Original Title: "DeSec? Where Crypto Meets Security, Surveillance, and Defense"
Author: Luffistotle, Zee Prime Capital
Translator: Tia, Techub News
Recently, issues with security order in the West have begun to emerge. Typically, we measure the quality of order by taking walks in cities and parks during the day and at night (to see if it's safe). But now, this method of measurement is becoming increasingly unreliable. Social order is constructed and maintained through three components:
- Laws and social norms
- Law enforcement (police, surveillance, etc.)
- Judiciary (application of the law)

The interaction between these three is complex and deeply integrated. When people start to feel unsafe walking in parks, or when stores begin to relocate from the original city (usually a very clear sign), it indicates that governance is problematic. In fact, some current policies do have issues. We can try to understand the potential for crypto to improve law enforcement, which would contribute to the improvement of social structure. Below, we will discuss this, focusing on the application of crypto in surveillance tools.
Looking back at history, during periods of declining trust in public institutions and protocols (laws), societies often resort to vigilante justice to solve their problems. This power was originally meant to address actual community issues, but it eventually turned corrupt and evolved into extortion and blackmail.
Perhaps now there are more modern solutions, such as cheaper surveillance technology, through which law enforcement agencies may be provided with "leverage" to address issues at scale, ensuring the realization of community goals and desires. Technology can enable the same number of people to do more. Decentralized protocols can help ensure that this new power is not used for other purposes.
The idea of strengthening law enforcement through surveillance is actually terrifying, as there is a threat of abuse of power.
"Absolute power corrupts absolutely."
Cryptocurrency brings the possibility of financial freedom—it eliminates the state's monopoly on currency and provides a check on the state's financial behavior. Similarly, it can also provide a check on new surveillance tools. By combining ubiquitous, inexpensive robots, cameras, and sensors with a reliable neutral collaborative network, the monopoly of state surveillance can be checked.
In the category of projects we call DeSec, we conduct in-depth exploration through interesting conversations with outstanding individuals. The security field is another opportunity for crypto, as it is one of the few areas where clients (governments, communities) are willing to pay for insurance (defense is willing to pay for redundancy). Redundancy is an inherent feature of crypto. This feature is also why many cryptographic products often cannot compete with other solutions—crypto needs to constantly pay for higher levels of security/redundancy/validation.
That being said, redundancy is not a bad thing. It is a balance between fixed costs of certainty and variable future costs. In the case of Bitcoin, its value and success come from the cost paid for achieving trustless validation (breaking consensus requires a high cost, hence its high security). In the defense manufacturing industry, the tolerance for security or failure rates is also extremely low, even if it comes at a high cost.
DePIN Meets DeSec: NeighborhoodWatchDAO
Most of DePIN's value comes from shifting the burden of capital expenditure from companies/protocols to node operators in exchange for a certain proportion of income. This provides the potential for expansion for many types of networks that would not be achievable in other ways.
With these features, some immediate applications can be introduced to the market. For example, Dempsey is a DePIN-style SoundThinking (formerly known as ShotSpotter) node network, which can be sold to ShotSpotter itself and can also have its own protocol. For those unfamiliar, ShotSpotter is a microphone network installed on buildings that can triangulate the location of gunfire and alert law enforcement or emergency personnel for faster/immediate resource deployment.
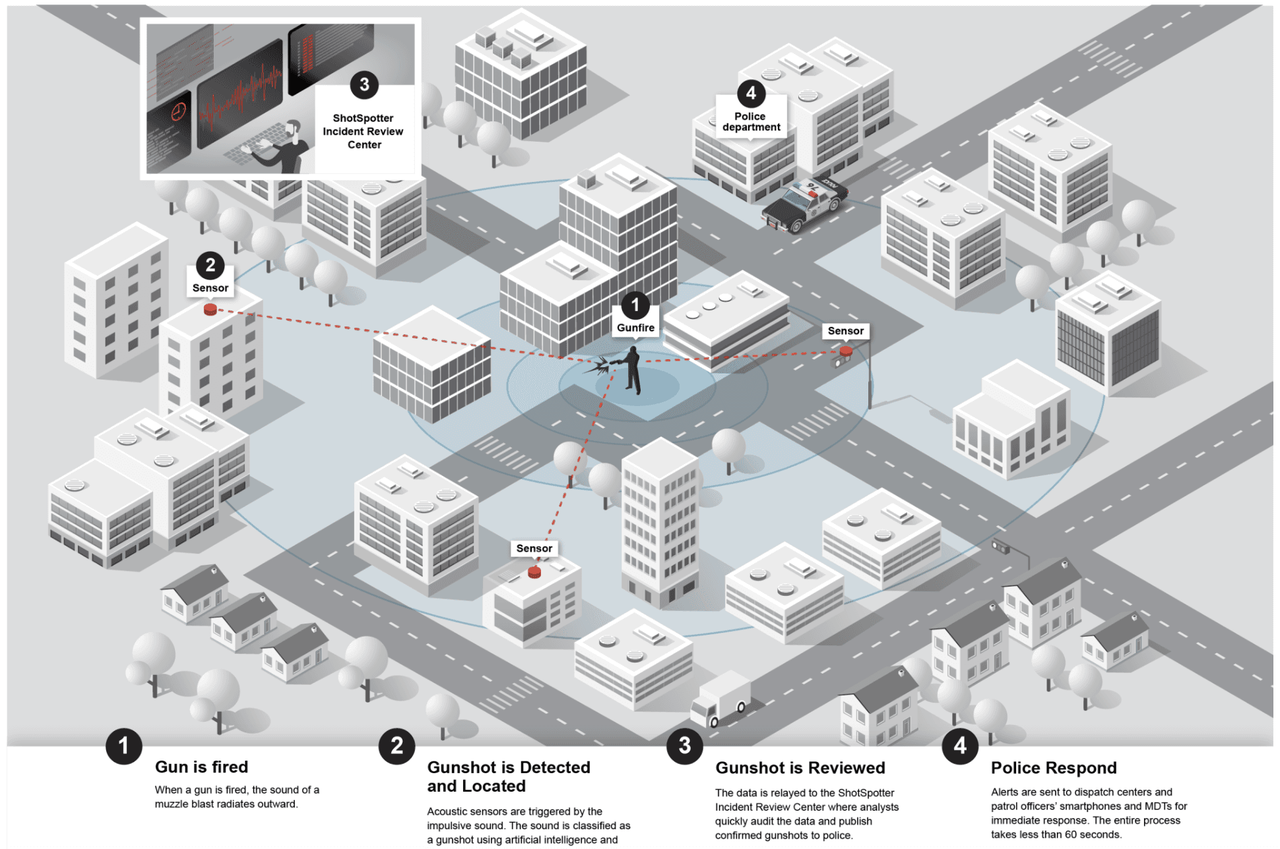
As node operators deploy to their respective cities, such protocols can expand globally at a much faster pace than the internal reinvestment cycle of companies like SoundThinking.
Similarly, the risk of small drones invading potentially important airspace is increasing. As recently demonstrated by the incursion at Langley Air Force Base. While the US military may have confidential solutions for such attacks, another solution may be needed for other less secure airspace. Incentives can be provided for small radar or visual observation networks in relevant airspace to help law enforcement understand the situation at the launch point.
Similar models can be used to observe signal strength. (Although this is usually provided by wireless providers primarily to ensure network quality, wireless providers also have drawbacks, as their signals are usually more transient.) DePIN can provide continuous signal quality monitoring for these networks (as some projects like ROAM have already planned to do). This is a simpler execution solution.
In recent years, the number of cheap signal jamming devices in the hands of thieves has increased dramatically. These devices are very frightening because you may find that when someone breaks into your home, your phone, wifi, or radio cannot contact the police.

The criminals can carry it on their belts and then rob your home or steal your car. Signal monitoring in cities and other areas can easily detect such interference events. Similar to ShotSpotter, it can also alert authorities.
We can also create similar protocols to incentivize small drones for regular monitoring (Patrol2earn) in problem areas, or we can use existing DePIN projects to support surveillance agencies. Projects like Frodobots or DIMO capture critical events with cameras.

Communication
Similar to the surveillance department, the DePIN network can also be used to enhance the robustness of network transmission (whether electrical or digital). The benefit is that such networks can remain stable even in the event of a disaster.
Mesh edge networks can resist today's highly centralized CDN-centric internet traffic, and decentralized power plants can coordinate small-scale energy production, providing backup power when these energy devices become targets in major production centers.
This logic also applies to modern warfare. In fact, modern frontline forces need decentralization. As we have seen in Ukraine, the use of FPV drones is a significant development in the field of warfare. Small, low-cost (even cardboard) drones can now achieve fast and precise strikes. Any key facilities on the battlefield (logistics hubs, transmission/command shelters, etc.) become targets. This causes these small facilities to become failure points, and the best way to address this is through distributed communication.

In this economic situation, do you still want to use missiles?
Verification
Multi-party verification can be applied to robot manufacturing. Inputting malicious instructions to manufacture robots could pose a serious risk to the entire manufacturing chain. One way to address this issue could be to achieve consensus on the code to be executed at runtime. By capturing malicious changes to the manufacturing process through consensus on the code to be executed.
Similar to verification, STAEX provides a public network to facilitate trustless communication between IoT devices. This provides a novel way of communication for these devices and reduces the risk of interference through traditional channels. Given the increasing risk of illicit activities, this is an important technology that can build strong networks to allow these devices to transmit valuable data.
Other uses of verification include the citizen evidence submission as described by Palmer Luckey (snitch2earn). Within the current legal framework, highly complex operations such as covert identities and bait cars may be difficult to execute, but even so, there are still plenty of ways to record criminal activities in today's age, setting up a simple place to deploy data, and even contextualizing location/time verification through encryption (ZK!!!).

DeSci
DeSci is another way of integrating encryption technology with the defense/intelligence industry. For example, the DeSci DAO funds research in previously overlooked areas such as materials science, biofabrication (like valleyDAO), cryogenics (CryoDAO), longevity (Vita), or human performance enhancement (anyone want to do a peptide DAO with me?). These DAOs can actually have a meaningful impact on these research areas. For example, HairDAO is now one of the largest non-baldness research funders in the world.
I believe that as more and more scientists are abandoning traditional research paths, more innovative frontier research will come from these types of DAOs.
Why Protocols Matter
Why do we need protocols? Many of the ideas proposed above are clearly aimed at enhancing state surveillance. However, assuming these surveillance tools are pushed to the market and managed by protocols. In this case, decentralized governance can check whether the authorities using them are enforcing the law properly, and whether the values of those monopolistic governors are consistent with the people they govern? If not, the protocol can vote to decide not to provide value-added information to law enforcement agencies anymore (perhaps they would choose to support private police forces or private intelligence agencies).
Comments from Skeptics

Increasing surveillance capabilities, regardless of who controls them, may have negative effects on society. Do not overly question the practicality of decentralized governance, as with Bitcoin, this protocol must rely on the principle of absolute permissionlessness, i.e., minimal governance. That is, maximizing trustlessness.
As society evolves, the ability to enforce absolute rule of law may weaken our adaptability. Disobedience can promote progress, although it is a very specific form of disobedience (not street crime). How can we eliminate specific types of crime? If surveillance technology is maximally utilized, this could become a slippery slope.
Therefore, when implementing technologies that help maintain established order, we must be careful to protect privacy. We humans must have the ability to voice outrageous ideas and resist tyranny. If the asymmetry between law enforcement and resistance becomes too great, we are only fostering minority report-style tyranny.
If we delve deeper into this asymmetry, we may find that the right to bear arms in the United States has become meaningless. When the right to bear arms was established, its goal was to ensure the potential for resistance, but once we invented missiles (not to mention nuclear weapons), this potential no longer exists. Of course, the right to defend one's property still exists, but it is ineffective in resisting the government.
Encryption technology has the unique ability to bring the market into a new realm. Will the future be MerceneryDAO, crypto-funded defense technology, community-owned drones, or liberal and pacifist? No one knows. Perhaps the answer lies in more niche areas, such as decentralized micro-nuclear power plant monitors and drone protection networks, or perhaps the answer lies in places we haven't even considered.
免责声明:本文章仅代表作者个人观点,不代表本平台的立场和观点。本文章仅供信息分享,不构成对任何人的任何投资建议。用户与作者之间的任何争议,与本平台无关。如网页中刊载的文章或图片涉及侵权,请提供相关的权利证明和身份证明发送邮件到support@aicoin.com,本平台相关工作人员将会进行核查。



