We cannot deny the value brought by Permit, but the increasing number of theft incidents recently also indicates that the harm it brings seems to be greater.
Written by: Keystone
1. Understanding Permit in One Minute
Let's start with a little story about borrowing money:
I am preparing to borrow 1 million from my good friend Jack Ma. Without a word, Jack Ma picks up the phone and calls the bank. After confirming his identity, he informs the bank: I want to authorize someone to have a withdrawal limit of 1 million. The bank replies that it has received the authorization and recorded it.
Next, I just need to go to the bank and inform the counter that I am there to withdraw the 1 million authorized by Jack Ma. At this point, the bank will check for any authorization records and, upon confirming that I am indeed the authorized person, will give me the 1 million.
This little story can be seen as a visualization of the Approve authorization on ETH. In this process, the authorization can only be communicated to the bank by Jack Ma (the asset owner) via phone (on-chain), and the bank (Token contract) manages these authorizations. Only then can I (the authorized party) withdraw money from the bank, not exceeding the authorized amount. If the bank does not find an authorization record, my withdrawal request will undoubtedly be denied.
Now, if we switch to another authorization method—Permit—what changes would occur in the process of borrowing money from Jack Ma?
This time, when I ask to borrow 1 million again, generous Jack Ma is too lazy to make a call. He pulls out a check from his pocket, fills in the amount, signs it, and hands it to me. I take this check to the bank for redemption. At this point, even though the bank has no authorization record, the bank confirms the authenticity of the check based on Jack Ma's signature and pays me the specified amount.
I believe everyone has noticed the differences in the processes. Approve, as an important function in ERC-20, has been widely used shortly after ETH went live. Why was the Permit method later introduced in ERC-2612 to achieve the same effect?
2. Why is Permit Needed?
The ERC-2612 proposal was put forward in March 2019 and completed its final review in October 2022. Its launch is closely related to the multiple surges in gas prices on the ETH mainnet during this period.
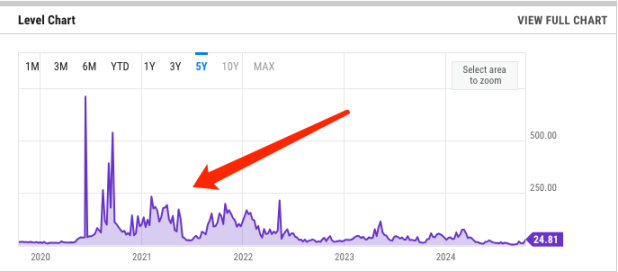
Image: ETH mainnet gas price remained high from 2020 to 2022
The frenzied bull market, combined with the wealth effect of new projects on-chain, has led to a surge in user enthusiasm for on-chain transactions, with users willing to pay higher fees to expedite transactions. Sometimes, being on-chain a block earlier often means significantly higher returns.
However, the consequence of this phenomenon is that when users trade tokens on-chain, they often have to bear high gas fees. Under the Approve method, two transactions (TX) are required to complete a token swap, which can be a nightmare for users with smaller amounts of funds due to the transaction fees incurred.
The Permit introduced in ERC-2612 changes the authorization process to offline signing, which does not need to be immediately on-chain; it only needs to be provided when transferring tokens. Just like in the borrowing story, I only need to present the check to the bank for verification when I go to withdraw.
Busy Jack Ma saves a phone call, and it seems that users also save a transaction. The savings in fees during high gas prices can be quite substantial, seemingly a win-win situation. But little do we know, Pandora's box has quietly opened…

3. Volcanic Eruption of Wild Growth
Before the emergence of Permit, one of the methods hackers used to phish cryptocurrency users was to induce them to sign Approve transactions. Such transactions require users to spend gas, making them more alert and less likely to succeed. Even if a user hastily clicks, the time it takes for the transaction to go on-chain allows the user to quickly submit a transaction with the same nonce to rescue themselves, making it relatively difficult for hackers to succeed.
The introduction of Permit, however, is undoubtedly a boon for hackers. Compared to Approve, Permit does not consume gas and only requires a signature, which lowers user vigilance. Additionally, due to the nature of offline signing, the initiative is in the hands of the hacker. Not only can users not take back their authorization, but hackers can also choose the right moment to commit their crimes, maximizing their benefits.
The negative impact resulting from this is evident in the increasing number of phishing victims and the amounts stolen. According to statistics from @ScamSniffer:
In 2023, the amount lost by phishing victims was 295 million USD.
In the first half of 2024, this amount has already exceeded 314 million USD.
By the end of Q3 2024, there was a significant incident: a wallet address suspected of being a "god fish" fell victim to a Permit phishing attack, losing 12,000 $spWETH, worth 200 million RMB.
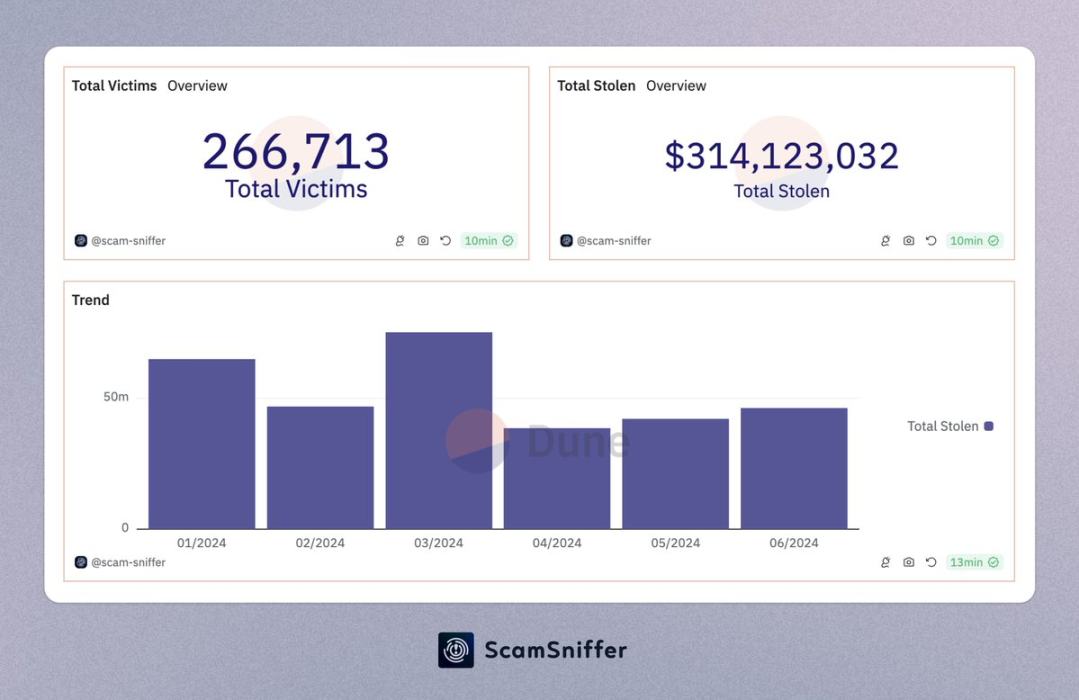
Image: ScamSniffer's phishing attack statistics report for the first half of 2024
Such a situation is likely beyond the expectations of the original proposal developers. The initial intention of introducing Permit was to reduce users' gas costs and improve user experience and efficiency. What was thought to be a double-edged sword has turned out to be a large kitchen knife, with one side extremely sharp, directly cutting a large hole in the shield of user asset security.
There are many similar signature authorization methods like Permit, such as Permit2 launched after Uniswap, which allows all ERC-20 tokens to support offline signing. As the No.1 DEX, Uniswap's move has also increased users' reliance on offline signing, raising the risk of phishing.
4. How to Prevent?
So, as ordinary users, facing this large kitchen knife hanging over our heads, what measures can we take to avoid losses and prevent risks?
1. Raise Awareness
Stay Calm About Airdrop Temptations
Airdrops from cryptocurrency projects can be very enticing, but most of the time they are phishing attacks disguised as airdrops. When encountering such information, do not let your guard down and directly "claim" it. Confirm the authenticity of the airdrop and the official website through multiple sources to avoid falling into phishing sites.
Avoid Blind Signing
If you unfortunately enter a phishing site and are unaware, when a transaction window pops up in your wallet, you should carefully check the transaction details. If you see terms like Permit, Permit2, Approve, IncreaseAllowance, etc., it means this transaction is requesting token authorization, and you should be cautious, as a normal airdrop process does not require this. Keystone has also implemented transaction parsing and display on the hardware side, allowing users to avoid blind signing and prevent serious consequences caused by impulsive actions.
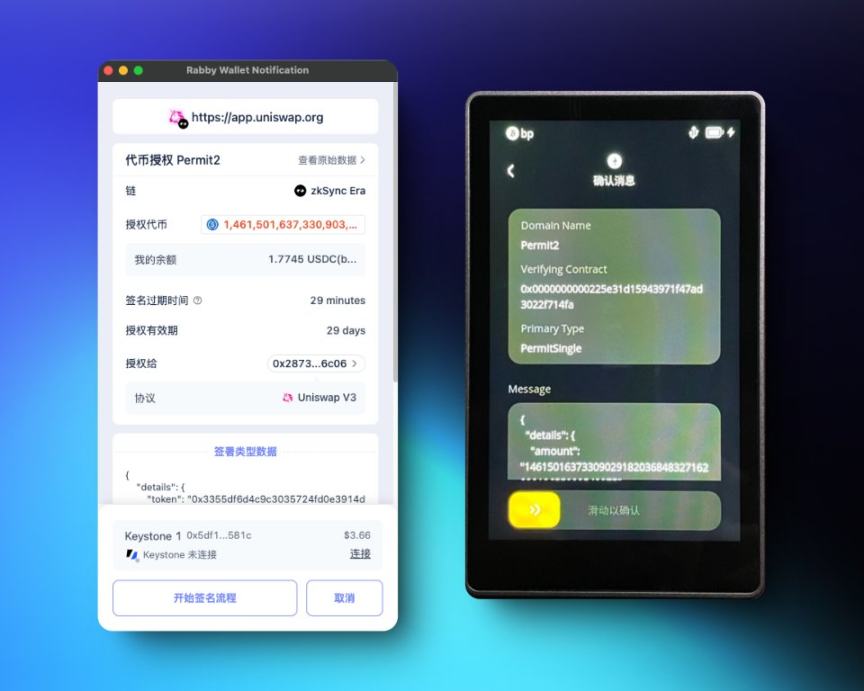
Image: Keystone hardware wallet and Rabby Wallet parsing and displaying Permit2 signed transactions
2. Use Tools Wisely
ScamSniffer
For ordinary users, accurately identifying phishing websites can be very challenging, and there will inevitably be some that slip through the cracks. By using the ScamSniffer browser extension, users will receive alerts before entering suspected phishing websites, allowing them to stop interactions in time.
Revoke
Revoke.cash can display the token authorization records in users' wallets. For any suspicious or unlimited authorizations, we recommend revoking them. Develop a habit of regularly cleaning up authorizations and try to limit authorizations to only what is necessary.
3. Asset Isolation and Multi-Signature
As the saying goes, do not put all your eggs in one basket, and this applies to cryptocurrency assets as well. For example, we can store large amounts of assets in a cold wallet like Keystone, while using a small hot wallet for daily interactions. Even if we accidentally fall for a scam, our assets will not be completely wiped out.
If higher security is required, multi-signature can be used to further enhance security. Assets with multi-signature can only be operated or transferred when the number of wallet approvals reaches a threshold. If a single wallet below the threshold is hacked, the hacker will not be able to access the assets.
5. Conclusion
We cannot deny the value brought by Permit, but the increasing number of theft incidents recently also indicates that the harm it brings seems to be greater. Just like the previous ethsign method, which was favored by hackers due to its poor readability and significant harm, it has now been largely abandoned by most wallet software. Its functions have been replaced by some safer methods.
Focusing on Permit, are we also at a crossroads similar to what ethsign once faced? Whether to improve and upgrade or to abandon it requires ETH developers to spend some time thinking and discussing.
免责声明:本文章仅代表作者个人观点,不代表本平台的立场和观点。本文章仅供信息分享,不构成对任何人的任何投资建议。用户与作者之间的任何争议,与本平台无关。如网页中刊载的文章或图片涉及侵权,请提供相关的权利证明和身份证明发送邮件到support@aicoin.com,本平台相关工作人员将会进行核查。



