that due to a cyber attack on Ledger, user data had been compromised, and the company was sending new hardware wallet devices to affected customers, requesting users to replace their devices for security.

However, the authenticity of this letter is questionable. Ledger CEO Pascal Gauthier has explicitly stated that the company will not provide any compensation for accidental data leaks. The user also indicated that this was a scam, sharing more images and opening the device to show clear signs of tampering inside the plastic case of the hardware wallet.
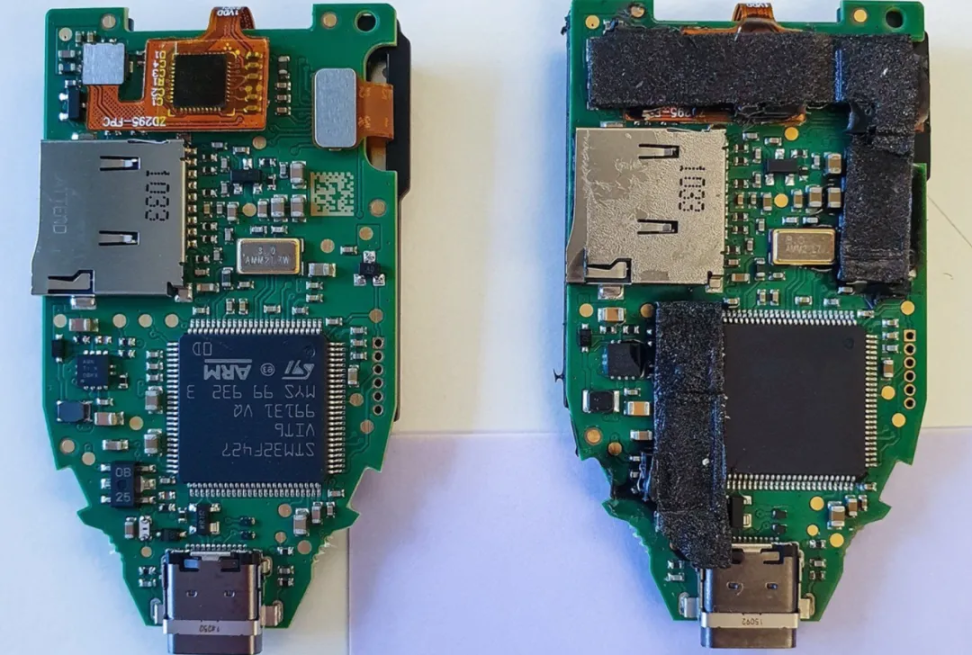
Additionally, the Kaspersky security team has reported a case of a counterfeit Trezor hardware wallet, where the victim purchased a Trezor Model T from an unofficial channel, but the device had been altered by attackers who replaced the internal firmware, allowing them access to the user's crypto assets and enabling theft.
In Conclusion
From the above cases, it is clear that supply chain attacks targeting hardware wallets are widespread, and ordinary investors as well as hardware wallet manufacturers should be vigilant. Correct usage can effectively mitigate the risk of theft:
- Purchase hardware devices from official channels. Any hardware wallet purchased from unofficial channels is not secure.
- Ensure the wallet is in an unactivated state. Officially sold hardware devices must be in an unactivated state. If investors find that the device has been activated after powering it on, or if the manual indicates an "initial password" or "default address," they should stop using the device immediately and report it to the hardware wallet manufacturer.
- Ensure the address is generated by the user. Apart from the device activation process, setting the PIN code, generating the binding code, creating the address, and backing it up must also be completed by the user. Any step performed by a third party poses a financial risk to the user. Normally, the hardware wallet device should be in an unactivated state, meaning that when first using the hardware wallet, the user should activate the device, create the wallet, back up the mnemonic phrase, and set the PIN code themselves.
免责声明:本文章仅代表作者个人观点,不代表本平台的立场和观点。本文章仅供信息分享,不构成对任何人的任何投资建议。用户与作者之间的任何争议,与本平台无关。如网页中刊载的文章或图片涉及侵权,请提供相关的权利证明和身份证明发送邮件到support@aicoin.com,本平台相关工作人员将会进行核查。



