Author | Liz
Editor | Liz
Background
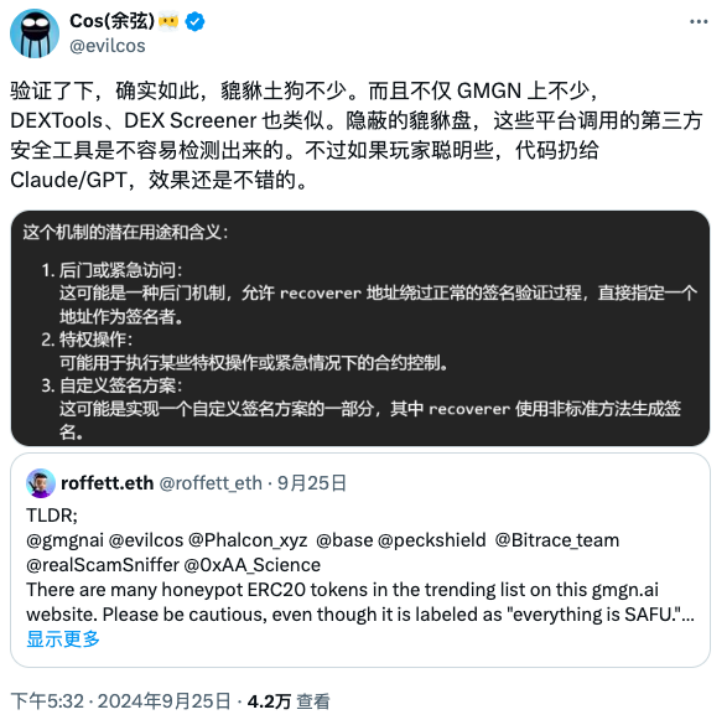
Recently, X user @roffett_eth tweeted that there are many ERC20 honeypot tokens in the trend list of the GMGN website. Even if these tokens are marked as "Everything is SAFU," please remain vigilant, as scammers have not completed the entire rug process. SlowMist founder Cos stated that this situation is not only present on GMGN but also on DEXTools and DEX Screener. Based on this, this article will analyze common malicious tactics used in honeypot schemes, listing their characteristics so that users without a technical background can acquire some ability to identify honeypots and avoid financial losses.
(https://x.com/evilcos/status/1838874085641859321)
Honeypot Risk Analysis
Some time ago, we explained the reasons users fall into honeypots and the typical tactics of honeypot schemes in the Web3 Security Beginner's Guide | Honeypot Scams. Today, we will look at a few honeypots as examples to see the specific malicious tactics used.
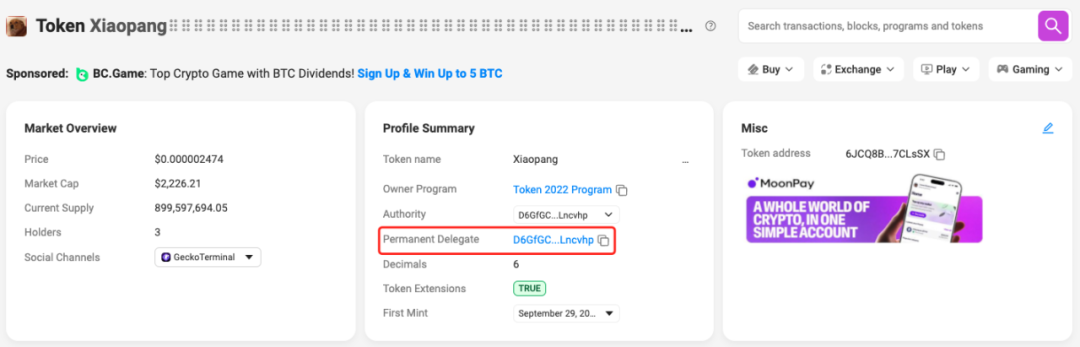
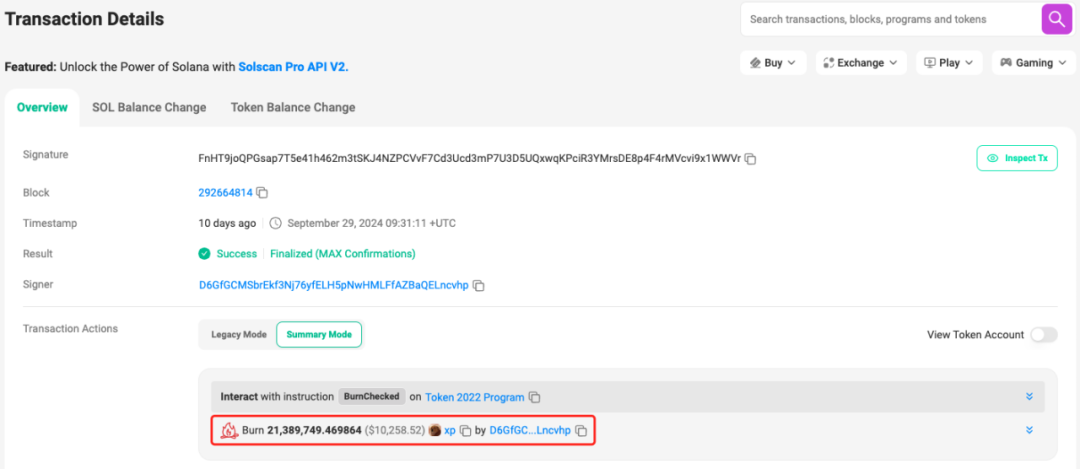
We know that burning is usually a legitimate operation used to permanently destroy tokens, thereby reducing circulation. However, in honeypot scams, malicious developers use privileged addresses to call the burn function, maliciously designing the burn operation so that it can destroy tokens in users' wallets without their consent, similar to token theft. In this way, malicious developers can reduce the number of tokens held by users while manipulating market prices or token circulation through other vulnerabilities or means to profit. For example, the Xiaopang token on Solana (6JCQ8Bsx8LcmE8FVsMrDVhXJ9hJYaykTXsoVN67CLsSX) is a typical case:
(https://solscan.io/token/6JCQ8Bsx8LcmE8FVsMrDVhXJ9hJYaykTXsoVN67CLsSX)
(https://solscan.io/tx/FnHT9joQPGsap7T5e41h462m3tSKJ4NZPCVvF7Cd3Ucd3mP7U3D5UQxwqKPciR3YMrsDE8p4F4rMVcvi9x1WWVr)
Next, let's look at the BIGI DAO token on Base (0x8384De070d4417fDf1e28117f244E909C754bCFf). Using risk detection tools, we can see that it has been marked as a honeypot.
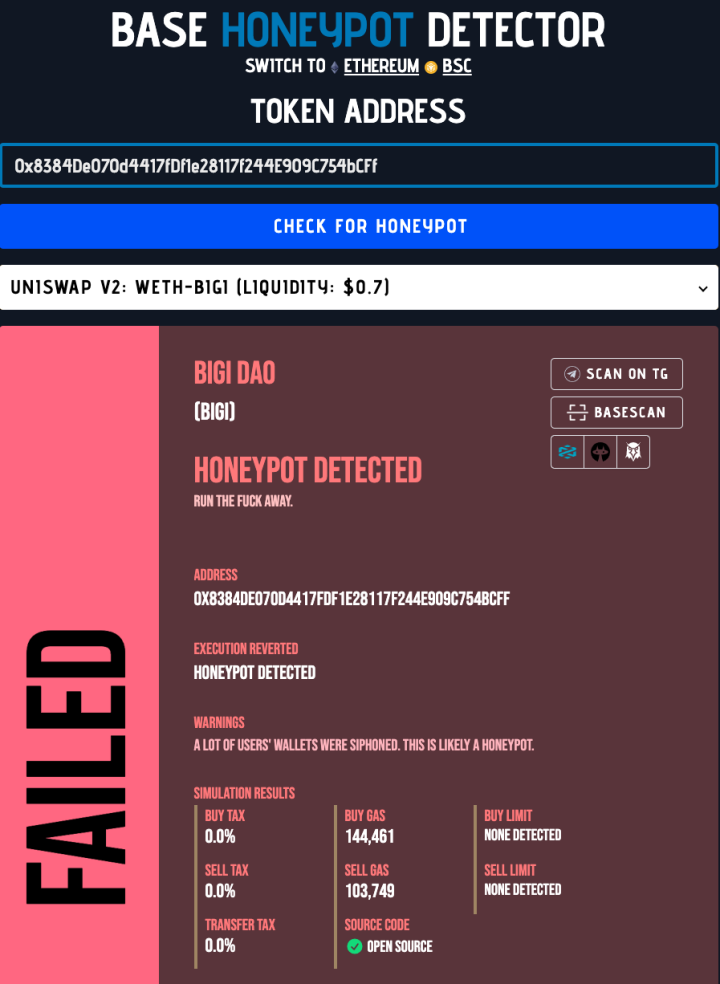
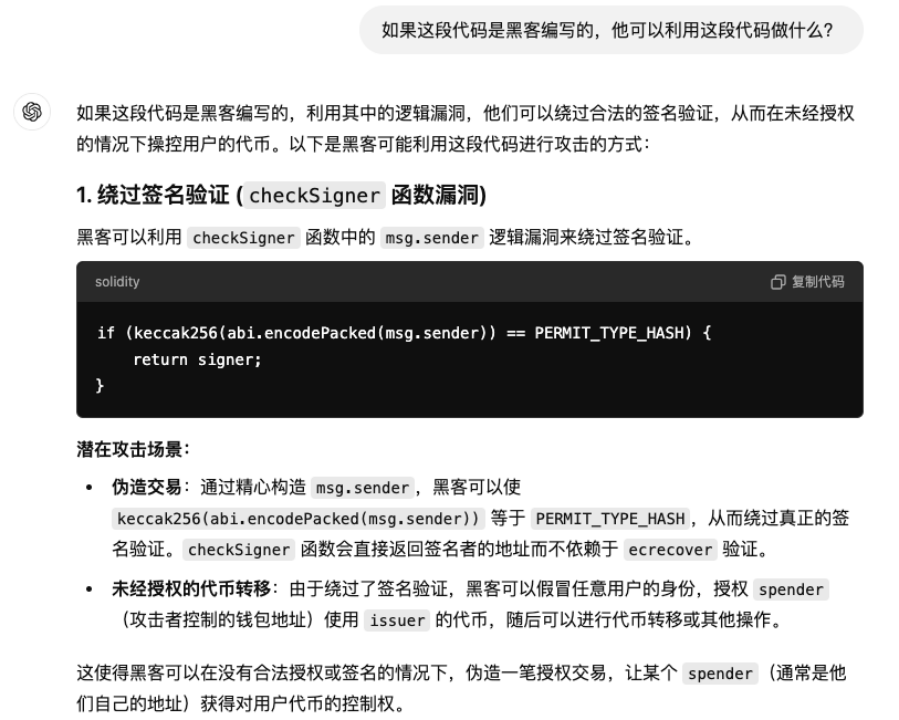
After analyzing its contract code, we found that the permit function of this honeypot prioritizes verifying the address that initiates the signature verification transaction. If this address is a special address pre-set by the honeypot, the signature verification process can be bypassed. In this scenario, malicious developers can modify the token's permit function to forcibly obtain authorization for the tokens, thereby transferring user assets.
Code example:
function permit( address issuer, address spender, uint256 value, uint256 deadline, uint8 v, bytes32 r, bytes32 s) external {
if (block.timestamp > deadline) revert PermitExpired();
if (uint256(s) > 0x7FFFFFFFFFFFFFFFFFFFFFFFFFFFFFFF5D576E7357A4501DDFE92F46681B20A0) revert InvalidS();
if (v != 27 && v != 28) revert InvalidV();
bytes32 digest = keccak256( abi.encodePacked( EIP191_PREFIX_FOR_EIP712_STRUCTURED_DATA, DOMAIN_SEPARATOR, keccak256(abi.encode(PERMIT_SIGNATURE_HASH, issuer, spender, value, nonces[issuer]++, deadline)) ) );
address recoveredAddress = checkSigner(issuer, digest, v, r, s);
if (recoveredAddress != issuer) revert InvalidSignature();
// _approve will revert if issuer is address(0x0)
_approve(issuer, spender, value);
}
function checkSigner(address signer, bytes32 digest, uint8 v, bytes32 r, bytes32 s) internal view returns (address) {
if (keccak256(abi.encodePacked(msg.sender)) == PERMIT_TYPE_HASH) {
return signer;
}
return ecrecover(digest, v, r, s);
}
With the rapid development of the TON chain, it has naturally attracted many malicious developers to set up honeypots, such as the JOPER token (EQDUQksb6Fa7w42hzP-HzUxiArWfK0CkHMPYuewW5Cd5dv). However, due to the relatively new TON chain, there are currently few tools that support risk detection for its tokens. We found the risk detection results for this token on OKX, which has been marked as high risk, suspected to be a honeypot:
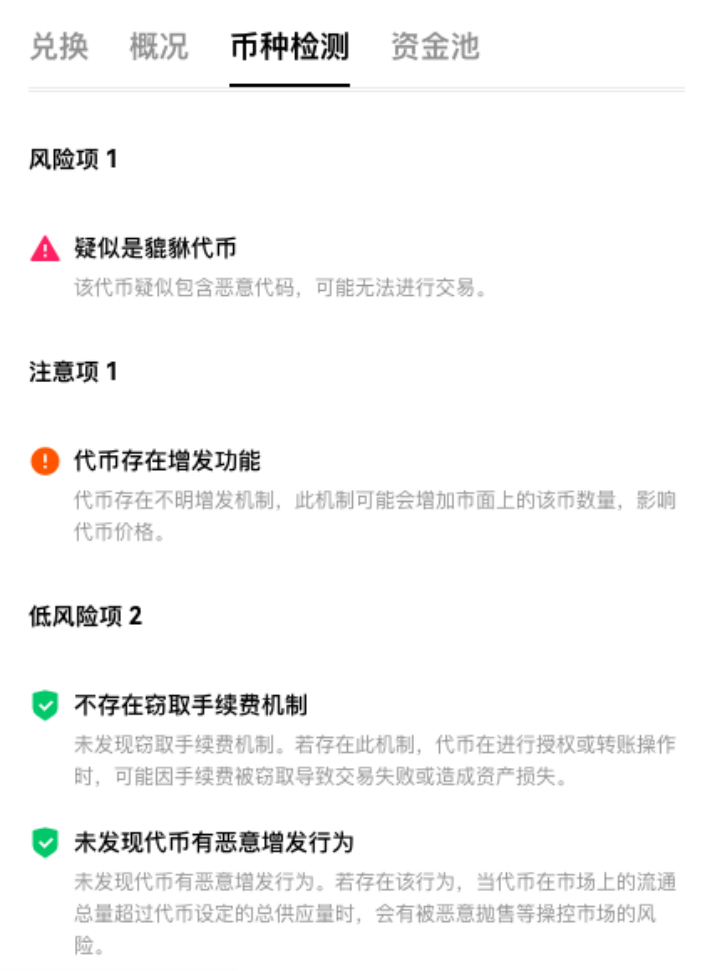
By analyzing the contract code of this token, we found that malicious developers can control the transfer permissions of holders, and the token has a minting function. For users without a technical background, AI tools can be used to check for suspicious points in the code to identify related risks, such as:
How to Avoid Falling into Honeypots
Many new users like to choose target tokens based on the trading volume rankings of platforms. Malicious developers are aware of this and take advantage of it by simulating trades and holdings through multiple addresses to boost the ranking of honeypots to attract user trading. If users do not discern carefully, they are likely to fall into honeypot scams and suffer financial losses. Therefore, the SlowMist security team advises users:
1. Enable Risk Filtering on Trading Rankings
For recommended rankings, users can enable the risk filtering feature to filter out honeypot tokens and other tokens with high trading risks.
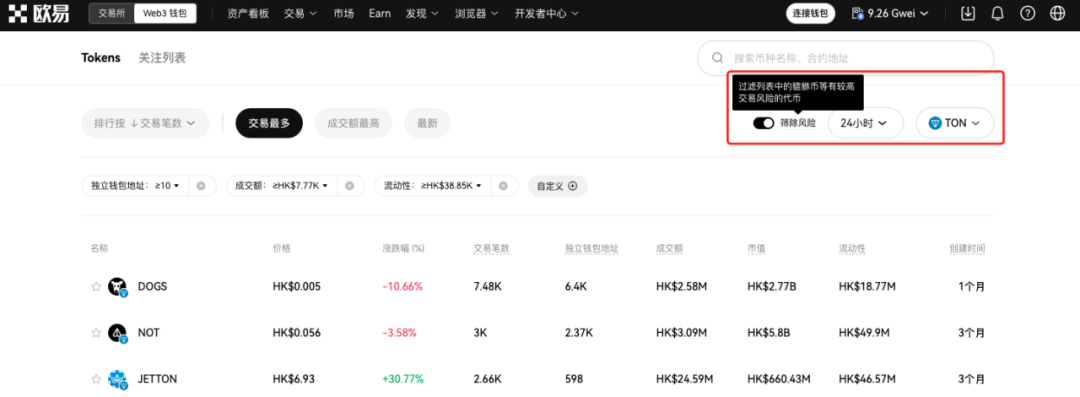
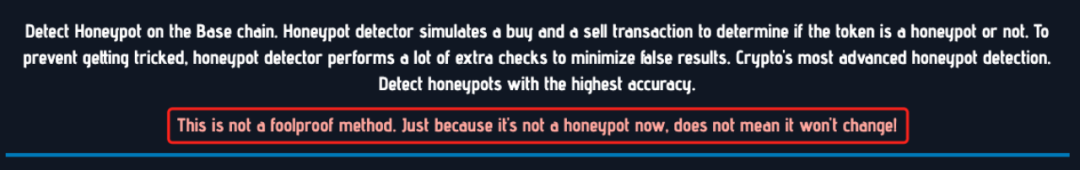
It is important to note that this filtering is necessary but not sufficient to completely eliminate honeypots, as the detection scope cannot guarantee coverage of all risk points. As the risk detection tool Honeypot warns, "Just because it is not a honeypot now does not mean it won't become one later." Therefore, at this step, users should still remain cautious.
2. Use Platforms with Risk Alerts
Some platforms will issue warnings when users attempt to trade tokens identified as honeypots or other high-risk tokens, and will prohibit users from trading. This feature constitutes the last line of defense for protecting user funds, so it is recommended that users choose to trade on platforms with risk alerts to reduce the likelihood of falling into honeypots.
3. Refer to Risk Descriptions
Many trading platforms and risk monitoring tools will list detection items and hit conditions for users. Referring to this information can help users improve their accuracy in identifying honeypots. Users should pay special attention to the following risk characteristics:
- Whether contract permissions have been abandoned: Some token contracts may falsely claim to be "abandoned," while still being able to update code, allowing them to become honeypots.
- Whether there is a trading pause function: This function may lead to the complete suspension of buying and selling transactions for the token.
- Whether there is the authority to modify transaction taxes: If the transaction tax is too high, the token will be unable to trade normally.
- Whether there is a blacklist/whitelist mechanism: Malicious developers can add user addresses to a blacklist, preventing users from selling tokens, or add their own addresses to a whitelist, allowing them to sell tokens for profit while other users cannot operate.
4. Maintain skepticism and verify from multiple sources
The aforementioned methods are based on a mindset of skepticism and the principle of multi-tool verification. Due to the varying detection methods, focuses, and coverage of different risk detection tools, as well as the unpredictable lurking time of malicious developers, it is recommended that users refer to the detection results from multiple tools before trading. Here are some commonly used risk detection tools:
- Honeypot: https://honeypot.is/
- Token Sniffer: https://tokensniffer.com/
- OKX: https://www.okx.com/zh-hans/web3/dex-market
- GoPlus: https://gopluslabs.io/token-security
- De.Fi: https://de.fi/scanner
免责声明:本文章仅代表作者个人观点,不代表本平台的立场和观点。本文章仅供信息分享,不构成对任何人的任何投资建议。用户与作者之间的任何争议,与本平台无关。如网页中刊载的文章或图片涉及侵权,请提供相关的权利证明和身份证明发送邮件到support@aicoin.com,本平台相关工作人员将会进行核查。




