2024 年对于 Web3 零售投资者来说真是残酷的一年。太多的投资者被诈骗者和黑客洗劫一空。虽然正如之前报道的那样,获取零售投资者损失资金的
撰文:NEFTURE SECURITY
编译:白话区块链
2024 年对于 Web3 零售投资者来说真是残酷的一年。太多的投资者被诈骗者和黑客洗劫一空。
虽然正如之前报道的那样,获取零售投资者损失资金的精确数据是一项极其困难的任务,但犯罪报告显示,至少有 58.4 亿美元从他们的钱包中被抹去。其中,至少 40 亿美元因「杀猪盘」骗局而损失,超过 10 亿美元因钓鱼诈骗 ( 包括钱包窃取和地址投毒 ) 而损失,4.44 亿美元则归因于退出骗局。
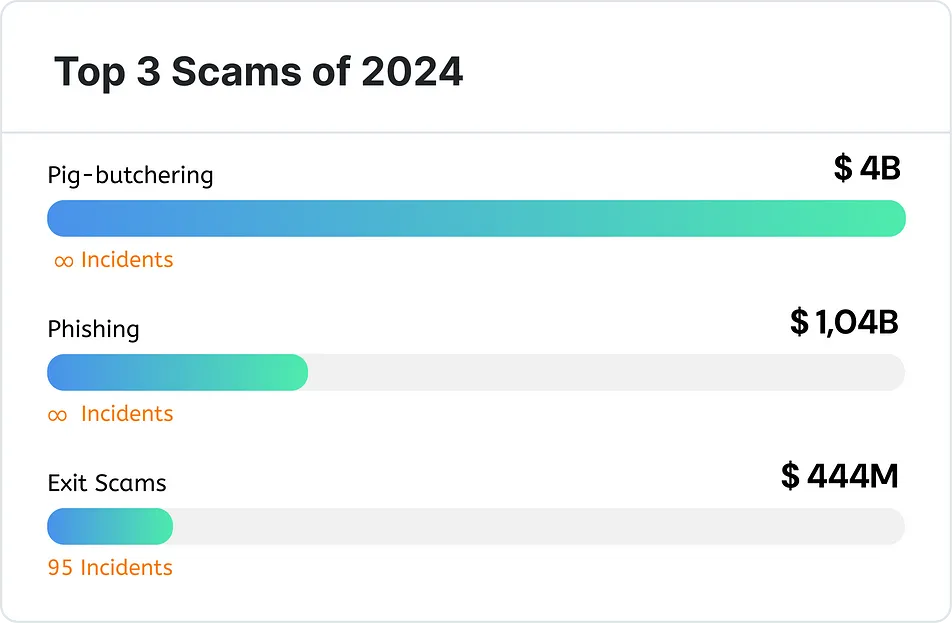
必须指出,2024 年的加密货币市场状况确实为这些诈骗者提供了巨大机会。
从 2023 年底开始的牛市,到 2024 年 3 月 14 日比特币达到新的历史高点 73,738 美元时达到顶峰,吸引了大量流动性,不仅来自经验丰富的加密货币爱好者,还包括一大群急切的零售新投资者。2024 年被认为是比特币突破 10 万美元大关的一年 ( 它确实做到了!),再加上迷因币超级周期的爆炸性活动,将 2023 年的加密货币市场「鬼城」变成了一个充满交易活力的繁荣中心!
来源:Dune
许多新手对加密货币的险恶水域一无所知,这使他们极其脆弱,成为诈骗者的理想目标。而经验丰富的交易者,在经历了漫长而痛苦的熊市后,同样甚至更容易受到 FOMO( 害怕错过 ) 的诱惑,这为诈骗者创造了完美的环境来掠夺零售投资者。
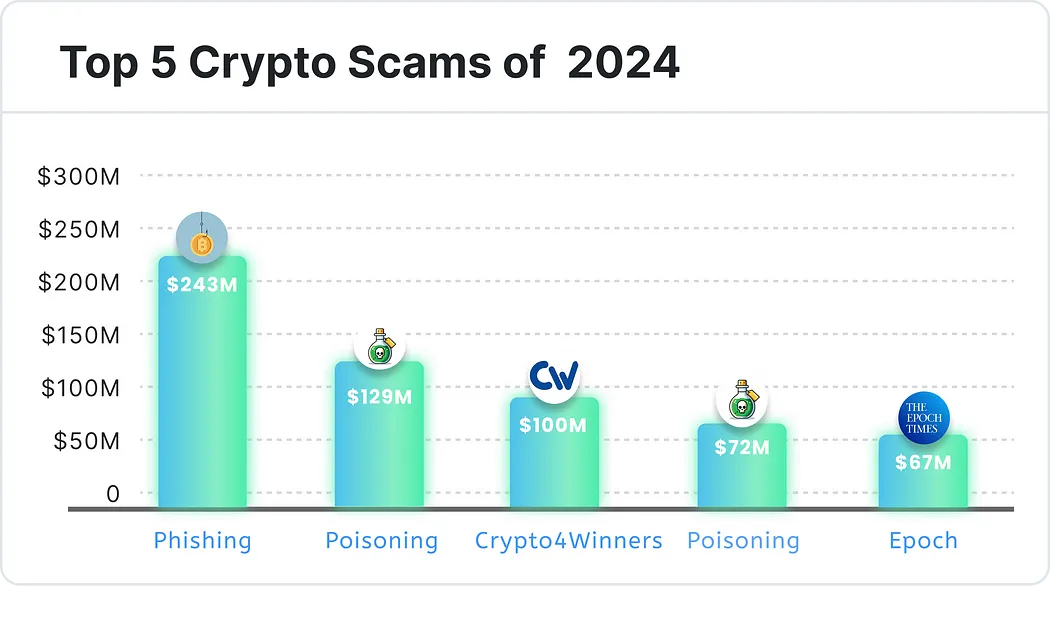
令人震惊的是,除去「杀猪盘」,2024 年排名前五的欺诈项目造成了惊人的 6.11 亿美元损失。
以下是 2024 年最成功的加密货币骗局!
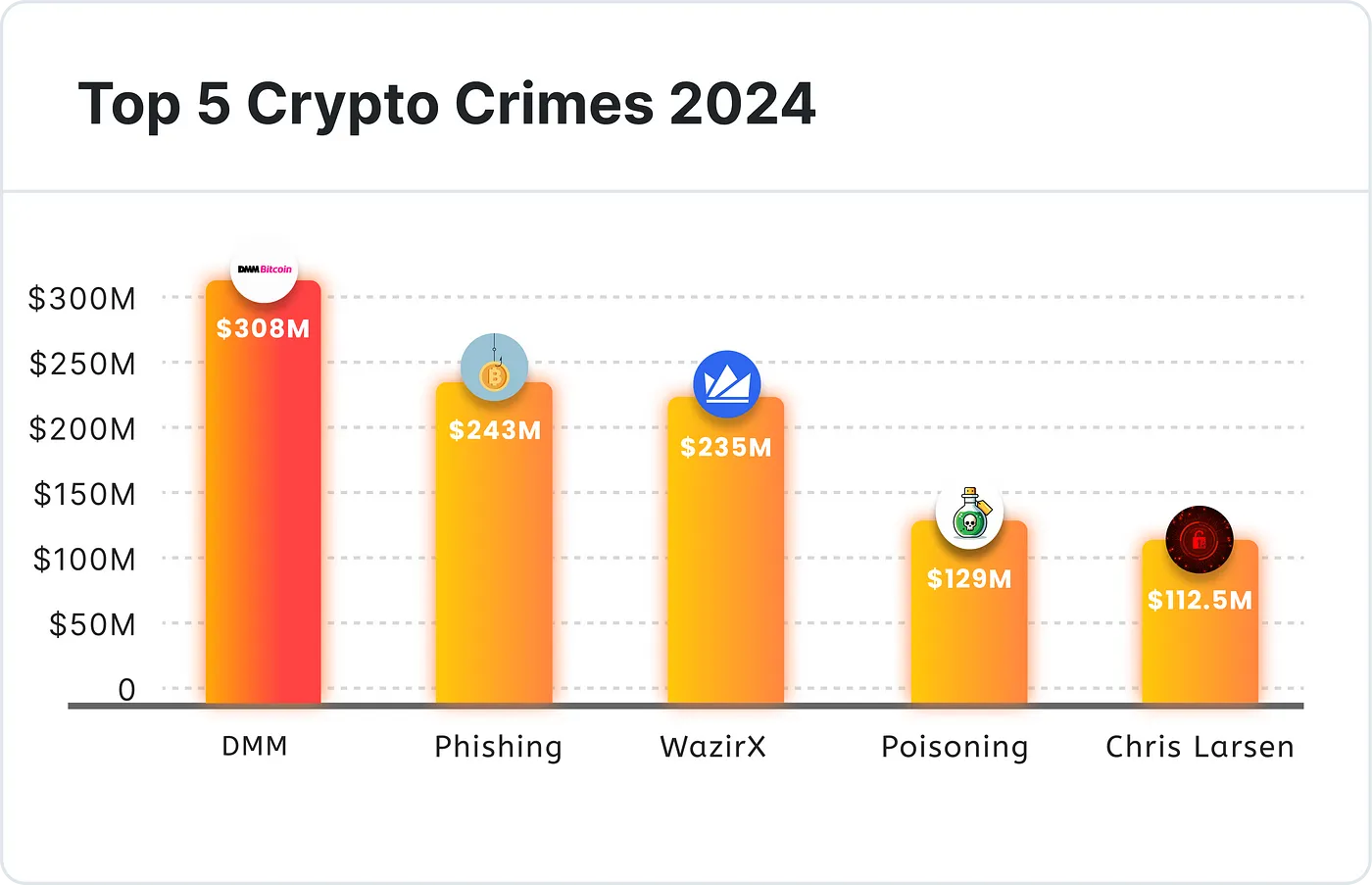
1. 2.43 亿美元被盗:迄今为止最大的社交工程钓鱼抢劫案——年度第二大抢劫案
2024 年最令人瞠目结舌的加密货币骗局是一次简单的社交工程钓鱼攻击,以其惊人金额位列年度第二大财务破坏性犯罪,仅次于朝鲜威胁集团对 DMM Bitcoin 私钥的 3.08 亿美元攻击。
目前,这似乎也是单个个体在单次加密钓鱼攻击中损失的最大金额。
2024 年 8 月 19 日,加密侦探 ZachXBT 在 Twitter 上披露,他发现了一笔可疑的 2.38 亿美元转账,资金通过多个中心化交易平台 (CEX) 进行洗钱和套现。很快,关于受害者身份的传言四起——是个人、对冲基金还是交易平台?这次抢劫是如何实施的:通过私钥漏洞、钓鱼还是两者兼有?
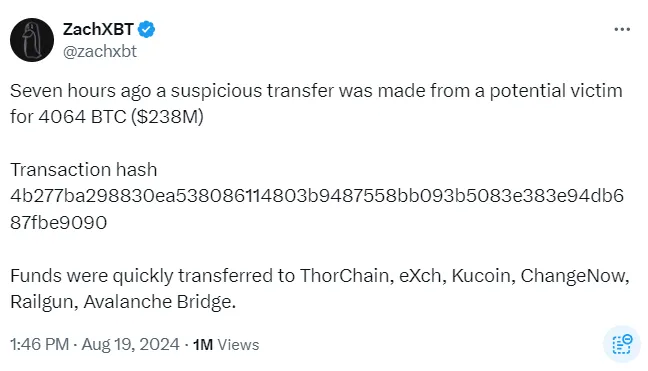
很长一段时间里,案件细节鲜为人知,除了 ZachXBT 的两次更新,报告了 Firn Protocol 和 NonKYC 成功冻结了约 50 万美元的被盗资金——这不过是杯水车薪。
一个月后,也就是在 2.38 亿美元攻击发生整整一个月后,ZachXBT 再次在 Twitter 上揭示了事件的完整故事。
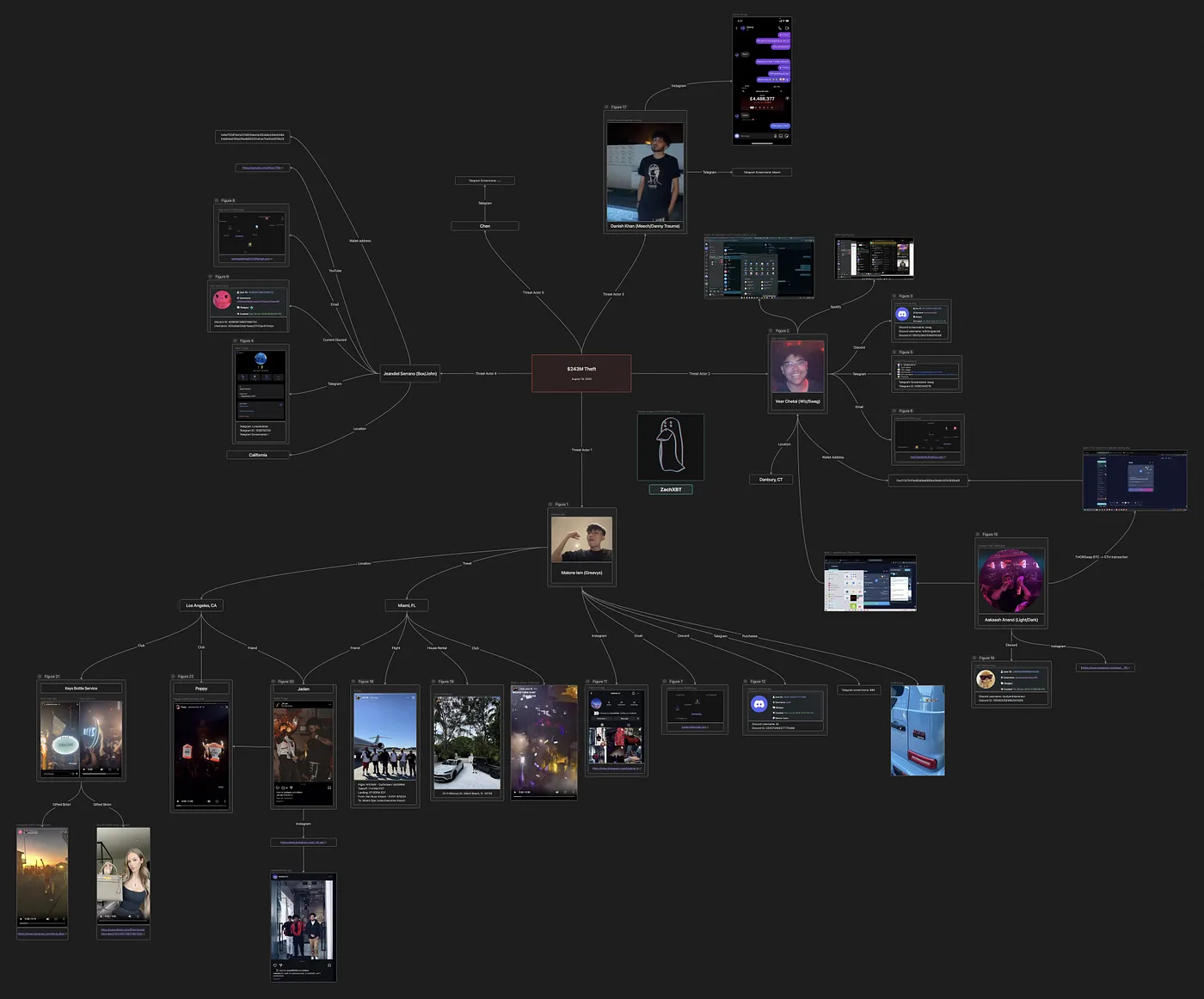
ZachXBT 的调查地图 —— 来源:ZachXBT
这次抢劫是一次「高度复杂的社交工程攻击」,即针对单一个人的钓鱼骗局。受害者是已破产的加密交易公司 Genesis 的债权人。
攻击当天,他接到一个伪装成 Google 支持的欺诈电话,骗子以此入侵了他的个人账户。根据 ZachXBT 的调查,随后受害者再次接到电话,这次骗子冒充 Gemini 支持,声称他的 Gemini 账户已被黑客入侵,并指示他重置双重身份验证 (2FA) 并从 Gemini 账户转移资金。
在多次劝说后,受害者使用 AnyDesk 共享了他的屏幕,使骗子得以访问并泄露他 Bitcoin Core 的私钥。
攻击者成功窃取了 2.43 亿美元,并立即试图将资金分散到多个钱包,然后转移到超过 15 个交易平台。根据 ZachXBT 的研究,盗窃的资产在比特币、莱特币、以太坊和门罗币之间迅速转换,以掩盖踪迹。
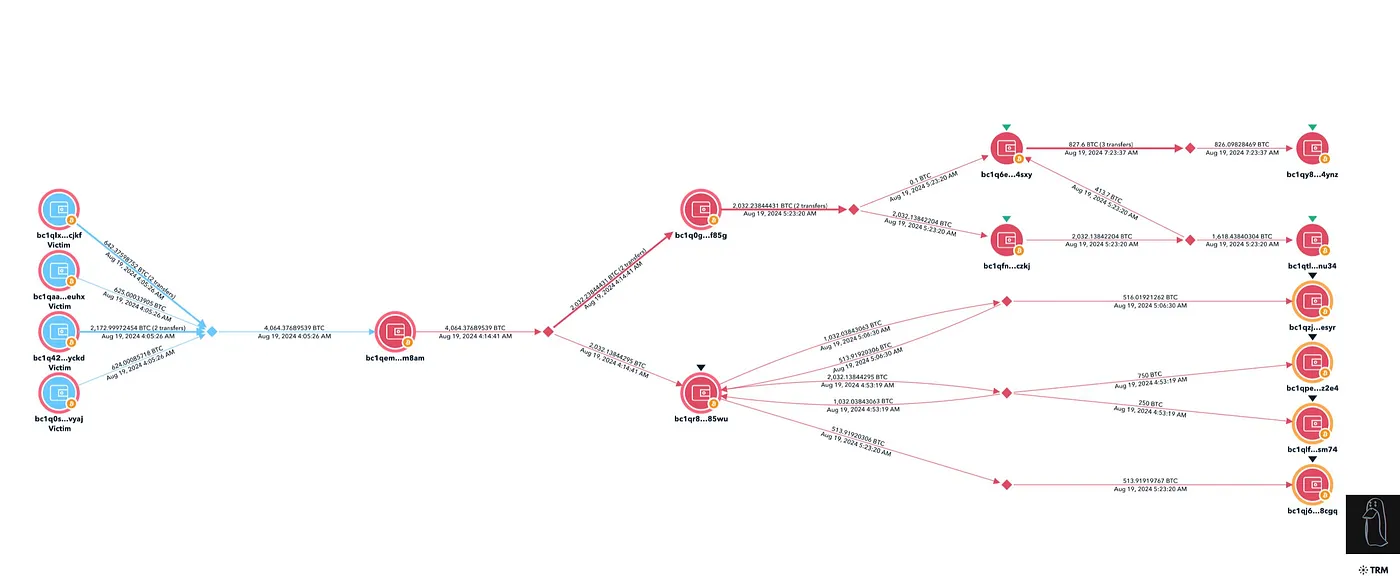
ZachXBT 的初步漏洞追踪 —— 来源:ZachXBT
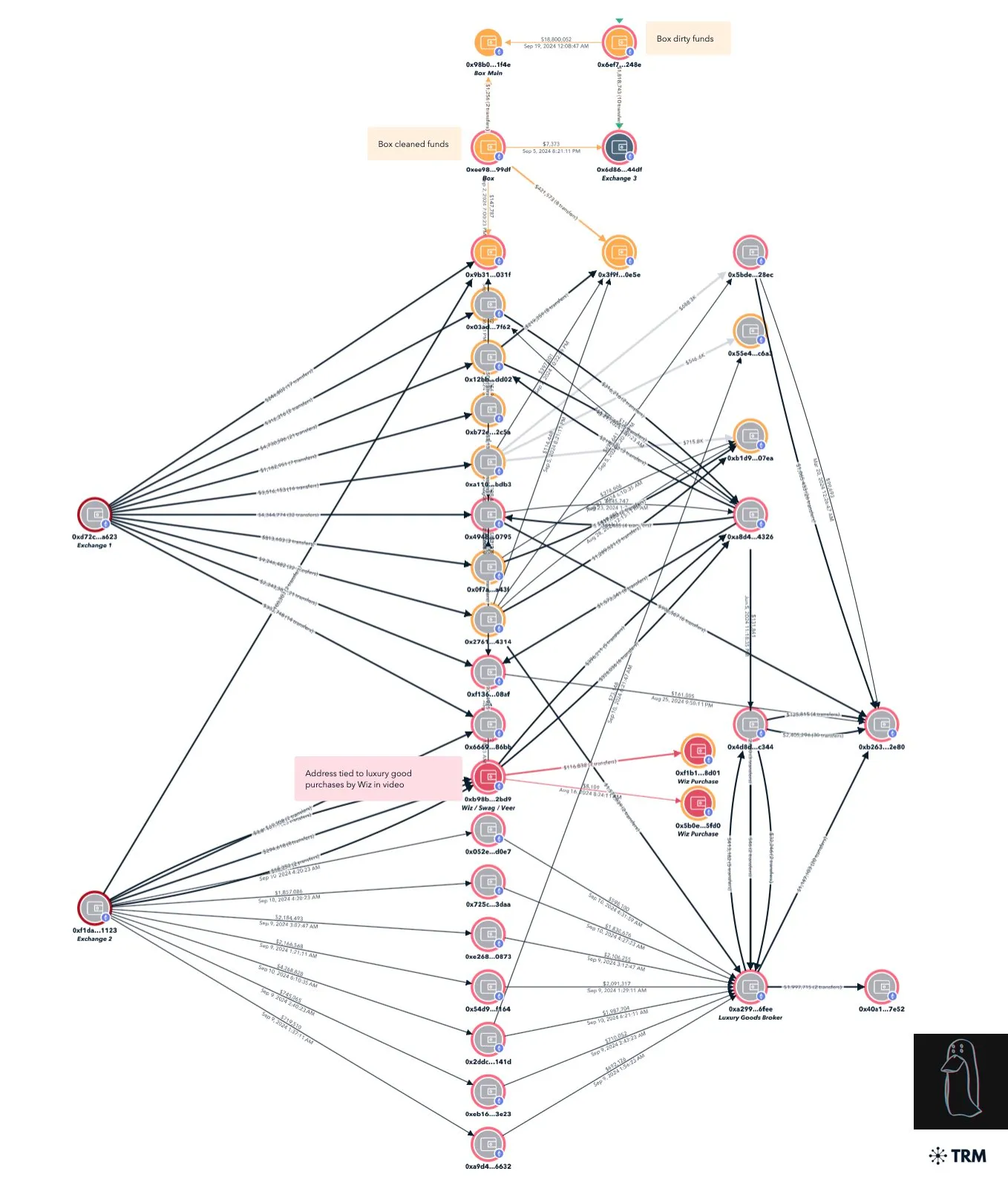
不幸的是对他们来说,幸运的是对受害者来说,他们在攻击和逃跑过程中都不够谨慎。这种疏忽让 ZachXBT 得以将钓鱼攻击追溯到三名主要犯罪嫌疑人及其同伙。
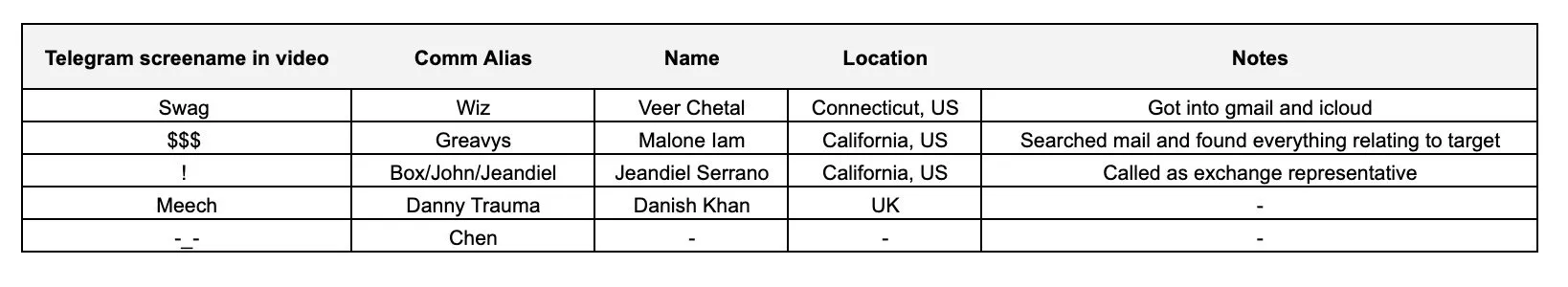
ZachXBT 建立的嫌疑人名单 —— 来源:ZachXBT
他们犯下的众多错误之一是在屏幕共享时向受害者透露了其中两人的名字。
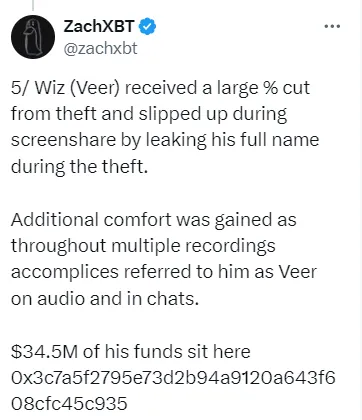
来源:ZachXBT Twitter
其他错误与他们的洗钱技术有关。尽管攻击者将大部分被盗资金转换为门罗币,但 ZachXBT 发现,其中两人因重复使用存款地址而意外混合了被盗资金和干净资金。一名攻击者在共享屏幕时还暴露了一个用来购买名牌服装的地址,该地址与数百万美元的被盗资金有关。
来源:ZachXBT Twitter
他们中的大多数人在社交媒体上留下了足够的痕迹——或者他们的前任留下了痕迹——最终在 ZachXBT 的调查中暴露了完整身份。ZachXBT 与 BN 安全团队、Zero Shadow 和 CryptoForensic Investigators 合作,进一步冻结了 900 万美元。
在 ZachXBT 发布调查结果的前一天,Box(Jeandiel Serrano,21 岁 ) 和 Greavys(Malone Lam,20 岁 ) 被 FBI 逮捕,并于 9 月 19 日被起诉。

Malone Lam —— 来源:ZachXBT
通过社交工程实施的钓鱼攻击一直是许多高收益加密抢劫的核心,其中一次极为复杂的攻击几乎成功从单一个人手中窃取 1.25 亿美元。
2. 2024 年 11 月 1.29 亿美元地址投毒攻击

2024 年 11 月 20 日,一名受害者决定从地址 TGrS7QNCf85X2B6ddvGZY2MF9VwvFn6XAE 向 TMStAjRQHDZ8b3dyXPjBv9CNR3ce6q1bu8 转出约 1.297 亿美元。
他们首先发送了 100 USDT 作为测试转账到地址 TMStaj…6q1bu8。交易成功完成后,受害者几乎立即决定转移全部 1.297 亿美元。
他们不知道的是,在测试交易之后,骗子通过一个伪装成测试地址的地址向其钱包「撒尘」( 发送了 1 USDT)。当受害者复制粘贴目标地址时,他们无意中选择了这个伪装地址。这个伪装地址甚至伪造得很粗糙,只有最后 6 位数字匹配,而前半部分完全不同,以 THcTxQ 开头,而非 TMStaj。
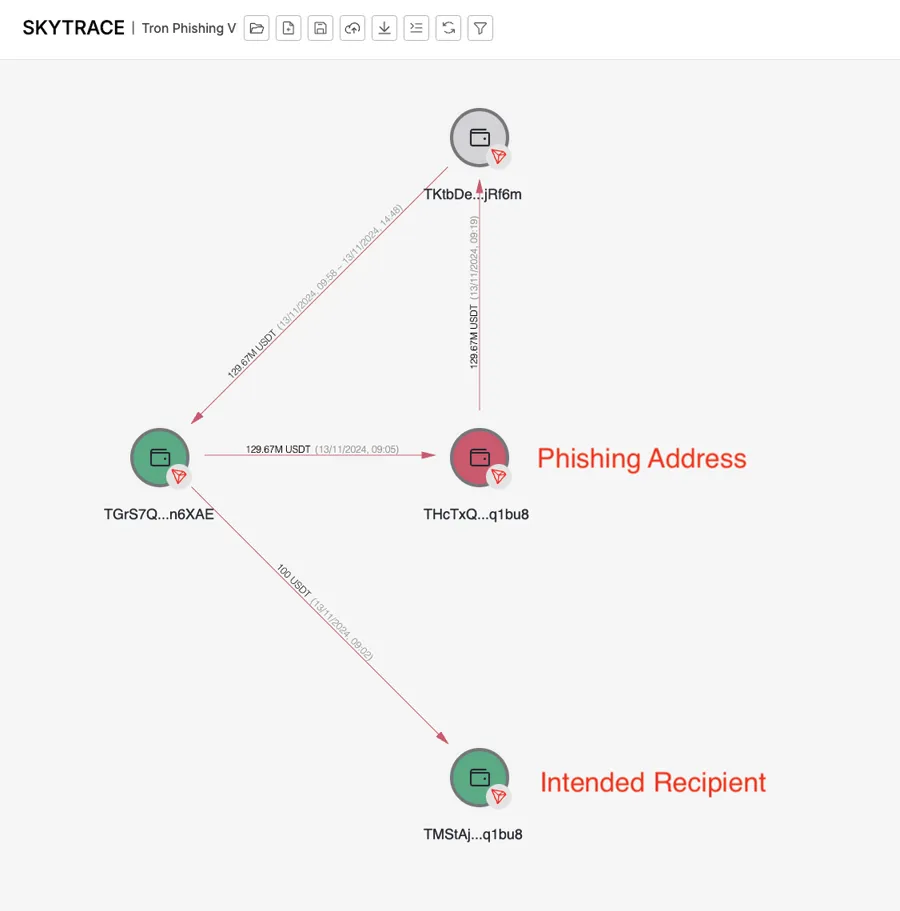
来源:Certik
幸运的是,地址投毒者在 1 小时内归还了 1.167 亿美元,4 小时后又归还了剩余的 1297 万美元。
两次转账和第二次转账的金额 (1297 万美元 ) 似乎表明,攻击者最初考虑拿走 10% 的「漏洞赏金」,但后来改变了主意。
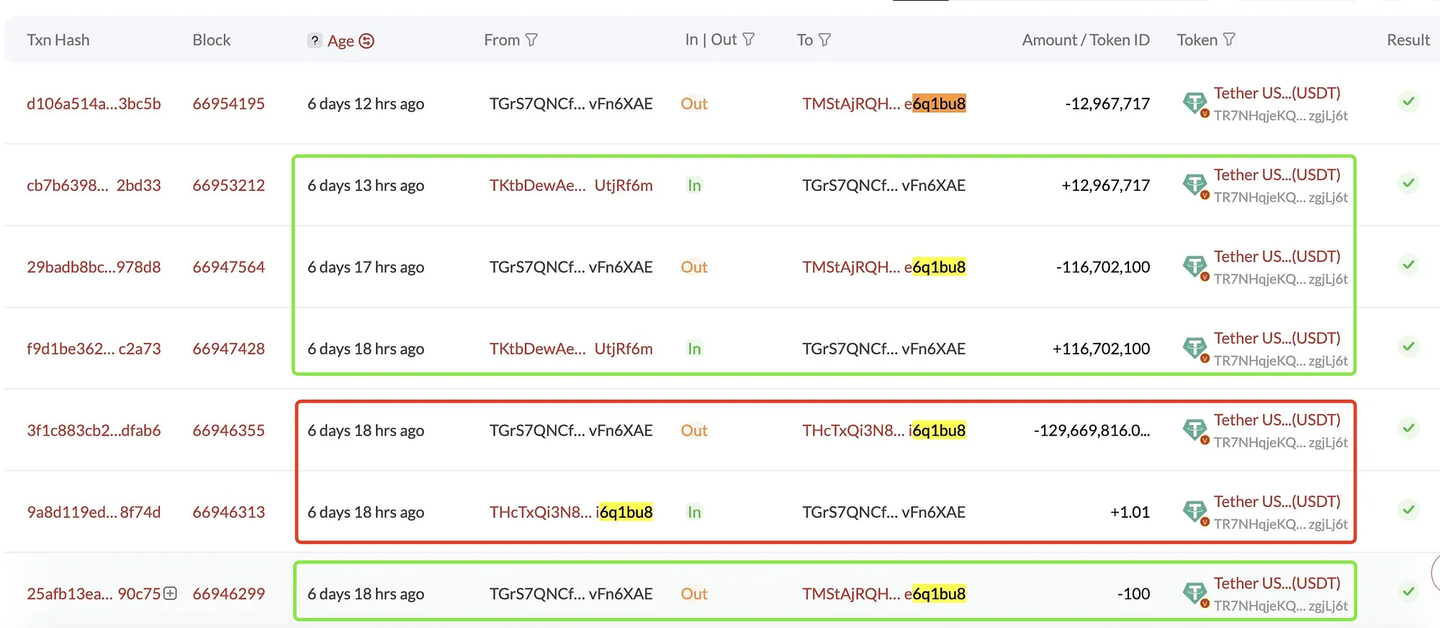
来源:SlowMist via ScamSniffer
他们归还全部资金的最可能原因是恐惧——害怕被拥有资源的受害者、区块链取证社区和执法机构追踪,尤其是考虑到被盗金额之巨,这会让他们成为巨大的目标。
3. Crypto4winners:1 亿美元庞氏骗局

2024 年 3 月 9 日,投资公司 Crypto4winners( 承诺每月 3-20% 的回报 ) 宣布,他们遭遇了一次漏洞攻击。
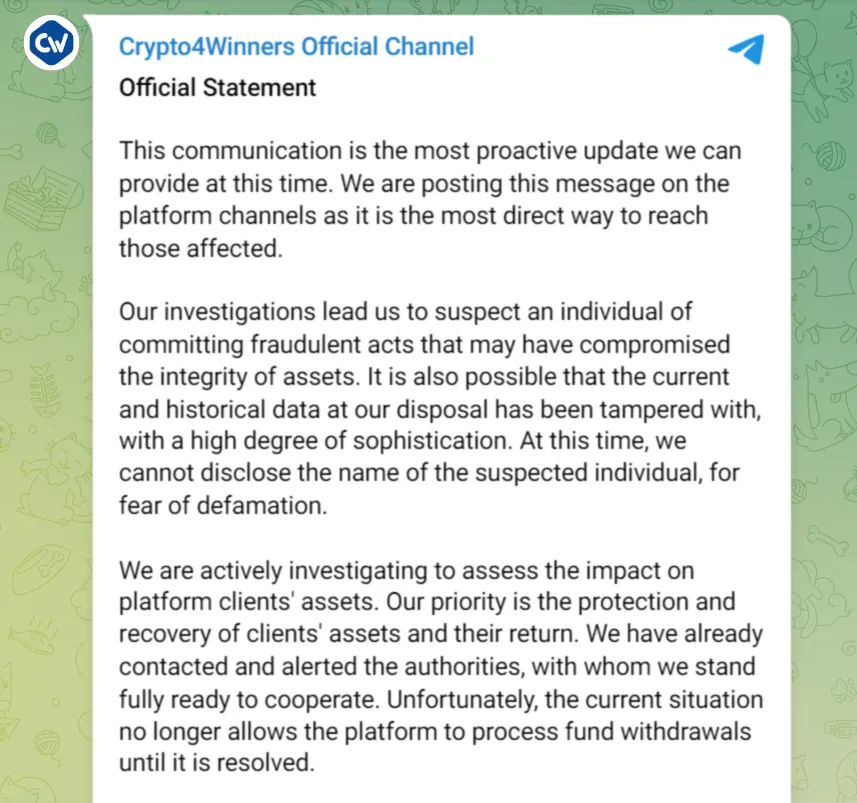
来源:Crypto4winners Telegram 频道
由于这次「漏洞」,Crypto4winners 声称在问题解决前无法处理资金提取。
问题在于,早在两个月前,加密报纸 DL News 就披露,Crypto4winners 的共同所有人之一是 Luc Schiltz,一位卢森堡人,曾在 2017 年因诈骗超过 150 万美元被判六年监禁,仅服刑两年。出狱后不久,他共同创立了 Crypto4winners 项目。
因此,当「黑客攻击」被宣布时,怀疑立即升起。在最初的公告后,Crypto4winners 完全沉默。到了 3 月 12 日或更早,其客户联系了律师和警方。
随后几天,Crypto4winners 被揭露具有庞氏骗局的所有特征,造成了数千名受害者,至少损失 1 亿美元。
根据 DL News,Luc Schiltz 是 Crypto4winners 的共同创始人,但他一直隐藏自己的参与。其公开的 CEO 和创始人是另一位卢森堡人 Adrien Castellani,但实际上,Castellani 只是与 Luc Schiltz 共同创立了该公司。
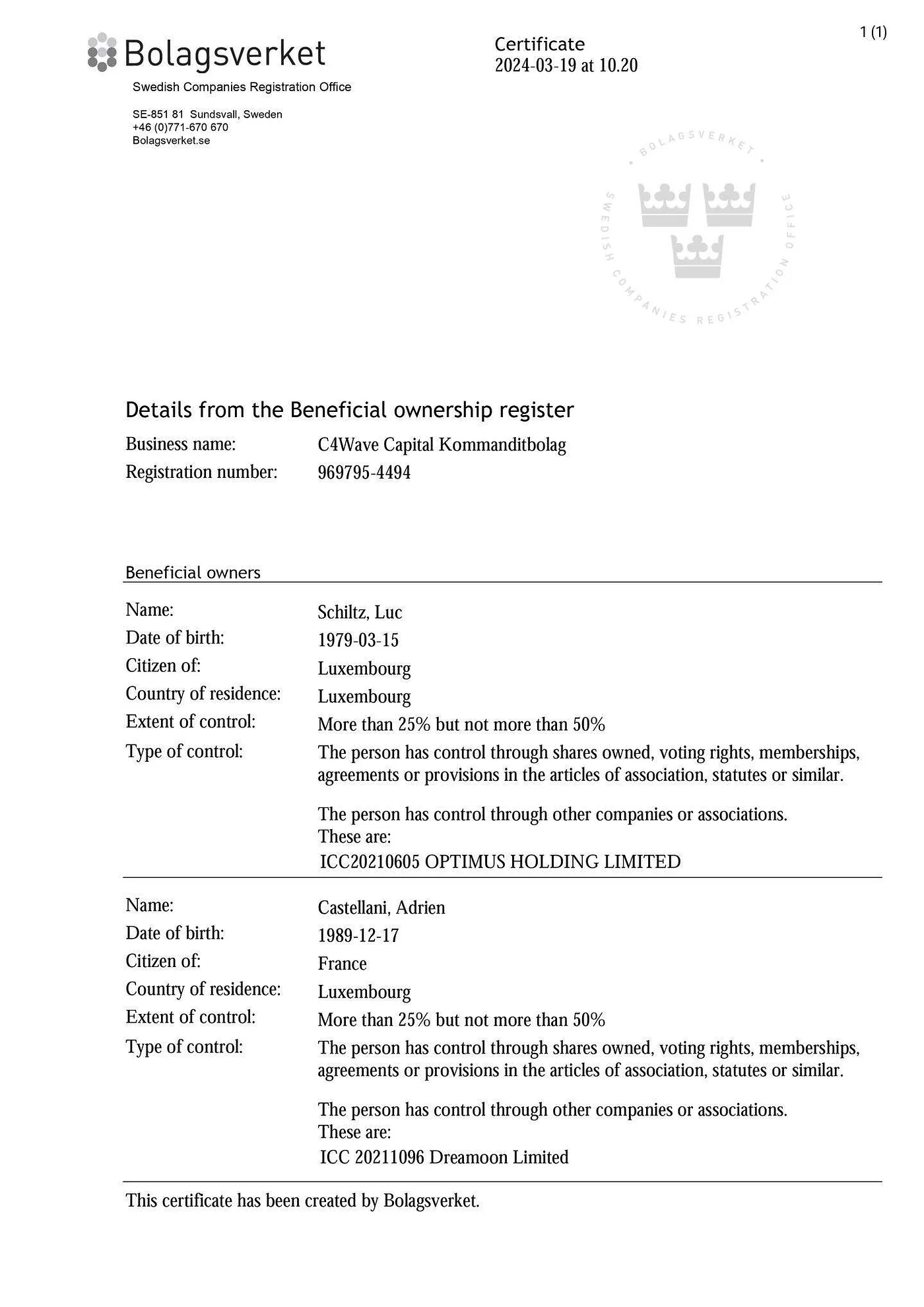
来源:Virgule
尽管多年来关于 Luc Schiltz 参与 Crypto4winners 的问题不断,他从未承认其为共同创始人或合伙人,仅将其称为顾问。2023 年,他承诺到年底与 Crypto4winners 完全切割关系,显然并未兑现。

来源:DL News
谎言层出不穷。
例如他们承诺的疯狂回报。他们甚至声称自 2019 年以来客户比特币存款实现了 377% 的回报,以及每月平均 7% 至 20% 的回报,无论加密市场涨跌,这是典型的加密庞氏骗局特征。
他们还声称与 Chainalysis 和 Ledger 合作,导致这两家公司在 2022 年公开否认这些说法。
Crypto4winners 在瑞典注册成立。2023 年,瑞典公司登记处要求其提交 2021 和 2022 年的年度报告时,他们声称作为信托管理公司无需提交,这是虚假的。即使面临清算或被宣布无效的风险,截止日期到来时他们仍未提交报告。
还发现,Crypto4winners 表面上是卢森堡 - 瑞典实体,实际上是通过迪拜、立陶宛、爱尔兰、瑞典和卢森堡构成的复杂结构。
更糟的是,Crypto4winners 实际上是一家空壳公司;投资者的资金全部被转移到一家名为 Big Wave Developments Limited 的爱尔兰公司。
根据卢森堡报纸 Virgule,在估计的 1 亿美元客户资金中,Big Wave Developments Limited 账户中仅剩不到 20 万美元。
这整个案件最令人瞠目结舌的是其解体的原因:一场非常奇怪的车祸,据称导致 Luc Schiltz 失忆。
3 月 5 日黎明前,Luc Schiltz 撞上了路边护栏,车冲上斜坡。据卢森堡警方称,他在这场事故中未受任何伤,但随后出于未知原因走上了高速公路,被一辆公交车撞倒。
他未受致命伤,被送往骨科住院治疗。
然而,他声称事故导致他失忆。问题在于,Luc Schiltz 完全控制客户资金;这意味着他无法再访问加密货币钱包和交易平台账户中的资金。
值得注意的是,根据 Virgule 的调查和事故后几天探访 Luc Schiltz 的人所述,他的失忆令人怀疑。
一位化名为 Mario 的 Adrien Castellani 的朋友向 Virgule 回忆:
「他最初假装失忆,然后告诉我们他会从父母那里拿回 USB 密钥,一切将恢复正常……」( 译自法语 )
就在那天,Mario 发现了 Crypto4winners 和 Big Wave Developments Limited 的空壳性质。后来在 3 月 12 日与 Shiltz 的通话中,Mario 询问 Big Wave Developments Limited 账户中仅剩的 20 万美元,Shiltz 安慰他说这是正常的,因为这只是热钱包中的资金。
尽管声称失忆,Luc Shiltz 似乎完全清楚自己的身份和公司运作方式。那么,他究竟忘了什么以至于无法访问资金?显然不是种子短语;在加密历史上,一个人仅靠记忆管理 1 亿美元几乎闻所未闻。
他自己曾说,一切都在他父母那里,并保证很快会恢复正常。那么,问题出在哪里?
希望这一事件及其引发的所有疑问能在法庭上揭晓答案。
3 月 15 日,卢森堡公共检察官办公室宣布对 Crypto4winners 展开欺诈和洗钱指控的调查,两名个人已被拘留并被起诉。
其中一人被认为是 Luc Shiltz。
来源:TrustPilot
4. 2024 年 5 月 7200 万美元地址投毒攻击

2024 年 5 月 3 日,一人成为地址投毒攻击的受害者,这次攻击成为当时历史上最大的地址投毒抢劫案,受害者向恶意地址转移了 1155 个包装比特币,损失 7270 万美元。
事情的经过可以归结为极端的坏运气。受害者首先成功向合法地址 ( 以 0xd9A1b 开头 ) 完成了一笔 149 美元的测试转账。之后,他们错误地复制粘贴了一个伪造的地址——一个模仿 0xd9A1b 的投毒地址。
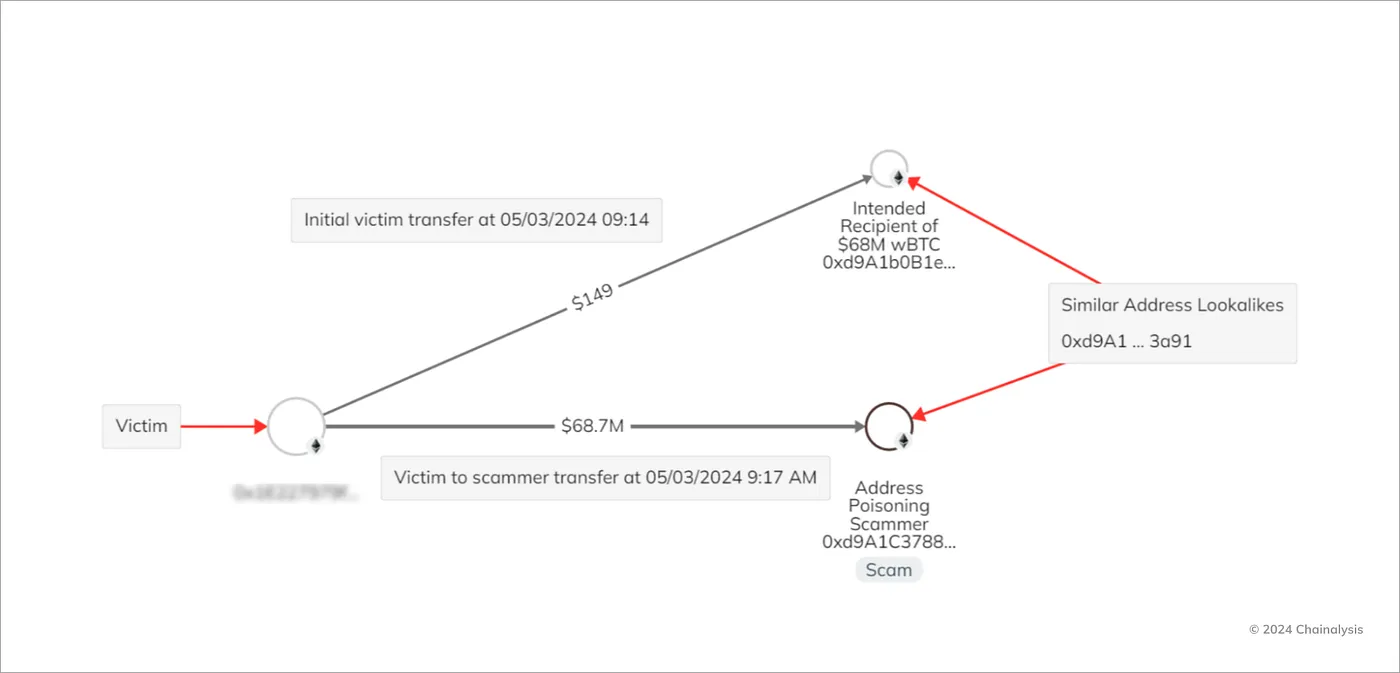
地址投毒分解 —— 来源:Chainalysis
受害者试图通过谈判以 10% 的「漏洞赏金」换回资金,但未能成功。攻击者被贪婪蒙蔽,认为自己能全身而退——他们大错特错了。
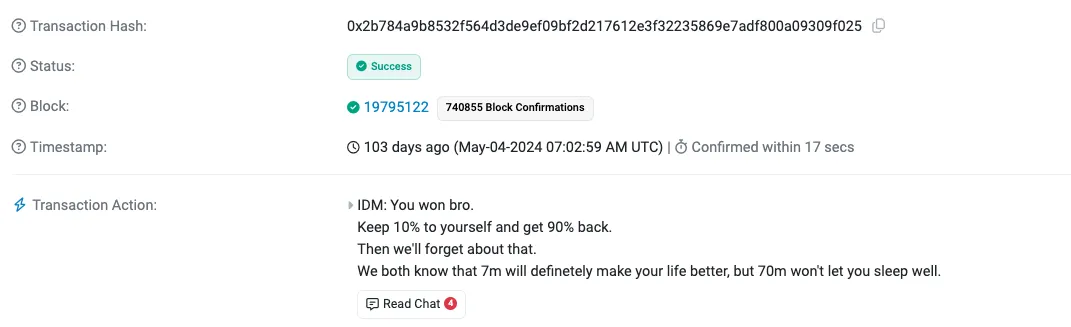
受害者发给攻击者的消息 —— 来源:Chainalysis
整个区块链安全社区都投入了调查,很快传出攻击者归还资金的消息,去掉留作「漏洞赏金」的 720 万美元。5 月 10 日,攻击者归还了几乎所有被盗资金,由于 Token 升值,他们仅带走了 300 万美元。
两周后发现,资金迅速归还并非攻击者良心发现,而是因为尽管他们尽力掩盖踪迹,他们的「设备指纹」暴露了部分身份,据 Match Systems 首席执行官 Andrey Kutin 报告。
5. Epoch Times 首席财务官 6700 万美元加密骗局与洗钱抢劫

2024 年 6 月,Epoch Times 的首席财务官 Bill Guan 因涉及大规模加密骗局被捕。
美国司法部 (DOJ) 指控 Guan 共谋洗钱至少 6700 万美元的欺诈所得资金,包括通过失业保险欺诈获得的收益。据称,该计划涉及使用加密货币以折扣价购买非法资金,然后通过包括 Epoch Times 账户在内的多个账户进行转移,以隐藏资金来源。
当银行报告其收入在一年内从 1500 万美元激增 410% 至超过 6200 万美元时,这一加密骗局暴露。
司法部的起诉书强调,这些指控与 Epoch Times 的新闻活动无关。Guan 面临包括共谋洗钱和银行欺诈在内的严重指控,可能面临最高 80 年监禁。
6 小结
2024 年,Web3 领域对于零售投资者而言是充满危机的一年。诈骗与黑客活动猖獗,导致投资者损失高达 58.4 亿美元,其中「杀猪盘」、钓鱼诈骗和退出骗局是主要的犯罪形式。从比特币的牛市到迷因币的超级周期,市场的繁荣吸引了大量新手和经验丰富的投资者,却也让他们成为诈骗者的理想目标。尽管如此,仍有一些积极的信号,如部分被盗资金被追回,以及相关执法机构和区块链安全社区对犯罪行为的严厉打击和追踪。
然而,这些事件也提醒我们,加密货币市场的风险无处不在,投资者在追求高收益的同时,必须提高警惕,加强安全意识,谨慎对待每一个投资决策,以避免成为下一个受害者。
免责声明:本文章仅代表作者个人观点,不代表本平台的立场和观点。本文章仅供信息分享,不构成对任何人的任何投资建议。用户与作者之间的任何争议,与本平台无关。如网页中刊载的文章或图片涉及侵权,请提供相关的权利证明和身份证明发送邮件到support@aicoin.com,本平台相关工作人员将会进行核查。




