This article's Hash (SHA1): 418ea6548326a5f3b9496aa7912935fec8ca925c
Number: Chain Source Technology PandaLYSecurity Knowledge No.031
What is a blockchain phishing attack?
You may be familiar with the term "phishing." Initially, it referred to the online scam that induced people to click on links through counterfeit websites or emails and then deceive them into providing personal information. Now, with the popularity of blockchain and cryptocurrency, this "phishing" has evolved into the world of blockchain.
In essence, blockchain phishing attacks are similar to traditional phishing. Attackers pretend to be someone you trust, such as a wallet website you frequently use, a trading platform, or even a project you have participated in. They may use forged links, fake social media accounts, or seemingly legitimate but actually flawed smart contracts to entice you to input your private key, mnemonic phrase, or sign a malicious transaction. The result? Your encrypted assets are unknowingly transferred away.
For example, imagine seeing an "official airdrop" activity on a social platform, with a link that looks like a familiar wallet website. You enter your mnemonic phrase and then realize that all your funds are gone. This is a typical scenario of a blockchain phishing attack.
Phishing attacks are particularly cunning because they specifically target users who are not very familiar with blockchain technology and are not well-versed in protective measures. Many people have fallen into the trap due to momentary negligence or the desire for small gains. Therefore, we must remain vigilant against these attack methods and be on guard at all times.
So, how do you identify phishing attacks? Let's start with their principles.
Principles of phishing attacks
Phishing attacks mainly occur in four ways: false airdrops, induced signatures, backdoor tools, and offering mnemonic phrases.
False airdrops:
Attackers use address generators to create addresses that are very similar to users' wallet addresses (usually with the same first or last few digits), and then transfer small amounts of funds (e.g., 0.001 USDT) into these addresses, or deploy fake USDT. This leads users to mistakenly believe that these addresses are their normal receiving addresses. When users make new transfers, they may inadvertently copy the transaction history and mistakenly transfer funds to the attacker's address, resulting in asset loss.
Induced signatures:
Attackers create counterfeit web pages, such as imitation websites of well-known projects, false airdrop links, or shopping platforms, to induce users to connect their wallets and execute signature operations, thereby stealing assets.
Common induced signature attacks include the following:
- Direct transfer
Attackers disguise signature operations as functions such as claiming airdrops or connecting wallets, when in reality, the operation transfers the user's assets to the attacker's address.
- Authorizing token transfers
Users sign transactions on phishing websites, such as ERC20's approve call or NFT's setApproveForAll. After obtaining authorization, attackers can freely transfer the user's assets.
- Blank address authorization phishing
Blank address authorization phishing is an upgraded version of authorization phishing. When users click on a phishing link to authorize (usually approve or increaseAllowance), the spender's address is an empty address with no on-chain records. If the victim signs the authorization, a contract will be deployed through the create2 method to transfer the victim's funds. Using blank address authorization can bypass some wallet security checks, avoiding detection by some wallet security tools.
- Zero-cost NFT phishing
Deceiving users to sign NFT sales orders. Once the user signs this order, the attacker can directly purchase the user's NFT through OpenSea. However, the purchase price is determined by the attacker, meaning the attacker can "buy" the user's NFT without spending any funds.
- eth_sign blank check (blind signature)
eth_sign, also known as blind signing, signs any hash value, equivalent to giving the attacker a blank check. Therefore, attackers can construct custom transactions to steal user assets.
- Permit phishing
Permit is an extension function of the erc20 protocol, allowing users to complete authorization operations through signed messages and send the signature results to another wallet, enabling asset transfers. By inducing users to sign ERC20 permit authorizations, attackers can gain permission to transfer the user's tokens.
- personal_sign signature
personal_sign is usually used to sign readable content, but it can also process the signed content into a hash value.
For example: 0x62dc3e93b0f40fd8ee6bf3b9b1f15264040c3b1782a24a345b7cb93c9dafb7d8 message, is the result of the target plaintext being hashed by keccak256. Phished users cannot understand the content of the signature. If they sign it, they will fall victim to a phishing attack.
Malicious multi-signature:
The original intention of multi-signature is to make wallets more secure, allowing multiple users to jointly manage and control the usage rights of the same wallet.
Taking TRON as an example, TRON's multi-signature is divided into Owner (highest authority, can manage permissions and perform all operations), Witness (participates in voting management), and Active (used for daily operations, such as transfers or contract calls). When a new account is created, the account address defaults to having Owner permissions.
When attackers obtain a user's private key through a phishing webpage/application, they can transfer or authorize the Owner/Active to their own address. Note that transferring removes the user's Owner permissions, while authorizing does not remove the user's permissions. However, in either case, the user loses the right to transfer wallet assets.
Since users can still deposit funds, attackers may "bide their time," not immediately transferring the victim's assets. They wait until the victim discovers the malicious multi-signature and stops depositing funds, at which point the attackers transfer the funds.
Backdoor tools:
- Disguised as scientific tools
"Scientific tools" usually refer to advanced tools used by some high-level users (the so-called "scientists") in the blockchain ecosystem, such as tools for quickly batch minting NFTs, batch sending tokens, or quickly executing certain complex on-chain operations. These tools are highly favored by primary market users because they greatly improve operational efficiency.
However, attackers may disguise themselves as developers of such tools, releasing seemingly legitimate tools that actually contain backdoor programs. These backdoor programs may secretly obtain private keys or mnemonic phrases when users use the tools, or directly control users' wallets to send tokens to the attacker's designated wallet. Subsequently, attackers can control the user's wallet using this sensitive information.
- Fake browser extensions
Many users like to use browser extensions (such as MetaMask, Token Pocket) to conveniently conduct blockchain transactions. Attackers may induce users to install counterfeit extensions through phishing websites. Once installed, these extensions secretly record users' transaction behavior, steal private keys, and perform multi-signature.
- Transaction accelerators or optimization tools
These tools often claim to help users accelerate transaction confirmations or optimize on-chain operations. Users typically need to input private keys or signatures to use these functions. Attackers secretly record critical information by inducing users to input it during usage.
Offering private keys/mnemonic phrases:
Attackers create counterfeit transaction websites or Telegram mini-programs (such as fake Pepebot), requiring users to provide private keys or mnemonic phrases to bind wallets, deceiving users into conducting "earth dog" transactions or other operations. In reality, attackers use these means to steal users' private keys and then transfer all assets from the wallets.
Analysis of typical cases
False airdrop scam:
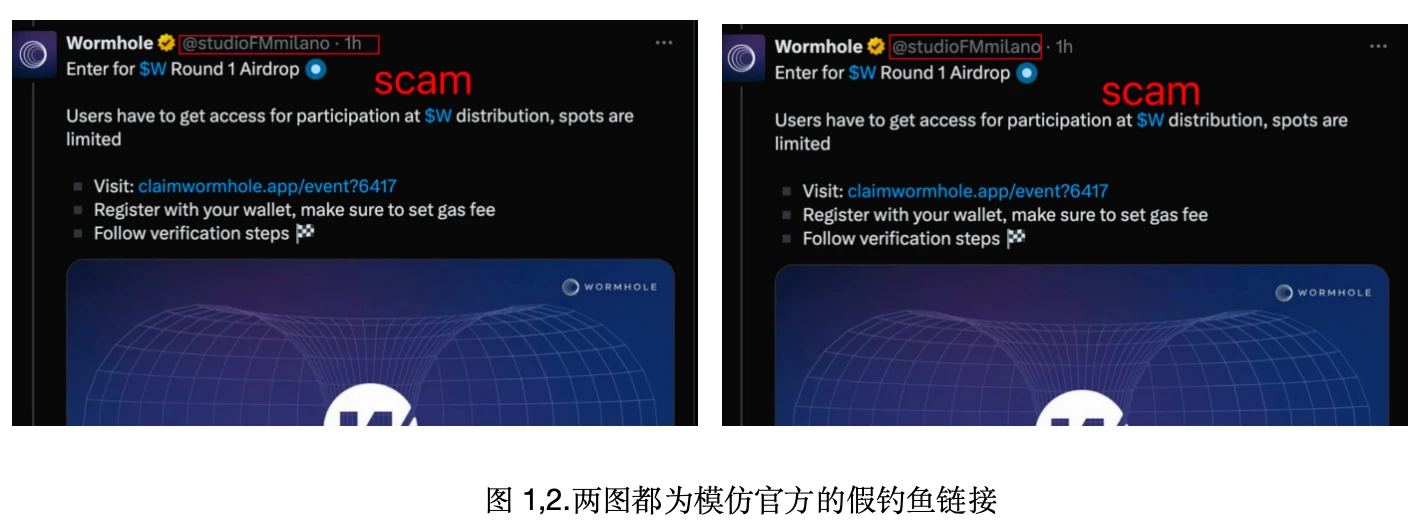
When the project Wormhole announced an airdrop, many Twitter accounts imitated the official account and posted fake airdrop links. In Figure 1, the project's name is @studioFMmilano·1h, and in Figure 2, the counterfeit project is @studioFMmilano, while the real project is @wormhole.
Induced Wallet Signatures:
Counterfeit Website Signatures:
Taking the phishing website moonbirds-exclusive.com as an example, this website is a counterfeit of www.proof.xyz/moonbirds. When users connect their wallets and click "Claim," a signature request box pops up. At this point, Metamask will display a red warning, but because the pop-up does not clearly show the signature content, it is difficult for users to determine if this is a trap. Once the user signs, the scammer can use the user's private key to sign any transaction, including asset transfers.
Permit Signature:
During the staking period, a user made a Permit signature on a phishing website. The user checked immediately and did not find any abnormal authorization. However, the phishing site later posted this permit offline authorization signature on the chain, opening a risk exposure for the target assets at the target address. The target user was unaware of this until they attempted to re-stake their ETH assets. The phishing site immediately transferred the assets, causing the user to lose $2.12 million.
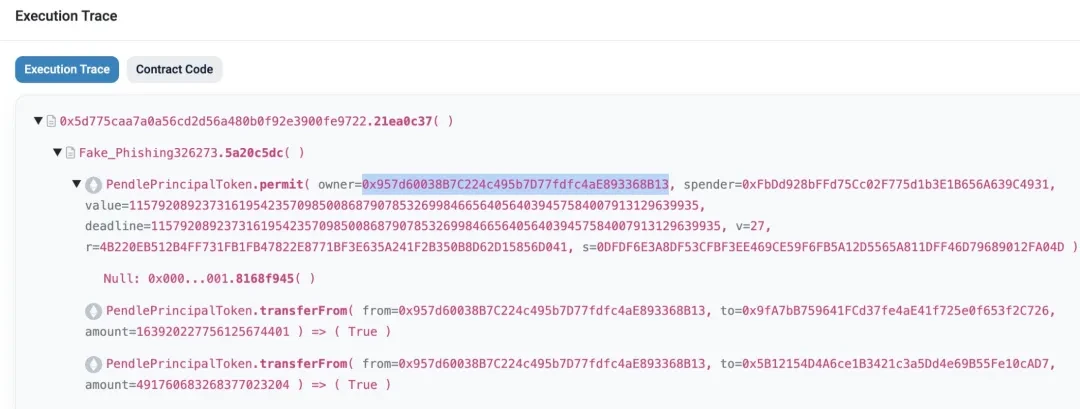
Figure 3. Account with permit offline authorization signature
Malicious Multi-Signature:
There are many phishing methods for malicious multi-signatures, the most common being "intentional leakage of private keys" or "fake plugins/wallets."
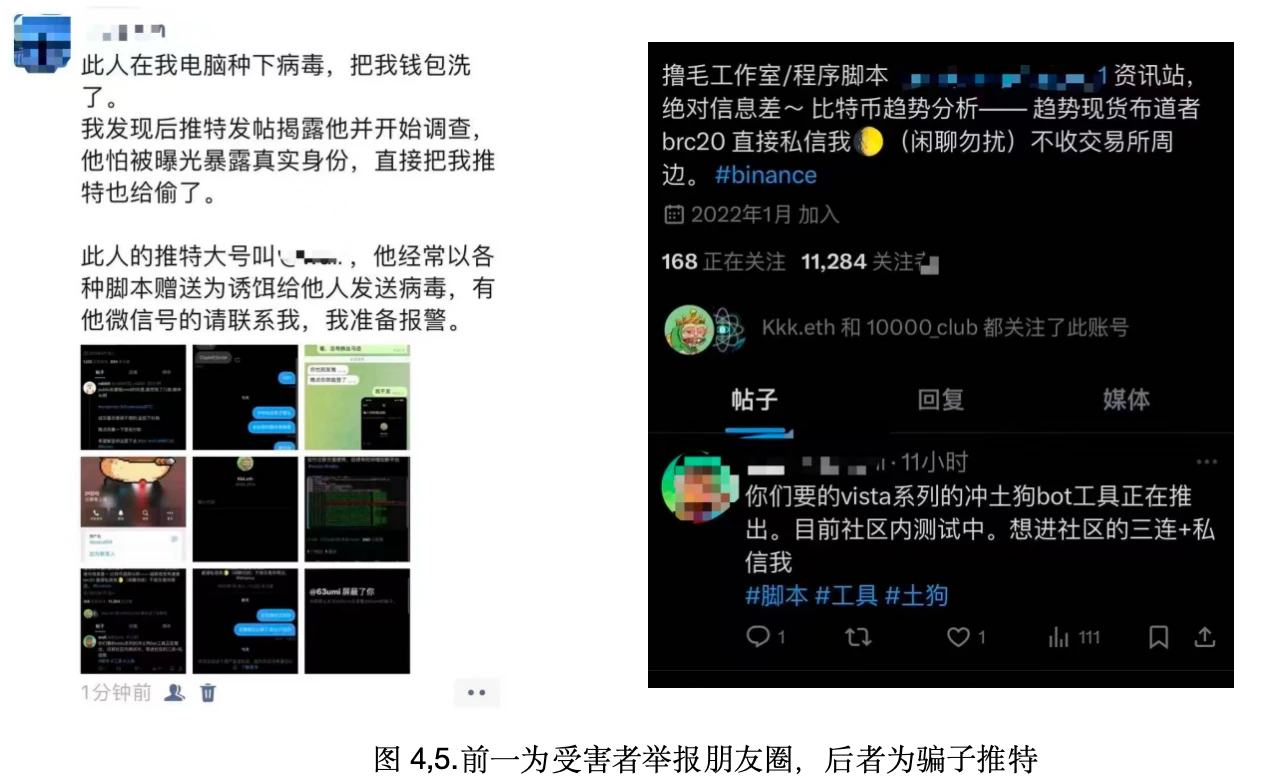
Intentional Leakage of Private Keys:
Attackers intentionally leak private keys on social media or through other means, using various tactics to persuade victims to transfer encrypted assets into wallets. Once the victim realizes that the assets cannot be withdrawn, the attacker then transfers the wallet assets.
Fake TokenPocket Wallet:
A victim searched for "TP wallet" on a search engine and downloaded the "TP wallet" from a non-official website. However, the downloaded wallet was not the official one but a fake wallet distributed by the attacker on the internet. After binding the mnemonic phrase, the victim's wallet was automatically multi-signed, making it impossible to transfer the assets.
Backdoor Tools:
A victim discovered a blogger on Twitter who claimed to specialize in WEB-3 "script development" and various scripts. The victim downloaded and ran the script given for free by the blogger, only to find that the wallet had been emptied, resulting in a loss of $700 USDT in tokens.
How to Prevent Blockchain Phishing Attacks
- Verify Links and URLs
When visiting any website related to cryptocurrency, it is essential to verify the authenticity of the links and URLs. Phishing attackers often create counterfeit websites that are extremely similar to official websites, with only a few characters modified. Therefore, the first step in prevention is:
Avoid clicking on unfamiliar links: Exercise caution with any unfamiliar emails, social media messages, or links of unknown origin, especially those claiming to be from "official" channels promoting airdrop activities or account issue alerts.
Use bookmarks to save official websites: When accessing cryptocurrency exchanges or wallet services, it is recommended to use bookmarks saved in the browser rather than searching through a search engine to avoid entering phishing websites.
- Two-Factor Authentication (2FA)
Two-factor authentication (2FA) is an important measure to enhance account security. In addition to a password, an additional verification step, usually through a dynamic code generated by a mobile SMS or authentication app, is required for account login.
Enable 2FA: It is crucial to enable 2FA for all cryptocurrency accounts that support it, including exchange accounts and wallet applications. Even if attackers obtain your password, they cannot access the account without the 2FA code.
Use an authentication app: It is advisable to use authentication apps such as Google Authenticator or Authy rather than SMS verification, as SMS may be vulnerable to SIM card hijacking attacks.
Regularly update 2FA devices: Ensure that the mobile phone or authentication device you have linked is up to date. If the phone is lost or replaced, update the 2FA device promptly to avoid security risks.
- Cultivate Security Awareness
Phishing attack methods in the blockchain world are constantly evolving, so continuous learning and maintaining security awareness are essential.
Follow security communities and news: Regularly follow relevant news, blogs, and community forums on blockchain and cryptocurrency security to stay informed of the latest security information and warnings, avoiding falling into new phishing traps.
Heighten vigilance: Develop the habit of carefully reviewing the content of any sensitive operations (such as authorization signatures or transaction transfers) before performing them, and avoid connecting wallets or signing operations on unfamiliar websites or platforms.
- Wallet Security Management
Wallets are the core storage tools for cryptocurrencies, and proper wallet security management plays a crucial role in preventing phishing attacks.
Do not disclose mnemonic phrases or private keys: Mnemonic phrases and private keys are crucial for controlling wallets. Once leaked, attackers can directly access the assets in the wallet. Therefore, mnemonic phrases and private keys must be securely stored and should not be disclosed to anyone, nor stored on connected devices.
Use cold wallets for storing large assets: Cold wallets, which are wallets not connected to the internet, usually refer to hardware wallets and offer higher security. For long-term holdings of large assets, it is recommended to store them in a cold wallet to prevent online attacks.
Use hot wallets reasonably: Hot wallets, which are connected to the internet, are convenient for daily transactions but have relatively lower security. It is advisable to keep a small amount of daily transaction funds in a hot wallet and store the majority of the funds in a cold wallet to spread the risk.
Regularly back up wallet data: Ensure that wallet mnemonic phrases, private keys, or recovery passwords are reliably backed up. It is recommended to store backup information in a secure, offline location, such as an encrypted USB device or physical paper.
Conclusion
In the world of blockchain, every action by users can directly affect the security of their assets. As technology advances, phishing attack methods continue to evolve, so it is crucial to remain highly vigilant, enhance self-protection awareness, and avoid falling into scams. Whether it is verifying links, using secure devices, enabling two-factor authentication, or managing wallets properly, these small measures can build a strong defense for our assets.
Exercise extreme caution and avoid being hasty!
Chain Source Technology is a company focused on blockchain security. Our core work includes blockchain security research, on-chain data analysis, and asset and contract vulnerability rescue. We have successfully recovered multiple cases of stolen digital assets for individuals and institutions. At the same time, we are committed to providing project security analysis reports, on-chain tracing, and technical consulting/support services for industry institutions.
Thank you for reading, and we will continue to focus on and share blockchain security content.
免责声明:本文章仅代表作者个人观点,不代表本平台的立场和观点。本文章仅供信息分享,不构成对任何人的任何投资建议。用户与作者之间的任何争议,与本平台无关。如网页中刊载的文章或图片涉及侵权,请提供相关的权利证明和身份证明发送邮件到support@aicoin.com,本平台相关工作人员将会进行核查。




