Today, the concept of blockchain has become deeply ingrained in people's minds, and digital wallets have become the main way for people to understand and participate in the blockchain ecosystem. However, driven by interests, some people take risks and embark on the criminal path of creating and distributing counterfeit wallets. Currently, counterfeit wallet websites and applications are widely present on the internet, becoming a "stumbling block" for beginners and posing significant potential risks to personal assets.
This article aims to expose the concept, harm, distribution, and dissemination methods of counterfeit wallets, enabling users to fully understand the dangers of using and spreading counterfeit wallets. It is hoped that this will enhance users' ability to identify counterfeit wallets and fake official websites, ensuring that users can safely and securely manage their assets.
What is a Counterfeit Wallet
A counterfeit wallet is created by fraudsters through decompiling the genuine wallet's apk or ipa, adding functionality to steal private keys and mnemonic data for creating or importing wallets, repackaging it, and distributing it on the internet to guide users to download it. Once a user downloads and uses a counterfeit wallet, the private keys and mnemonic data will automatically synchronize to the fraudsters' servers for monitoring. If a large amount of assets is detected, they will be immediately stolen or maliciously set up for multi-signature, ultimately resulting in asset theft.
The version number and hash value of the wallet can be viewed on the TokenPocket official website's download page. Any client that does not match the official version data is a counterfeit wallet. The authenticity of the wallet can be verified through the installation package hash value verification tutorial.
Verification method for genuine TokenPocket:
1️⃣ Official website verification: https://verify.tpwallet.io/
2️⃣ Text tutorial: https://help.tokenpocket.pro/cn/secirity-knowledge/protective-measures/verification
3️⃣ Video tutorial: https://www.bilibili.com/video/BV18M4y1B7Hy
Note: Genuine TP Wallet should be recognized with the developer as TP Global Ltd.
Enormous Harm Caused by Counterfeit Wallets
Data from Third-party Channels:
The Trend+ research team has discovered counterfeit versions of all the most popular cryptocurrency wallet applications, including TokenPocket, imToken, MetaMask, Trust Wallet, and Bitpie. Researchers stated that a total of 249 counterfeit applications have been found, which have been downloaded by victims from around the world, including the United States, France, Germany, Australia, New Zealand, and Japan.
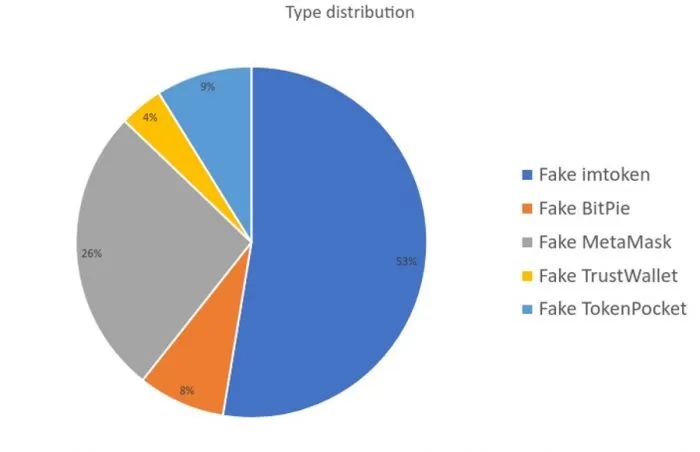
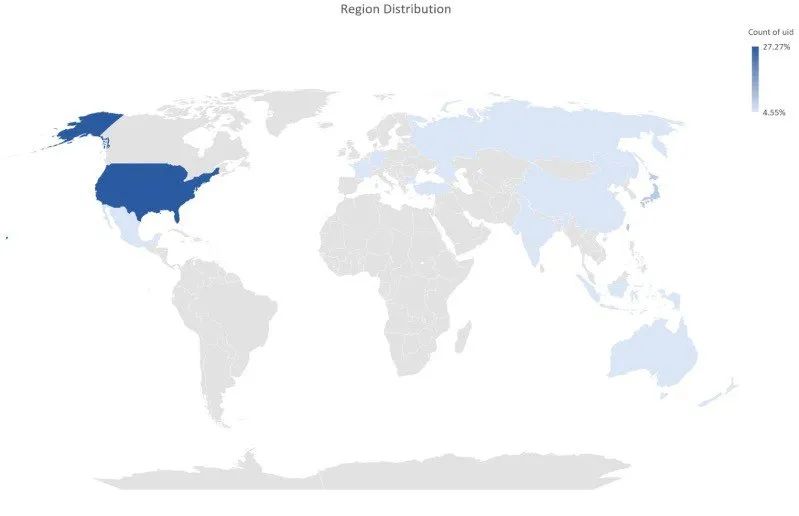
Source of data: Trend+ security team
According to research results from the SlowMist AML team, as of 2021, tens of thousands of victims have had their assets stolen due to downloading counterfeit wallet apps, with the stolen amount reaching up to 1.3 billion US dollars. Currently, this stolen data still shows an explosive growth trend.
Based on the information collected by the SlowMist MistTrack from victims, the proportion of victims whose assets were stolen due to downloading counterfeit wallet apps accounts for 61% of the reasons for being stolen, while private key leaks account for 28%. Other reasons include authorization theft, fraud, and contract vulnerabilities.
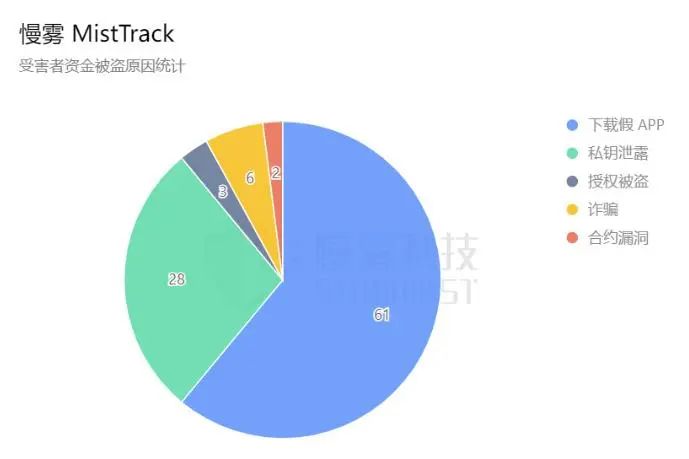
Source of data: SlowMist security team
The Bitrace team has long been paying attention to the trend of coin theft crimes and has conducted specialized analysis, tracking, and reporting on such counterfeit wallet multi-signature scams.
The main symptoms of Tron wallet malicious multi-signature caused by counterfeit wallets include: inability to use one's own cryptocurrency wallet app normally, specifically manifested as transfer errors, inability to call other on-chain contracts, but normal transfer in, and ultimately the assets in the account are transferred all at once. Upon investigation, it was found that all cases were due to downloading counterfeit wallet apps leading to key leaks, and then the stolen coins were illegally transferred by changing account permissions.
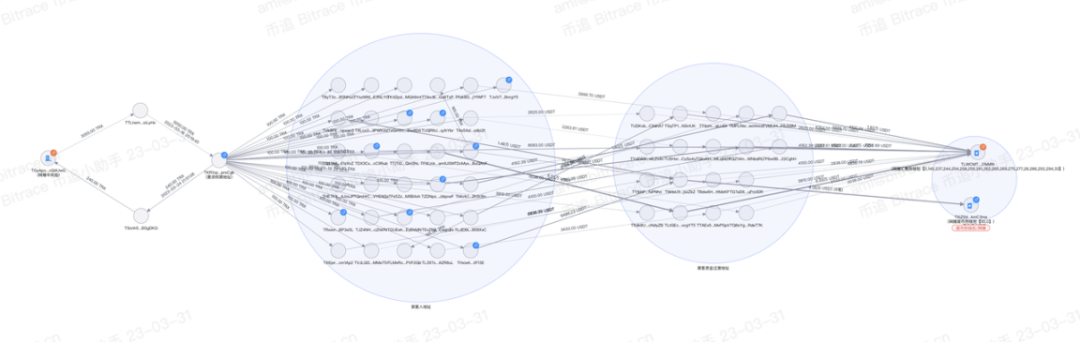
Source of data: Bitrace security team
By combining the data from Bitrace, SlowMist, and Trend+ security teams, we can fully see the depth of harm caused by counterfeit wallets and the magnitude of assets defrauded. These fraudulent activities are spread through various means and have formed a huge industry chain behind them. Counterfeit wallets pose a widespread threat to user groups, causing serious economic damage to users.
Channels for Creating and Distributing Counterfeit Wallets
1. Search Engine Channels:
In our daily lives, search tools have become an extremely common channel for obtaining information. Because of its ubiquity, scammers cleverly use people's usage habits and search product ranking optimization to achieve their fraudulent dissemination purposes. Data shows that scammers manipulate search engine results to optimize the exposure of counterfeit information, placing fraudulent content such as wallet source code at the top of user search results, increasing the likelihood of being viewed or disseminated.
For example, searching for "TP wallet source code" on Google and Baidu yields the following results:
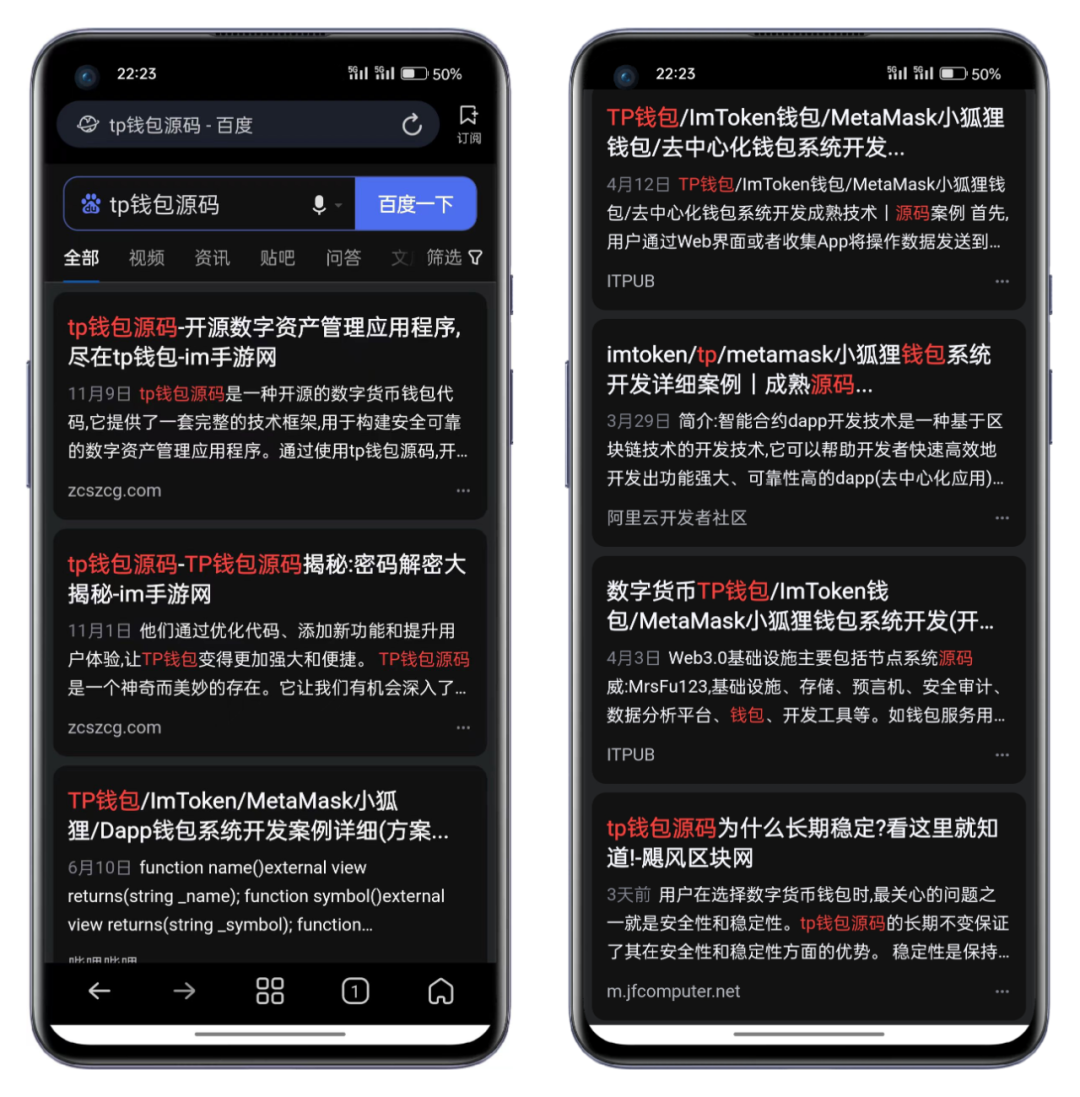
Baidu search results↑↑↑
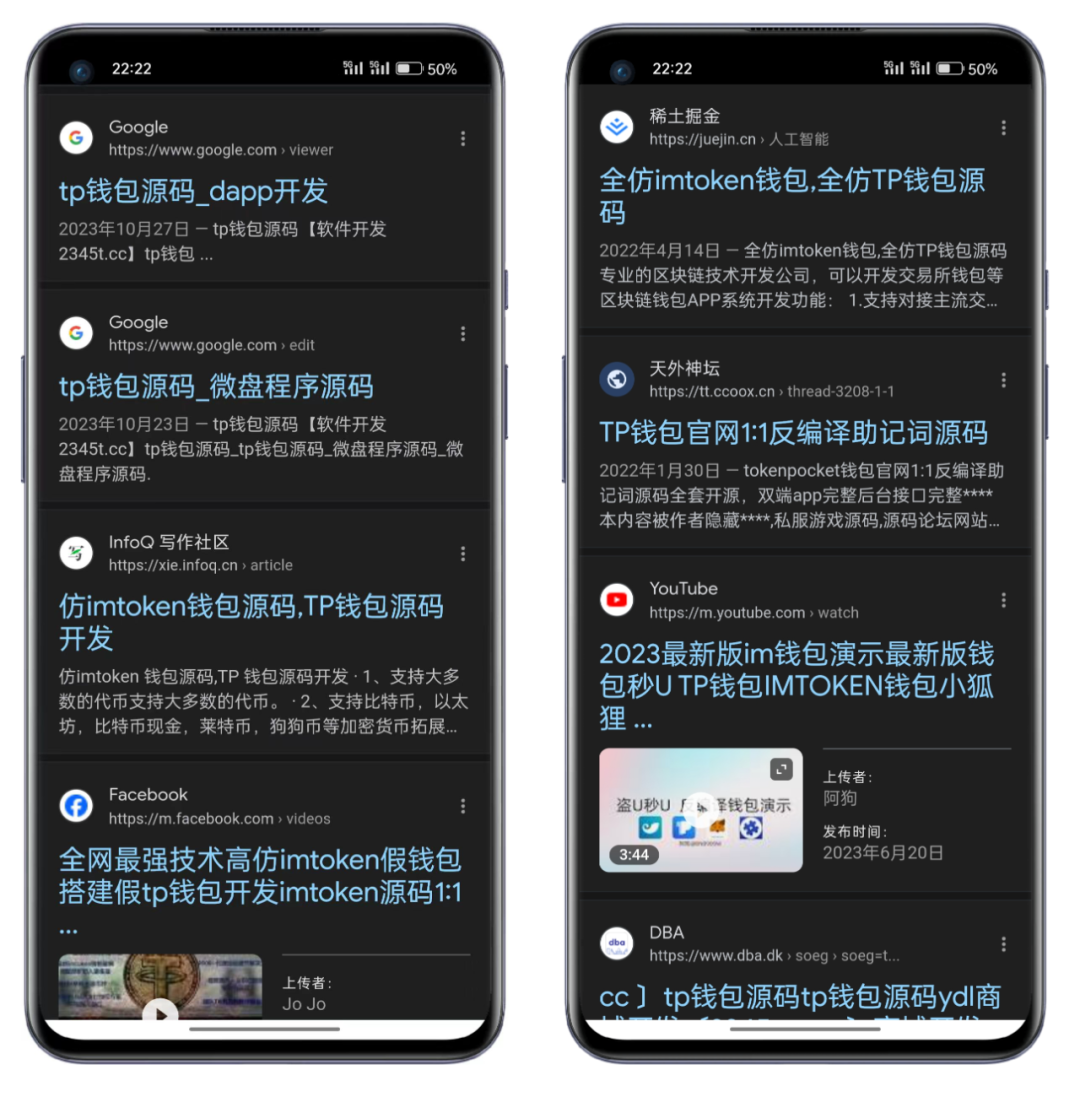
Google search results↑↑↑
2. Video Distribution Channels
The dissemination of counterfeit wallets through video platforms is increasingly becoming a major channel, with a clear upward trend in recent times, becoming another "highlight" for scammers after disseminating counterfeit official websites. The dissemination effect of videos is highly persuasive for new users and poses greater harm. The following are some examples of content displayed in search results.
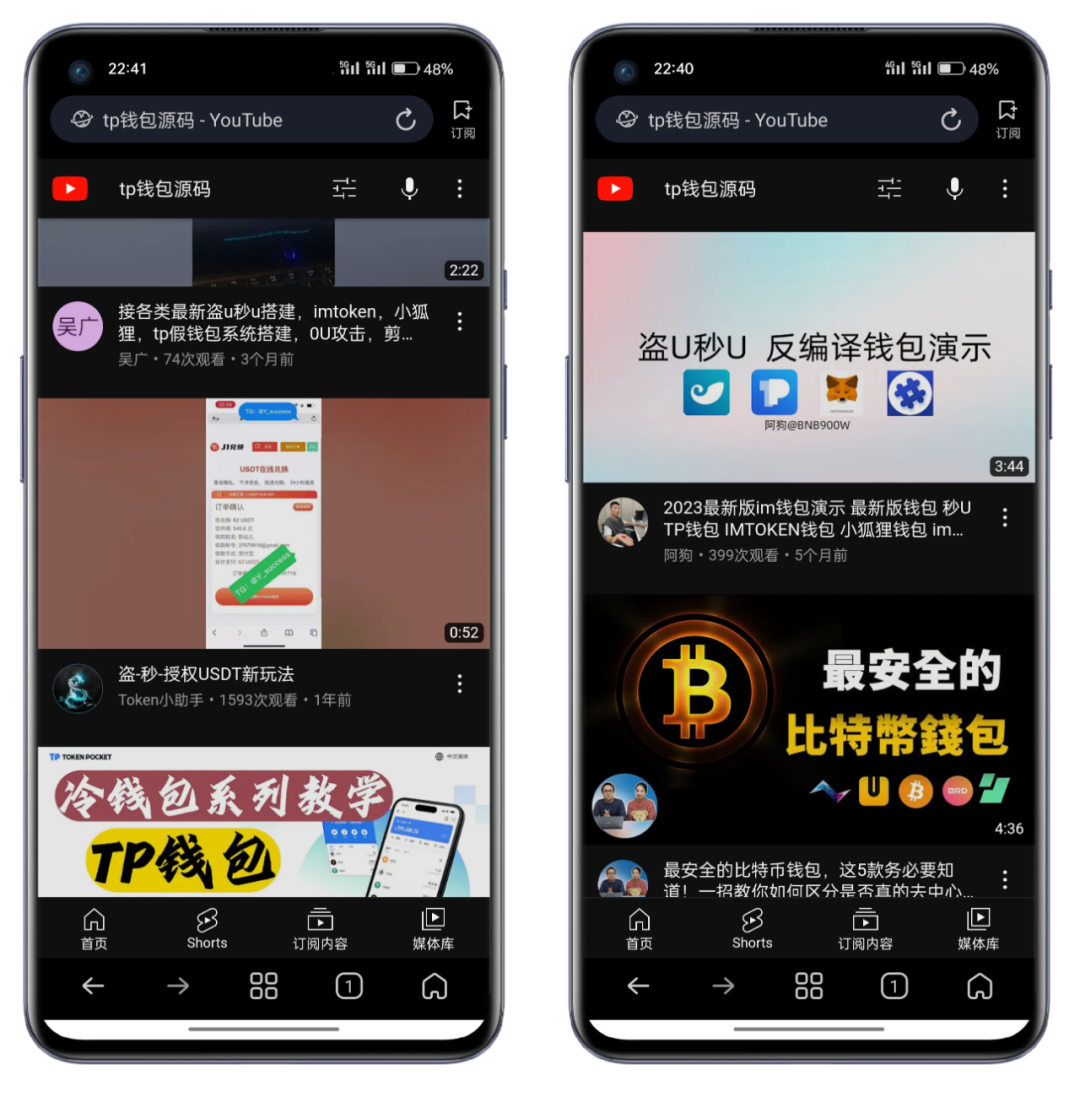
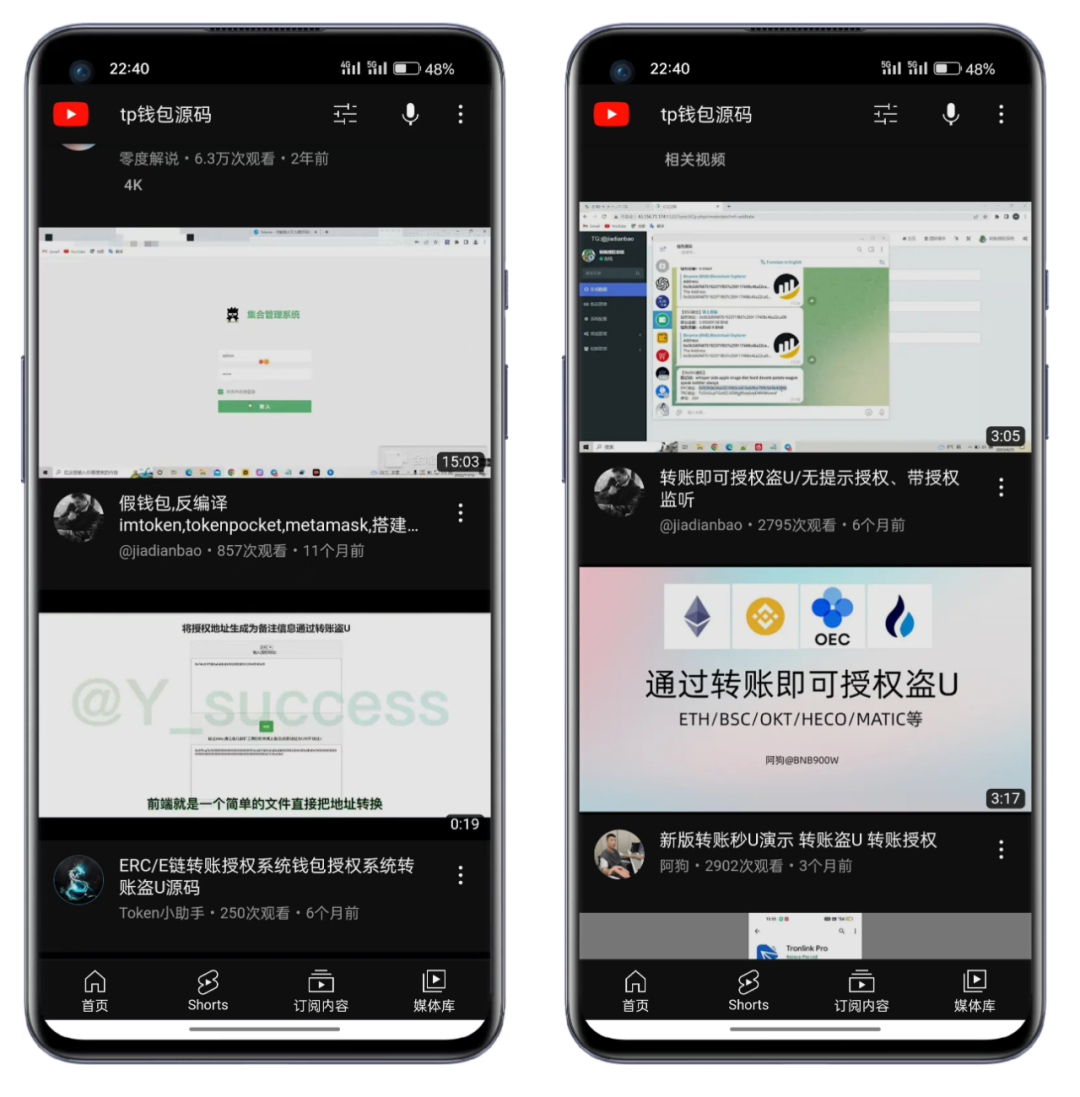
3. Social Media Channels
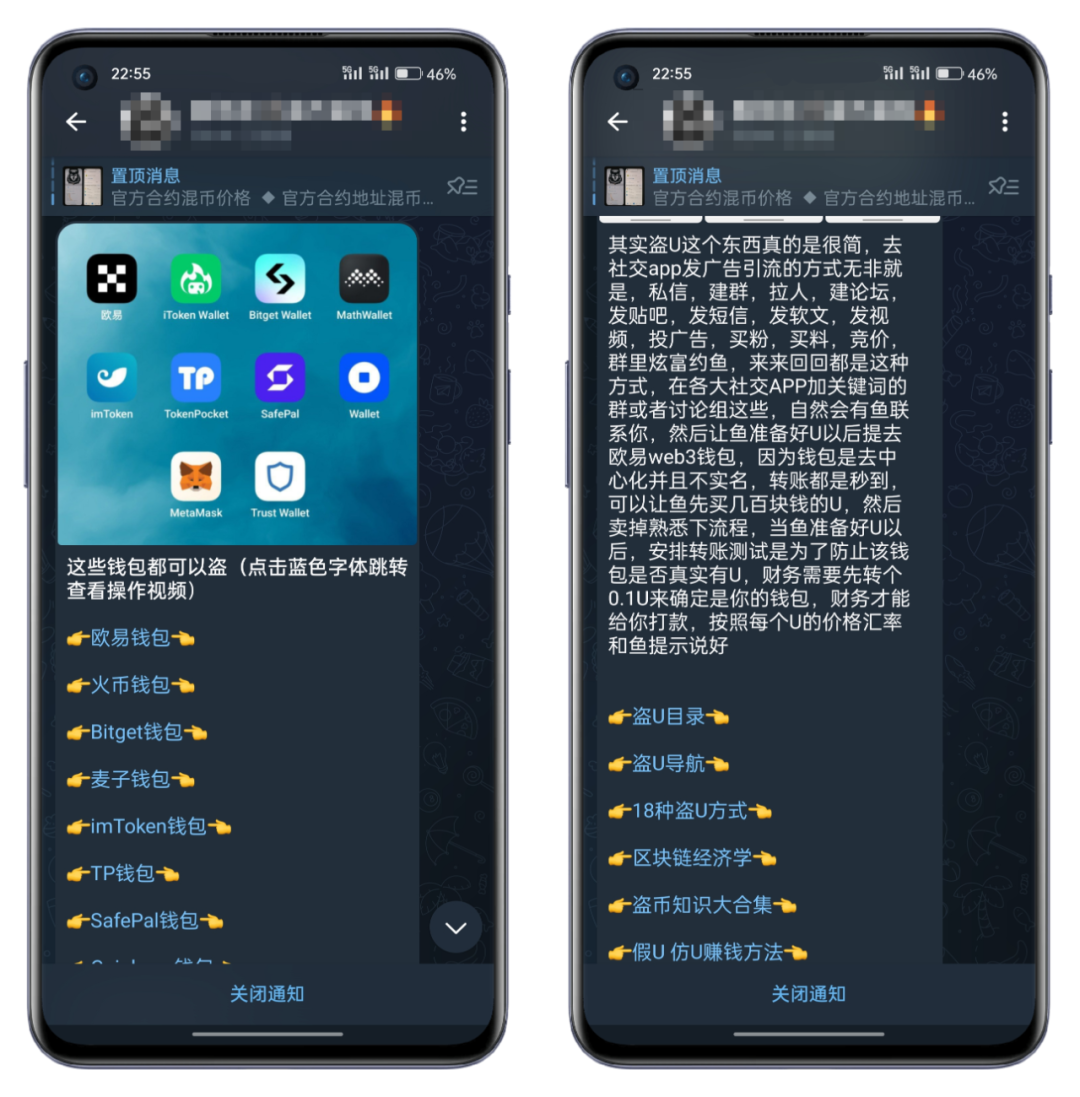
Counterfeit wallet source code is also disseminated through social media platforms, especially in QQ communities, WeChat communities, and Telegram communities. Fraudsters take advantage of the extensive user base on social media platforms to spread tutorials and promotions for counterfeit wallet source code in groups, and even entice users to participate in the distribution and dissemination of counterfeit wallets or counterfeit wallet source code, based on the proportion of dissemination performance or stolen assets for profit distribution.
The following are some examples of content spread in technical communities for malicious source code or stolen assets.
By spreading counterfeit wallet source code and creating counterfeit wallets through the above channels, these actions constitute the root cause of the dissemination of counterfeit wallets. Through these channels, we understand that the current situation is not optimistic. Scammers fully exploit the mainstream pathways of internet dissemination, forming a complete industry chain. This poses a huge threat to the entire blockchain environment, as almost all mainstream wallets can be found with information about counterfeit wallets on the internet.
Channels for Disseminating Counterfeit Wallets
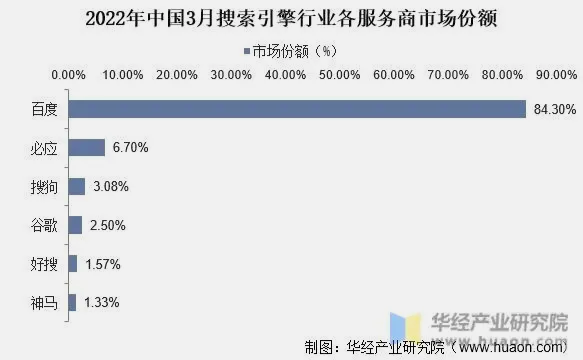
Baidu is the most widely used search engine in daily life, with a historical market share of 84.3%. It is followed by Bing and Sogou. The market share data for search engines is as follows:
The search results for TP wallet on the top four search engines are as follows:
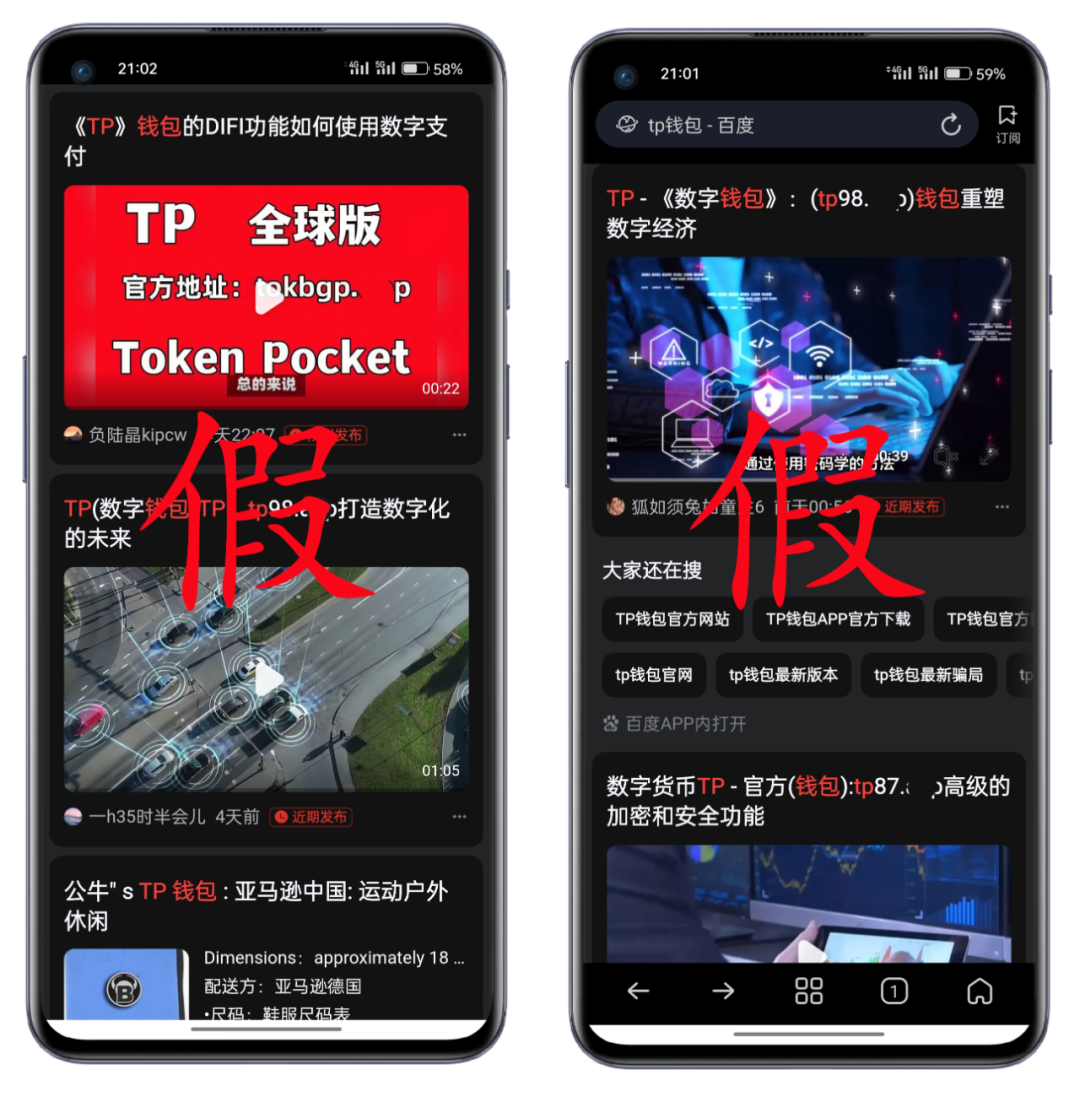
Baidu search results↑↑↑
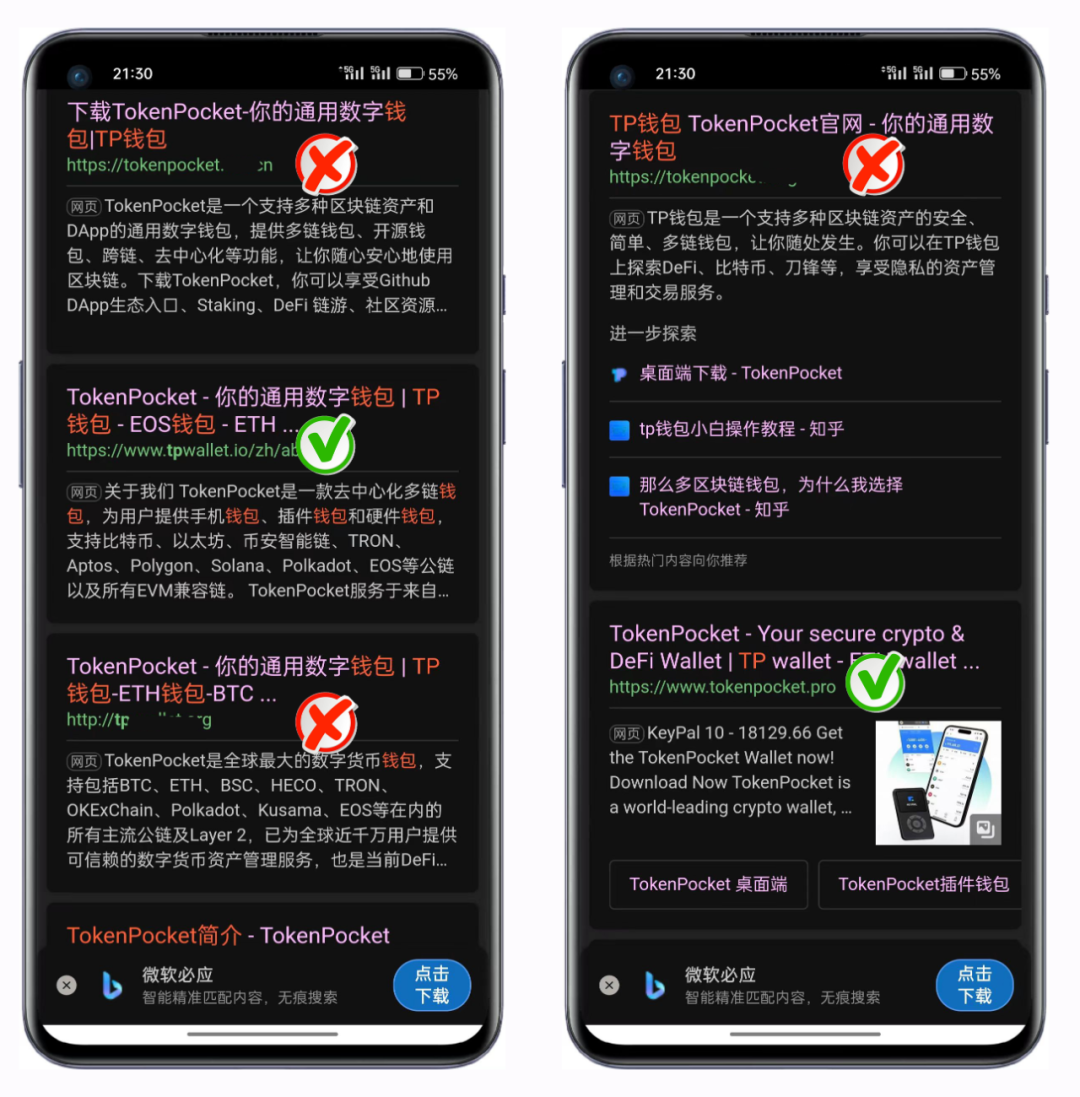
Bing search results↑↑↑
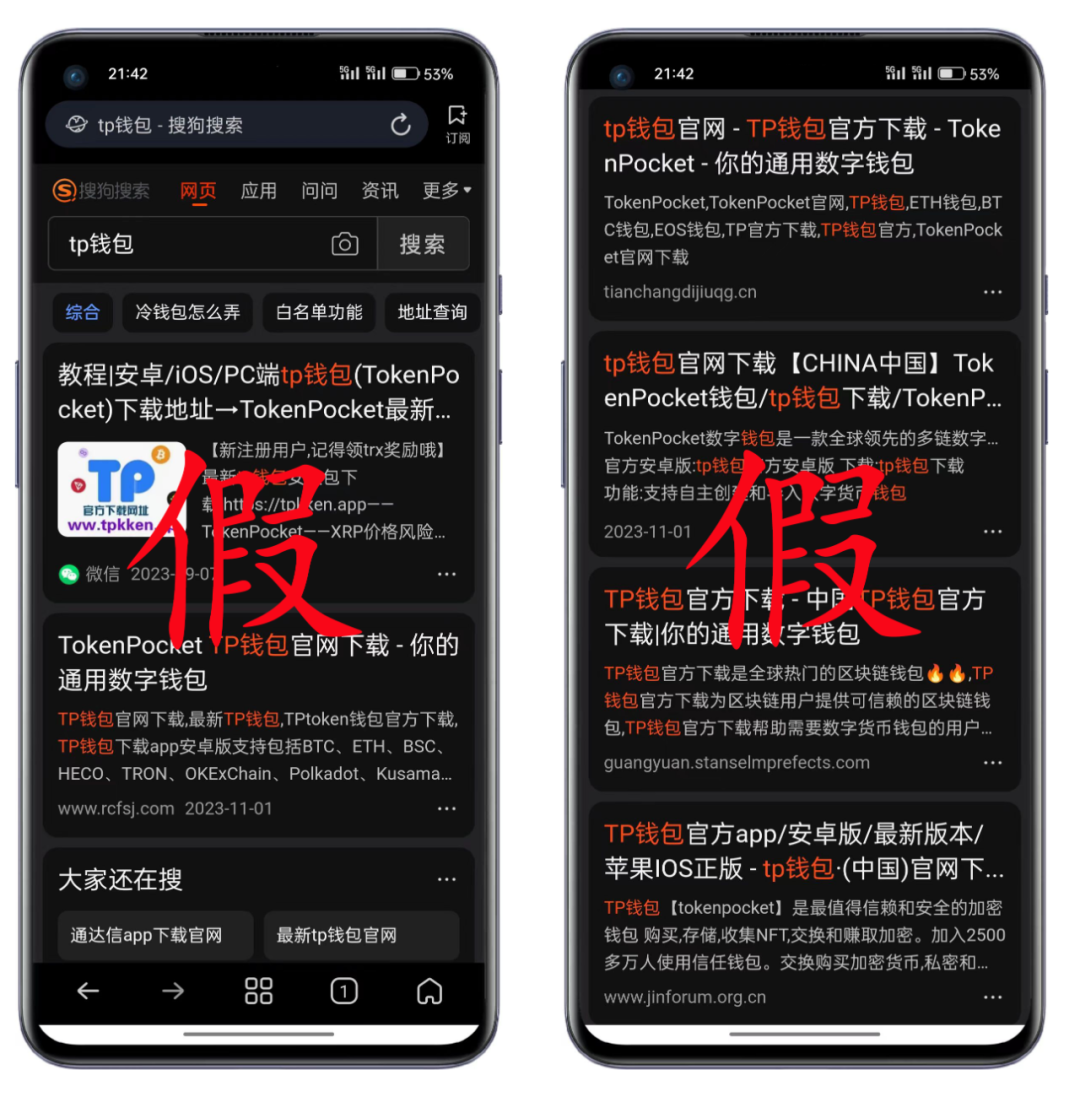
Sogou search results↑↑↑
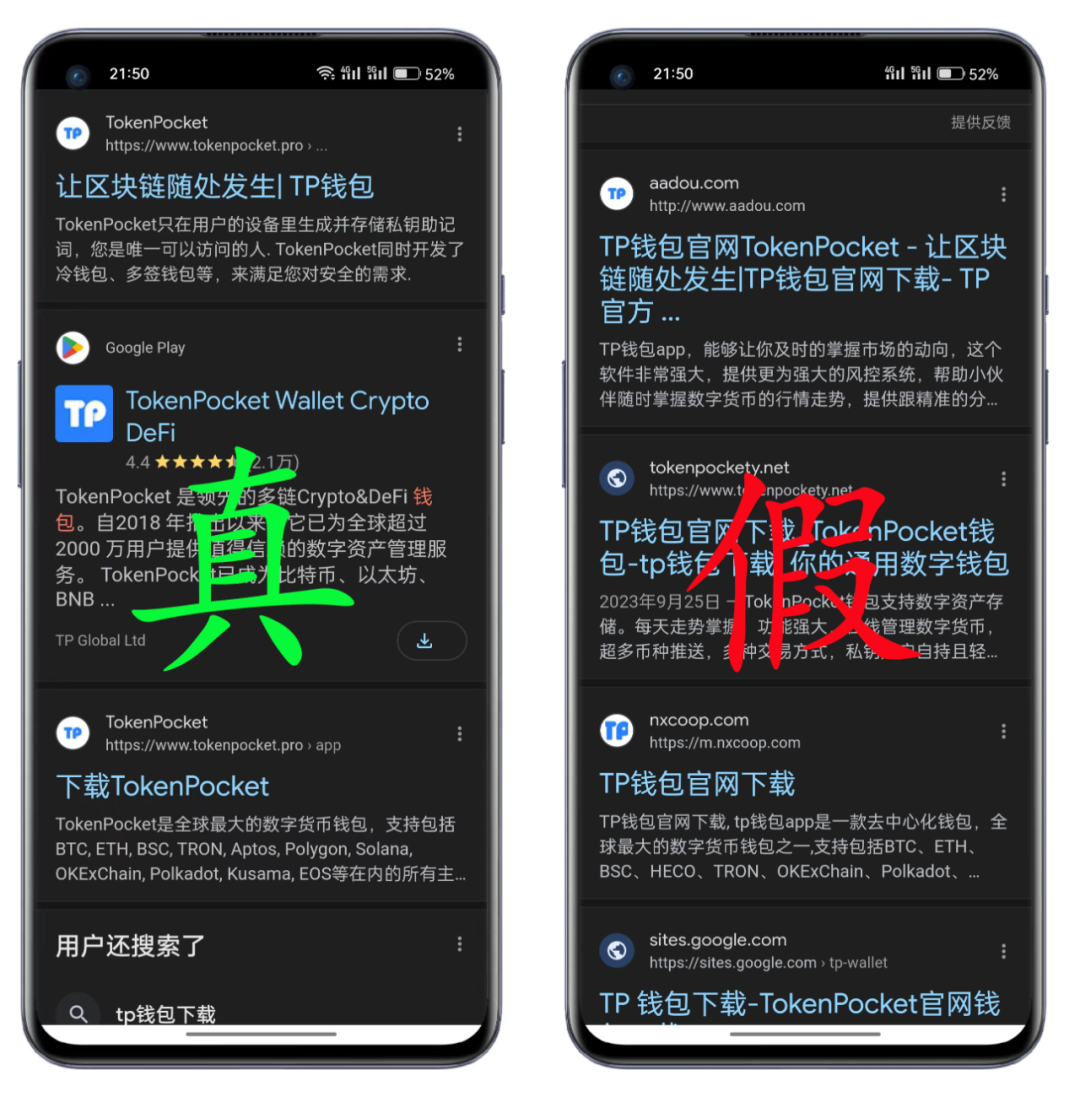
Google search results↑↑↑
According to the above search data, fraudulent activities disguised as counterfeit wallets have spread widely to mainstream search platforms. These fraudulent activities typically use fake official website links, create fake videos, or use other guiding methods to spread counterfeit wallets.
We strongly recommend that users increase their security awareness and ensure they visit the TP wallet official website: tokenpocket.pro, tpwallet.io, or other officially recommended channels (such as Google Play). Using genuine wallets is the most basic guarantee for asset security.
How to Prevent Counterfeit Wallets
Downloading and verifying wallets are basic knowledge that we should all have in the blockchain field. At the same time, developing good usage habits is crucial, especially for decentralized self-custody products, where it is essential to choose official channels. Here are some suggestions to help reduce the risk of encountering fraudulent activities.
Be cautious in selecting search results: When choosing search results, avoid relying on recommended results in search engines, as scammers may promote counterfeit wallets through fake official website links, fake videos, or other deceptive means. Using official website links is the safest choice.
Verify official website addresses: Only use official website addresses to access wallets. For TokenPocket users, ensure that you only use tokenpocket.pro, tpwallet.io, or other officially recommended channels (such as Google Play).
Use enhanced security products: TokenPocket supports diversified security products, such as cold wallets, hardware wallets, multi-signature wallets, AA smart wallets, passphrase-hidden wallets, NFC backup cards, and privacy wallets. These features or products provide additional security safeguards and play a decisive role in promoting asset security.
Enhance learning: Continuously learn about the security and anti-fraud knowledge related to blockchain wallets, and remain vigilant about new fraudulent methods. By taking these preventive measures, users can minimize the potential risks of encountering counterfeit wallets in blockchain usage and ensure the security of digital assets.
Asset Security Recommendations
When using decentralized self-custody wallets, it is crucial not to be afraid of some cumbersome tasks, such as backing up private keys and mnemonic phrases must be done offline, and they should be stored properly to avoid loss or leakage (NFC backup cards are a good offline backup option). The most important aspect is security, as every inadvertent oversight, from small-scale phishing scams to counterfeit wallets, malicious authorizations, or malicious multi-signatures, can lead to asset risks.
Especially in the Android client, due to its higher openness, some malicious apps can easily obtain more permissions. Therefore, it is essential not to use unofficial blockchain-related products casually, and never use any online platform to store private keys and mnemonic phrases, ensuring that your assets are protected from potential threats. In the field of digital assets, remaining vigilant and cautious at all times is crucial.
免责声明:本文章仅代表作者个人观点,不代表本平台的立场和观点。本文章仅供信息分享,不构成对任何人的任何投资建议。用户与作者之间的任何争议,与本平台无关。如网页中刊载的文章或图片涉及侵权,请提供相关的权利证明和身份证明发送邮件到support@aicoin.com,本平台相关工作人员将会进行核查。



