Author: Sam Kessler, Coindesk
Translation: Joy, PANews
Key Points:
- CoinDesk discovered that more than a dozen cryptocurrency companies unknowingly employed IT workers from North Korea, including well-known blockchain projects such as Injective, ZeroLend, Fantom, Sushi, Yearn Finance, and Cosmos Hub.
- These employees used fake IDs, successfully passed interviews, cleared qualification checks, and provided real work experience.
- Hiring North Korean workers is illegal in the U.S. and other countries that sanction North Korea. This also poses security risks, as CoinDesk found that multiple companies that hired North Korean IT workers were subsequently hacked.
- Noted blockchain developer Zaki Manian stated, "Everyone is trying to filter these people out." He mentioned that he inadvertently hired two North Korean IT workers in 2021 to help develop the Cosmos Hub blockchain.
In 2023, the cryptocurrency company Truflation was still in its early stages when founder Stefan Rust unknowingly hired the first North Korean employee.
"We were looking for great developers," Rust said from his home in Switzerland. Unexpectedly, "this developer came to us."
"Ryuhei" sent his resume via Telegram, claiming to work in Japan. Shortly after being hired, strange contradictions began to surface.
At one point, "I was on a call with that person, and he said he encountered an earthquake," Rust recalled. But there hadn't been an earthquake in Japan recently. Then, the employee started missing calls, and when he did show up, "it wasn't him," Rust said. "It was someone else." Whoever it was, they had lost the Japanese accent.
Rust soon learned that "Ryuhei" and four other employees (more than a third of his team) were all North Koreans. Rust had inadvertently fallen into an organized scheme by North Korea, which aimed to provide its workers with remote overseas jobs and funnel the income back to Pyongyang.
U.S. authorities have recently intensified warnings that North Korean IT workers are infiltrating tech companies, including cryptocurrency employers, and using the proceeds to fund the country's nuclear weapons program. According to a 2024 United Nations report, these IT workers earn North Korea up to $600 million annually.
Hiring and paying these workers' salaries—even unintentionally—violates United Nations sanctions and is illegal in the U.S. and many other countries. This also poses serious security risks, as it is well-known that North Korean hackers attack companies by secretly employing staff.
A CoinDesk investigation revealed the eagerness and frequency of North Korean job seekers targeting cryptocurrency companies—successfully passing interviews, background checks, and even showcasing impressive code contribution histories on the open-source software repository GitHub.
CoinDesk interviewed over a dozen cryptocurrency companies, all of which stated that they had unknowingly hired IT workers from North Korea.
Interviews with founders, blockchain researchers, and industry experts indicated that North Korean IT workers are far more prevalent in the crypto industry than previously thought. Almost every hiring manager interviewed for this article acknowledged that they had interviewed suspected North Korean developers, unknowingly hired them, or knew someone who had.
Noted blockchain developer Zaki Manian stated, "The proportion of resumes, job seekers, or contributors from North Korea in the entire crypto industry may exceed 50%." He mentioned that he inadvertently hired two North Korean IT employees in 2021 to help develop the Cosmos Hub blockchain. "Everyone is trying to filter these people out."
Among the unaware North Korean employers discovered by CoinDesk were several well-known blockchain projects, such as Cosmos Hub, Injective, ZeroLend, Fantom, Sushi, and Yearn Finance. "All of this is happening behind the scenes," Manian said.
This investigation marks the first time these companies have publicly acknowledged that they inadvertently hired North Korean IT employees.
In many cases, North Korean workers operated like regular employees; thus, in a sense, employers essentially received the deliverables for which they paid. However, CoinDesk found evidence suggesting that these employees subsequently funneled their salaries to blockchain addresses linked to the North Korean government.
CoinDesk's investigation also uncovered several cases where cryptocurrency projects that employed North Korean IT workers were later hacked. In some of these cases, the thefts could be directly linked to suspected North Korean IT employees on the company's payroll. Sushi was one such case, a well-known DeFi protocol that lost $3 million in a hacking incident in 2021.
The U.S. Treasury Department's Office of Foreign Assets Control (OFAC) and the Department of Justice began publishing information in 2022 about North Korea's attempts to infiltrate the U.S. cryptocurrency industry. Evidence uncovered by CoinDesk suggests that North Korean IT workers had already begun working under false identities in cryptocurrency companies as early as 2018.
"I think a lot of people mistakenly believe this is something that happened suddenly," Manian said. "The GitHub accounts and other things of these people can be traced back to 2016, 2017, 2018." (GitHub, owned by Microsoft, is an online platform used by many software organizations to host code and allow developers to collaborate.)
CoinDesk used various methods to connect North Korean IT workers to companies, including blockchain payment records, public GitHub code contributions, emails from U.S. government officials, and direct interviews with target companies. One of the largest payment networks in North Korea investigated by CoinDesk was identified by blockchain investigator ZachXBT, who released a list of suspected North Korean developers in August. Link
Previously, employers had remained silent due to concerns about unnecessary exposure or legal repercussions. Now, faced with the extensive payment records and other evidence unearthed by CoinDesk, many of them have decided to come forward to share their stories for the first time, revealing the significant success and scale of North Korea's infiltration into the cryptocurrency industry.
Forged Documents
After hiring Ryuhei, who appeared to be a Japanese employee, Rust's Truflation received a flood of new applications. Within a few months, Rust unknowingly hired four more North Korean developers, who claimed to be based in Montreal, Vancouver, Houston, and Singapore.
The cryptocurrency industry is particularly vulnerable to North Korean IT workers. The labor distribution in the crypto industry is highly globalized, and compared to other companies, crypto firms are often more willing to hire fully remote (and even anonymous) developers.
CoinDesk reviewed job applications from North Korea received by cryptocurrency companies from various sources, including messaging platforms like Telegram and Discord, cryptocurrency-specific job boards like Crypto Jobs List, and recruitment websites like Indeed.
"They are most likely to be hired by those really fresh, emerging teams that are willing to hire from Discord," said Taylor Monahan, product manager at the crypto wallet app MetaMask, who frequently publishes security research related to North Korean crypto activities. "They haven't established processes to hire people who have undergone background checks. Many times, they are willing to pay in cryptocurrency."
Rust stated that he conducted background checks on all new employees at Truflation. "They sent us their passports and IDs, provided us with GitHub code repositories, took tests, and then basically we hired them."

An applicant submitted a Texas driver's license as identification to the cryptocurrency company Truflation, and the applicant is currently suspected to be a North Korean citizen. CoinDesk has redacted some details because North Korean IT workers have used stolen identification documents. (Image provided by Stefan Rust)
To the untrained eye, most forged documents are difficult to distinguish from real passports and visas, but experts told CoinDesk that professional background check services are likely to uncover these forged documents.
 One of the suspected North Korean IT workers confirmed by ZachXBT, "Naoki Murano," provided the company with a seemingly authentic Japanese passport. (Image provided by Taylor Monahan)
One of the suspected North Korean IT workers confirmed by ZachXBT, "Naoki Murano," provided the company with a seemingly authentic Japanese passport. (Image provided by Taylor Monahan)
Although startups are unlikely to use professional background check personnel, "we do see North Korean IT personnel in large companies, either as actual employees or at least as contractors," Monahan said.
Hiding in Plain Sight
In many cases, CoinDesk found that North Korean IT workers used public blockchain data.
In 2021, blockchain developer Manian's company Iqlusion needed some help. He was looking for freelance programmers who could assist in upgrading the popular Cosmos Hub blockchain. He found two new employees; they performed excellently.
Manian never met the freelancers "Jun Kai" and "Sarawut Sanit" in person. They had previously collaborated on an open-source software project funded by the closely related blockchain network THORChain, and they told Manian they were in Singapore.
"For a year, I spoke with them almost every day," Manian said. "They completed the work. Frankly, I was very satisfied."
Two years after these freelancers completed their work, Manian received an email from an FBI agent who was investigating token transfers that appeared to come from Iqlusion, which were sent to suspected North Korean crypto wallet addresses. The transfers in question turned out to be payments Iqlusion made to Kai and Sanit.
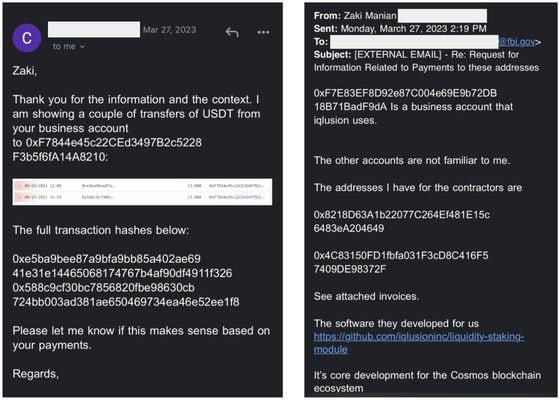
Left Image: An FBI agent (name redacted) requested Zaki Manian to provide information about two blockchain payments from his company Iqlusion. Right Image: Manian informed the agent that these transactions were made between Iqlusion and several contractors.
The FBI never confirmed to Manian that the developers he contracted were North Korean agents, but CoinDesk's review of the blockchain addresses associated with Kai and Sanit showed that during 2021 and 2022, they funneled income to two individuals on the OFAC sanctions list: Kim Sang Man and Sim Hyon Sop.
According to OFAC, Sim is a representative of the North Korean Foreign Trade Bank, which launders funds for IT workers to help "finance North Korea's weapons of mass destruction and ballistic missile programs." Sarawut appears to have sent all his income to blockchain wallets associated with Sim and others linked to him.
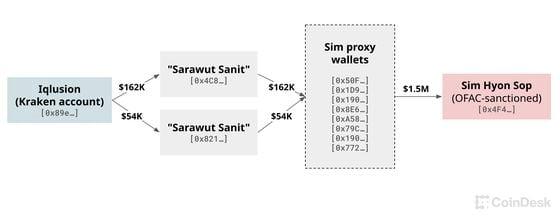
Blockchain records from April to December 2022 show that "Sarawut Sanit" sent all his salary to wallets associated with OFAC-designated North Korean agent Sim Hyon Sop. (Ethereum wallets tracked by CoinDesk. Asset prices estimated by Arkham.)
Meanwhile, Kai directly remitted nearly $8 million to Kim here. According to a 2023 OFAC advisory report, Kim is a representative of Chinyong Information Technology Cooperation, which operates in North Korea and "employs a delegation of North Korean IT workers in Russia and Laos through its controlled companies and representatives."
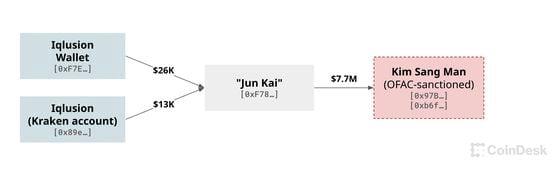
In 2021, "Jun Kai" sent $7.7 million in cryptocurrency directly to blockchain addresses on the OFAC sanctions list associated with Kim Sang Man. (Ethereum wallets tracked by CoinDesk. Asset prices estimated by Arkham.)
Iqlusion's salary to Kai accounted for less than $50,000 of the nearly $8 million he sent to Kim, with the remainder coming from other cryptocurrency companies.
For instance, CoinDesk found that the Fantom Foundation, which develops the widely used Fantom blockchain, made payments to "Jun Kai" and another developer linked to North Korea.
A spokesperson for the Fantom Foundation told CoinDesk, "Fantom does confirm that two external individuals were involved with North Korea in 2021. However, the developers in question were involved in an external project that was never completed and never deployed."
According to the Fantom Foundation, "The two employees involved have been terminated, and they never contributed any malicious code nor accessed Fantom's codebase, and Fantom's users were not affected." The spokesperson noted that a North Korean employee attempted to attack Fantom's servers but failed due to a lack of necessary access.
According to the OpenSanctions database, Kim's blockchain addresses related to North Korea were not publicly disclosed by the government until May 2023, more than two years after the payments to Iqlusion and Fantom.
Giving Leeway
The U.S. and the United Nations imposed sanctions on hiring North Korean IT workers in 2016 and 2017, respectively.
Whether knowingly or not, paying wages to North Korean workers in the U.S. is illegal—a legal concept known as "strict liability."
The location of the company does not matter: hiring North Korean workers poses legal risks for any company operating in countries that sanction North Korea.
However, U.S. and other UN member states have yet to prosecute cryptocurrency companies for employing North Korean IT workers.
The U.S. Treasury Department investigated Iqlusion, based in the U.S., but Manian stated that no penalties were imposed at the end of the investigation.
U.S. authorities have been lenient in bringing charges against these companies—acknowledging to some extent that these companies faced an unusually complex and sophisticated identity fraud, or at worst, a long-running and humiliating scam.
In addition to legal risks, MetaMask's Monahan explained that paying North Korean IT workers is also "bad because the people you are paying are essentially exploited by the regime."
According to a 615-page report from the UN Security Council, North Korean IT workers can only keep a small portion of their wages. The report states, "Low-income workers retain 10%, while high-income workers can retain 30%."
While these wages may still be high relative to the average in North Korea, "I don't care where they live," Monahan said. "If I pay someone, and they are forced to send all their salary to their boss, that makes me very uncomfortable. If their boss is the North Korean regime, that makes me even more uncomfortable."
CoinDesk reached out to several suspected North Korean IT workers during the reporting process but did not receive any responses.
The Future
CoinDesk identified over 20 companies that may have employed North Korean IT workers by analyzing blockchain payment records of OFAC-sanctioned entities. Twelve companies that submitted relevant records confirmed to CoinDesk that they had previously identified suspected North Korean IT workers on their payroll.
Some declined to comment further due to concerns about legal repercussions, but others agreed to share their stories in the hope that others could learn from their experiences.
In many cases, North Korean employees were easier to identify after being hired.
Eric Chen, CEO of Injective, a project focused on decentralized finance, stated that he contracted a freelance developer in 2020 but quickly fired him due to poor performance.
"He didn't last long," Chen said. "The code he wrote was terrible and ineffective." It wasn't until last year, when a "government agency" in the U.S. contacted Injective, that Chen learned the employee had ties to North Korea.
Several companies told CoinDesk that they had fired an employee for quality of work before learning of any connection to North Korea.
"Months of Payroll"
However, North Korean IT workers are similar to typical developers, with varying abilities.
Manian noted that on one hand, you have some employees "coming into the company, going through the interview process, and earning several months' salary." "On the other hand, when you interview these people, you find that their actual technical skills are really strong."
Rust recalled encountering "a very talented developer" at Truflation who claimed to be from Vancouver but was later found to be from North Korea. "He was really a young guy," Rust said. "It felt like he had just graduated from college. A bit green, very eager, and excited to have the opportunity to work."
Another example is that the DeFi startup Cluster fired two developers in August after ZachXBT provided evidence linking them to North Korea.
Cluster's anonymous founder z3n told CoinDesk, "These people knew too much; it was unbelievable." In hindsight, there were some "obvious red flags." For instance, "they would change their payment addresses every two weeks and change their Discord or Telegram names about once a month."
Cameras Off
In conversations with CoinDesk, many employers noted that when they learned their employees might be North Korean, certain anomalies made more sense.
Sometimes these hints were subtle, such as discrepancies between employees' working hours and their supposed locations.
Other employers, like Truflation, noticed that employees might be impersonated by multiple people, with employees hiding this by turning off their cameras. (They were almost all male.)
One company hired an employee who attended morning meetings but seemed to forget everything discussed later that day, even though she had previously spoken with many people, making this quirk more significant.
When Rust expressed his concerns about the "Japanese" employee Ryuhei to an investor with experience tracking criminal payment networks, the investor quickly identified four other suspected North Korean IT workers on Truflation's payroll.
“We immediately cut off contact,” Rust stated, adding that his team conducted a security audit of their code, enhanced background check processes, and changed certain policies. One new policy requires remote workers to turn on their cameras.
$3 Million Hack
Many employers consulted by CoinDesk mistakenly believed that North Korean IT workers operated independently from North Korean hacking units, but blockchain data and conversations with experts indicate that North Korean hacking activities are often linked with IT workers.
In September 2021, MISO, a platform established by Sushi for issuing cryptocurrency tokens, lost $3 million in a theft incident. CoinDesk found evidence suggesting that this attack was related to two developers hired by Sushi, whose blockchain payment records were associated with North Korea.
At the time of the hack, Sushi was one of the most prominent platforms in the emerging DeFi space. SushiSwap had over $5 billion in deposits and primarily served as a "decentralized exchange" for people to trade cryptocurrencies without intermediaries.
At that time, Sushi's Chief Technology Officer Joseph Delong traced the MISO theft back to two freelance developers involved in the platform's development: they used the names Anthony Keller and Sava Grujic. Delong stated that these developers (whom he now suspects to be the same person or organization) injected malicious code into the MISO platform, transferring funds to wallets they controlled.
When Keller and Grujic were hired to manage the decentralized autonomous organization Sushi DAO, they provided credentials that were sufficiently typical or even impressive for entry-level developers.
Keller publicly used the alias “eratos1122,” but when he applied for the MISO job, he used a name that appeared to be his real name, “Anthony Keller.” In the resume shared by Delong with CoinDesk, Keller claimed to reside in Gainesville, Georgia, and graduated from the University of Phoenix with a bachelor's degree in computer engineering. (The university did not respond to requests about whether there were any graduates with that name.)

“Anthony Keller” claims to reside in Gainesville, Georgia, and lists his experience working on the popular decentralized finance application Yearn in his resume.
Keller's resume did mention previous work, with the most impressive being Yearn Finance, a very popular crypto investment protocol that offers users a way to earn interest through a series of investment strategies. Banteg, a core developer at Yearn, confirmed that Keller was involved in developing Coordinape, an application created by Yearn to facilitate team collaboration and payments. (Banteg stated that Keller's work was limited to Coordinape, and he did not have access to Yearn's core codebase.)
According to Delong, Keller introduced Grujic to MISO, and the two claimed to be "friends." Like Keller, Grujic's resume listed his real name rather than his online pseudonym “AristoK3.” He claimed to be from Serbia, graduated from the University of Belgrade with a bachelor's degree in computer science, and had an active GitHub account listing his experience in several smaller crypto projects and gaming startups.

In his resume, “Sava Grujic” lists 5 years of programming experience and claims to be based in Belgrade, Serbia.
Rachel Chu, a former core developer at Sushi who worked closely with Keller and Grujic before the theft incident, stated that she had already developed "suspicions" about the two before the hack occurred.
Despite being far apart, Grujic and Keller "had the same accent" and "texted in the same way," Chu said. "Every time we had a call, there would be some background noise, like in a factory," she added. Chu recalled seeing Keller's face but never Grujic's. According to Chu, Keller's camera was "zoomed in," so she couldn't see what was behind him at all.
Grujic and Keller ultimately stopped contributing to MISO at the same time. "We thought they were the same person," Delong said, "so we stopped paying them." This was during the height of the COVID-19 pandemic, and it was not uncommon for remote cryptocurrency developers to impersonate multiple people to earn extra income from the payroll.
After Grujic and Keller were fired in the summer of 2021, the Sushi team neglected to revoke their access to the MISO codebase.
According to a screenshot obtained by CoinDesk, on September 2, Grujic submitted malicious code to the MISO platform under his alias “Aristok3,” transferring $3 million to a new cryptocurrency wallet.
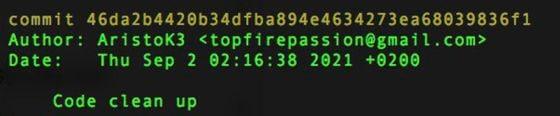 “Sava Grujic” submitted contaminated code to Sushi's MISO using the alias AristoK3. (Screenshot provided by Joseph Delong)
“Sava Grujic” submitted contaminated code to Sushi's MISO using the alias AristoK3. (Screenshot provided by Joseph Delong)
Analysis of blockchain payment records by CoinDesk suggests a possible connection between Grujic, Keller, and North Korea. In March 2021, Keller posted a blockchain address in a now-deleted tweet. CoinDesk discovered that there were multiple payments between this address, Grujic's hacker address, and the archived Keller address from Sushi. According to Delong, Sushi's internal investigation ultimately concluded that the address belonged to Keller.
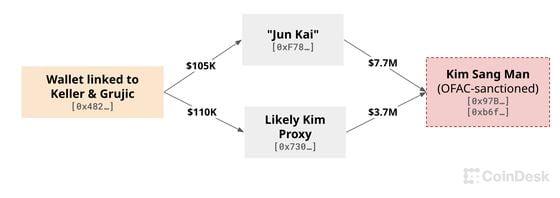
_During 2021 to 2022, blockchain addresses linked to Keller and _Grujic_ sent most of their funds to wallets associated with North Korea. (Ethereum wallets tracked by CoinDesk. Asset prices estimated by Arkham.)_
CoinDesk found that this address sent most of its funds to “Jun Kai” (an Iqlusion developer who remitted to OFAC-sanctioned Kim Sang Man) and another wallet that appeared to act as a North Korean proxy (as it also paid Kim).
Sushi's internal investigation found that _Keller and _Grujic frequently operated using IP addresses from Russia, further corroborating claims that they were North Koreans. OFAC stated that North Korean IT workers are sometimes stationed in Russia. (The U.S. phone number on Keller's resume is no longer in service, and his “eratos1122” GitHub and Twitter accounts have also been deleted.)
Additionally, CoinDesk found evidence suggesting that Sushi hired another suspected North Korean IT contractor while employing Keller and Grujic. ZachXBT identified this developer as “Gary Lee,” who coded under the alias LightFury and funneled income to “Jun Kai” and another address associated with Kim.
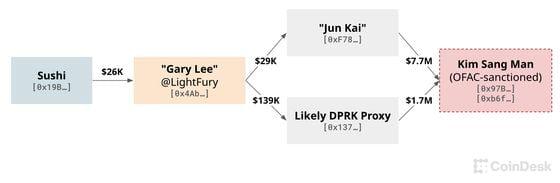
From 2021 to 2022, Sushi also employed another individual who was clearly a North Korean contractor named “Gary Lee.” This worker funneled his income from 2021 to 2022 to blockchain addresses related to North Korea, including the wallet used by Iqlusion's “Jun Kai.” (Ethereum wallets tracked by CoinDesk. Asset prices estimated by Arkham.)
After Sushi publicly blamed the attack on Keller's alias “eratos1122” and threatened to involve the FBI, Grujic returned the stolen funds. While it may seem counterintuitive for North Korean IT workers to care about protecting their aliases, they appear to reuse certain names and build their reputations by contributing to many projects, perhaps to gain the trust of future employers.
One might think that protecting the alias Anthony Keller would be more profitable in the long run: in 2023, two years after the Sushi incident, a person named “Anthony Keller” applied to Stefan Rust's company Truflation.
CoinDesk attempted to contact “Anthony Keller” and “Sava Grujic” for comments but was unsuccessful.
North Korean-style Heists
According to the United Nations, North Korea has stolen over $3 billion in cryptocurrency through hacking over the past seven years. In the first half of 2023, blockchain analysis firm Chainalysis tracked 15 hacks related to North Korea, “about half of which involved thefts associated with IT workers,” said company spokesperson Madeleine Kennedy.
North Korean cyberattacks are not like the Hollywood version of hacking, where hoodie-wearing programmers use complex computer code and black-green computer terminals to infiltrate mainframes.
North Korean-style attacks are evidently lower in technical sophistication. They often involve some form of social engineering, where attackers gain the trust of victims holding system keys and then extract those keys directly through simple means like malicious email links.
Monahan said, “So far, we have never seen North Korea carry out a real attack. They always start with social engineering attacks, then compromise devices, and finally steal private keys.”
IT workers are well-suited to contribute to North Korea's heists, either by obtaining personal information that can be used to compromise potential targets or by directly accessing software systems filled with digital cash.
A Series of Coincidences
On September 25, just as this article was about to be published, CoinDesk arranged a video call with Rust from Truflation. The plan was to verify some details he had previously shared.
A flustered Rust joined the call 15 minutes late. He had just been hacked.
CoinDesk contacted over 20 projects that appeared to have unwittingly hired North Korean IT staff. In just the last two weeks of interviews, two of those projects were hacked: Truflation and a cryptocurrency lending application called Delta Prime.
It is still too early to determine whether these two hacking incidents are directly linked to the unintentional hiring of North Korean IT workers.
On September 16, Delta Prime was first breached. CoinDesk previously discovered payments and code contributions between Delta Prime and Naoki Murano, one of the developers promoted by anonymous blockchain detective ZachXBT as being linked to North Korea.
The project lost over $7 million, with the official explanation being that “the private keys were leaked.” Delta Prime did not respond to multiple requests for comment.
Less than two weeks later, the Truflation hack followed. About two hours before the call with CoinDesk, Rust noticed funds flowing out of his crypto wallet. He had just returned from a business trip to Singapore and was trying to figure out what he had done wrong. “I just don’t know how this happened,” he said. “I locked my laptop in the hotel safe. I always had my phone with me.”
As Rust spoke, millions of dollars were flowing out of his personal blockchain wallet. “I mean, this is really bad. This money is for my kids' tuition and retirement.”
Truflation and Rust ultimately lost about $5 million. The official cause of the loss was determined to be the theft of private keys.
免责声明:本文章仅代表作者个人观点,不代表本平台的立场和观点。本文章仅供信息分享,不构成对任何人的任何投资建议。用户与作者之间的任何争议,与本平台无关。如网页中刊载的文章或图片涉及侵权,请提供相关的权利证明和身份证明发送邮件到support@aicoin.com,本平台相关工作人员将会进行核查。




