Author: Biteye, Source: Author's Twitter @BiteyeCN
On September 28, an address lost approximately $32.33 million due to a phishing attack, which is rumored to be related to the cryptocurrency figure Shen Yu. Coincidentally, on October 11, assets worth $35 million in fwDETH were again stolen by a phishing gang. In just half a month, virtual assets totaling over 470 million RMB have become difficult to recover due to Permit signature phishing attacks.
Why is Permit signature phishing so effective? Even cryptocurrency figures have fallen victim one after another?
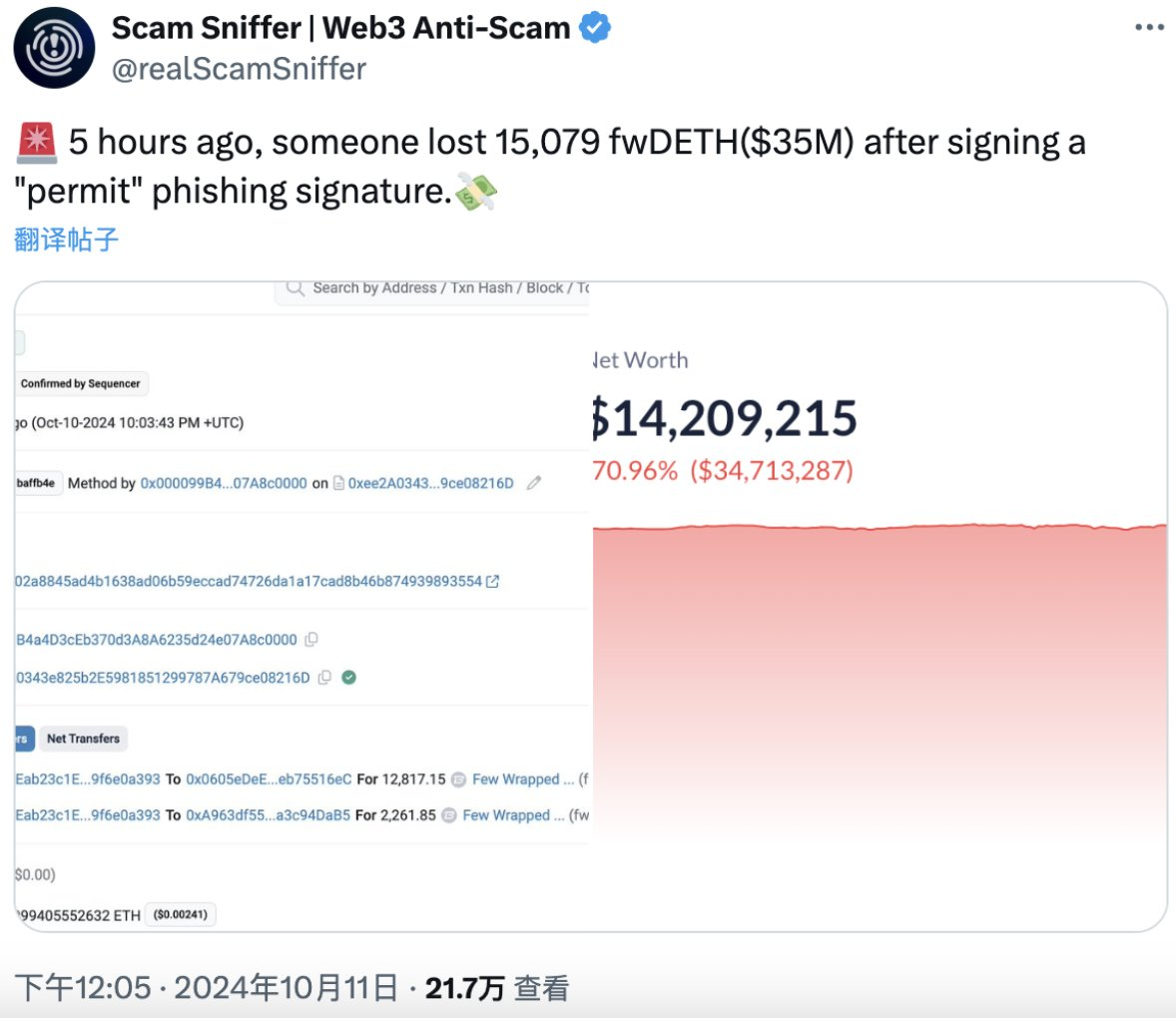
What is a Permit Signature?
To understand the introduction of Permit signatures, one must first grasp the trading rules of ERC20 tokens: Account A can call the approve function to authorize Account B to operate specified tokens, and only the token owner can call this function.
Permit is a mechanism that uses offline signatures to achieve authorization, allowing the approval step to be skipped and gas fees to be avoided. In this process, A signs B off-chain in advance and provides this signature to B; B can then use this signature to call the permit function to execute A's authorization, allowing B to use transferFrom for token transfers.
Through Permit, A can implement token transfers without any on-chain transactions, and the execution of the permit operation is not limited to the account owner. Permit was officially introduced in the ERC20 protocol's EIP-2612 proposal, providing users with a convenient and cost-effective interaction method.
How is the Permit Signature Used to Implement Phishing Attacks?
According to the introduction above, when a user mistakenly enters a phishing website and clicks a link, the hacker obtains the signature, and then the hacker submits the permit on-chain using the signature information, gaining control over the user's assets and transferring them.
Attack Steps: Enter phishing website - Sign on the phishing website after linking wallet - Hacker obtains signature and steals assets through permit.
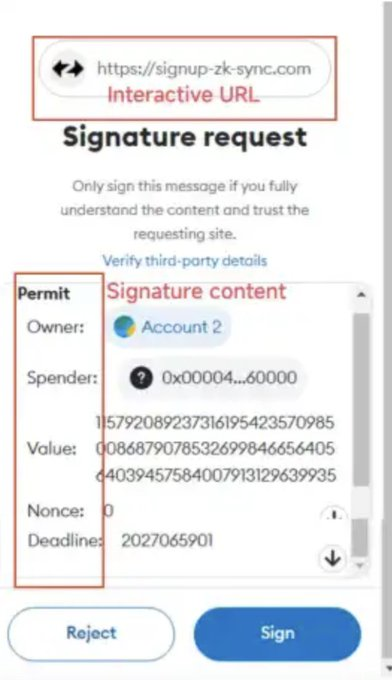
For example, below is a malicious signature from a phishing website: the top of the image shows that this is a phishing site for zksync, and the permit signature below shows that the wallet (owner) is authorizing an address (spender), with the value indicating the amount of tokens authorized, and the deadline is the timestamp, valid before the given time.
How to Avoid Permit Signature Phishing Attacks
Permit signature phishing attacks are not entirely unavoidable; most users who suffer losses have repeatedly made multiple security mistakes.
First, users should distinguish between wallets for holding tokens and wallets for interacting with DeFi. Before linking wallets, signing, or authorizing, carefully check the URL to ensure that you have entered the correct website.
Some websites may also experience cases where contracts are maliciously replaced by hackers. Before clicking to sign or authorize, we should carefully read the Signature request information that pops up from the wallet to ensure that the authorization is for the correct address and that the assets and amounts are within a controllable range.
Finally, we can use security plugins like @walletguard and @realScamSniffer to help identify abnormal risks, and periodically use authorization tools like RevokeCash (https://revoke.cash) to check for any unusual authorizations. Additionally, choosing to use plugin wallets like @Rabbyio can provide more readable signature information.
免责声明:本文章仅代表作者个人观点,不代表本平台的立场和观点。本文章仅供信息分享,不构成对任何人的任何投资建议。用户与作者之间的任何争议,与本平台无关。如网页中刊载的文章或图片涉及侵权,请提供相关的权利证明和身份证明发送邮件到support@aicoin.com,本平台相关工作人员将会进行核查。




