Original | Odaily Planet Daily (@OdailyChina)

Around 11 PM Beijing time last night, on-chain analysis firm Lookonchain detected an unusual transaction where a certain address (0xA7A1c66168cC0b5fC78721157F513c89697Df10D) received approximately 1.67 million EIGEN from the Eigenlayer team address and then directly sold it off at a price of $3.3, cashing out about $5.51 million.
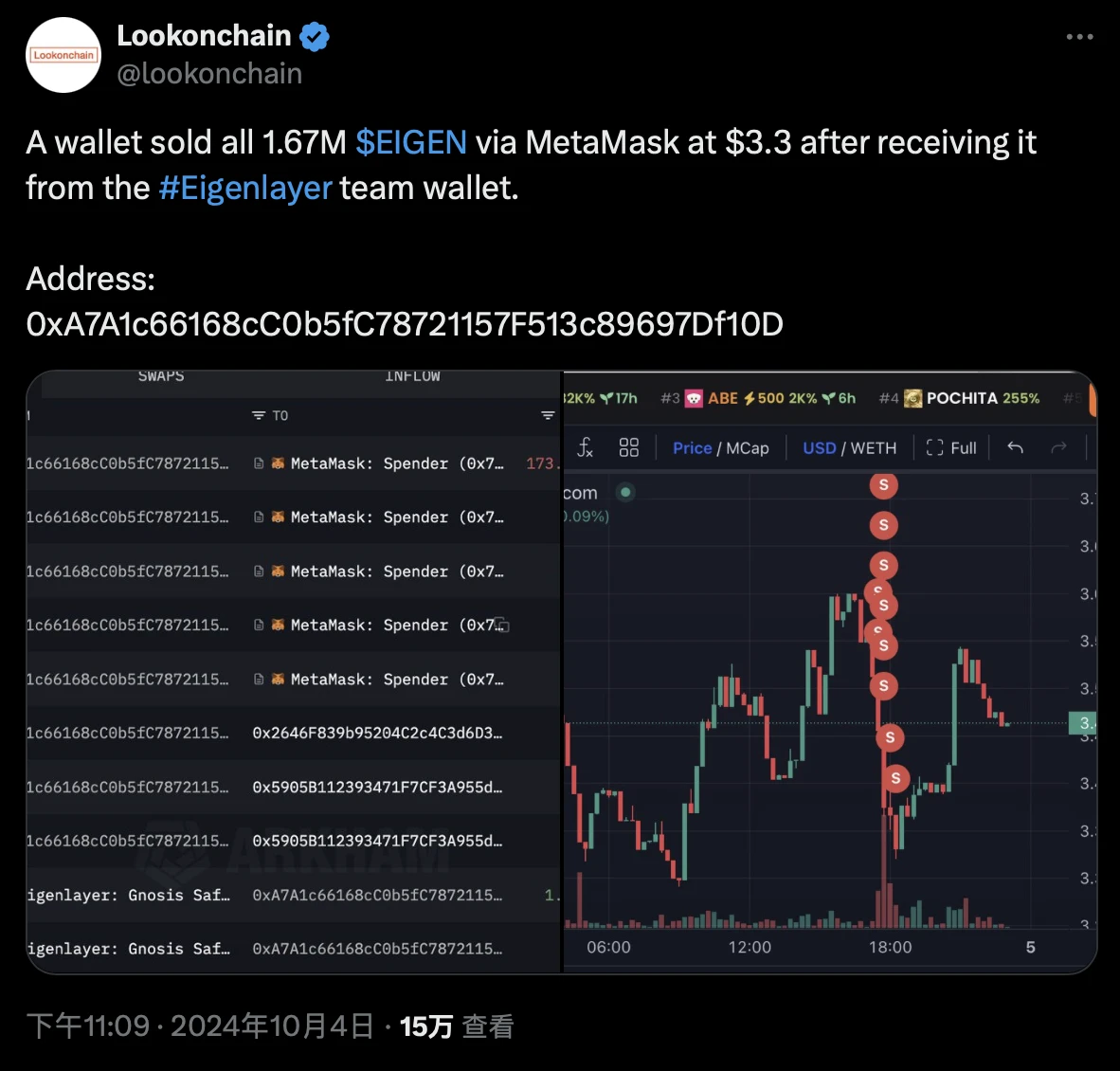
After this transaction was exposed, voices of doubt arose within the community — EIGEN had just lifted its transfer restrictions a few days ago, and the team blatantly dumped the tokens like this?
Around 5:30 AM this morning, EigenLayer provided an official response to the community's concerns.
This morning, an isolated incident occurred where an investor's email regarding transferring tokens to a custody address was hijacked by malicious attackers, who replaced the specific address in the email, resulting in 1,673,645 EIGEN being incorrectly transferred to the attacker's address. The attacker has sold the stolen EIGEN through decentralized exchanges and transferred the stablecoins to centralized exchanges. We are in contact with these platforms and law enforcement. Some of the funds have already been frozen.
This breach did not affect the Eigenlayer system, and there are no known vulnerabilities in the protocol or token contracts; this incident is unrelated to any on-chain functionality of EigenLayer.
We are still investigating this situation, and we will continue to disclose further information as it becomes available.
The attack itself is not complex; well-known security expert and SlowMist founder Yuxian provided a detailed analysis on his personal X account.
Regarding this attack, the attacker likely premeditated for quite some time. The attacker's address first received 1 EIGEN, and about 26 hours later received 1,674,644 EIGEN, all from a 3/5 multi-signature address (0x87787389BB2Eb2EC8Fe4aA6a2e33D671d925A60f). Then, over an hour later, various laundering activities began. Gas fees came from ChangeNow, and the illegally obtained EIGEN was mainly exchanged for USDC/USDT, primarily laundered through platforms like HitBTC.
The official explanation for the attacker's success is that "the email was compromised." It is estimated that in the email content, the expected receiving wallet address for EIGEN was replaced with the attacker's address, leading the project team to send EIGEN to the attacker's address. Even if they initially sent 1 EIGEN, the attacker might have sent 1 EIGEN to the expected receiving address after receiving 1 EIGEN, causing the expected recipient to believe the entire process was correct… Of course, this is just speculation; the specifics should be based on official disclosures.
However, behind this "ordinary" security incident lies a more serious issue — why can EigenLayer's investors receive EIGEN tokens now? And why can the receiving addresses (whether investors or hackers) sell off EIGEN directly without any restrictions after receiving them?
In the token economic model previously disclosed by EigenLayer, the portion regarding early contributors and investors clearly emphasized "a one-year lock-up restriction."
After the transfer restrictions on the EIGEN contract are lifted, the tokens of early contributors, investors, and service providers of the Eigen Foundation will be locked for one year. After one year, 4% of the EIGEN for each recipient will be unlocked, with an additional 4% unlocked each month thereafter.
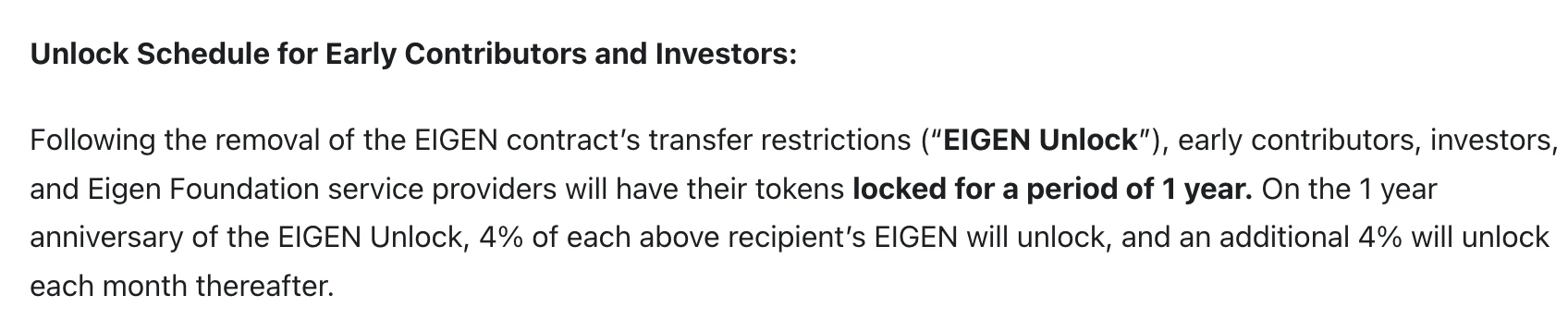
As a project with over a hundred million in funding, a high TVL ranking across the ecosystem, and major exchanges competing to list it… it is hard to imagine that EigenLayer neither chose to use the currently mature token distribution protocols nor deployed its own token unlocking contract, but rather "thoughtlessly" sent tokens to investor addresses immediately after the transfer restrictions were lifted…
From the hacker's selling behavior, it appears that these addresses faced no hard operational restrictions after receiving the tokens, in other words, EigenLayer seems to be relying on VCs to "morally lock up" their tokens…
Even more absurdly, it seems that EigenLayer did not cross-verify the email from the "investor" (who was actually the hacker) through a phone call or any other means, but directly released the tokens, which led to the hacker successfully stealing millions of dollars…
In summary, this entire incident is filled with points of contention. If EigenLayer had executed normal token unlocking protocols, and if the EigenLayer team's operational quality had been even slightly competent, this hacking incident would not have occurred, and EigenLayer would not have been criticized by the community as a "shoddy operation."
From a technical perspective, EigenLayer's innovative "re-staking" narrative expands the boundaries of node validation services, utilizing AVS to extend node validation services, originally only used for network consensus maintenance, to more segmented scenarios such as oracles, sequencers, and cross-chain bridges. This has long-term utility significance for the Ethereum ecosystem and the entire cryptocurrency market.
But technology is one thing, and operations are another. From past controversies over "team members requesting airdrops from ecosystem projects" to the current "unlocking storm," EigenLayer's outrageous operations are gradually eroding community trust. For any project, no matter how large its scale, this is an extremely dangerous signal.
免责声明:本文章仅代表作者个人观点,不代表本平台的立场和观点。本文章仅供信息分享,不构成对任何人的任何投资建议。用户与作者之间的任何争议,与本平台无关。如网页中刊载的文章或图片涉及侵权,请提供相关的权利证明和身份证明发送邮件到support@aicoin.com,本平台相关工作人员将会进行核查。




