作者:十四君
引言
近日,比特币 L2 项目 Bitlayer Labs 完成了 1100 万美元 A 轮融资,由 Franklin Templeton、ABCDE 和 Framework Ventures 联合领投。与此同时,Bitlayer 成为了首个获得ETF许可机构投资的比特币基础设施项目。
Bitlayer 是一个 BTC 的 L2 项目,初衷是提高BTC的扩展性,解锁其生态的潜力。在项目特色上,Bitlayer 是第一个基于 BitVM 的 L2,同时也是第一个完全继承了BTC安全性并且图灵完备的 L2。
1、 BTC L2 现状
BTC L2 的本质是跨链桥,目前 L2 项目方的跨链桥方案各有各的特色,但是站在技术角度来看,大多数跨链桥方案的本质是多签。
多签方案其实存在严重的信任问题,目前因为多签导致的资金被盗事件屡见不鲜。
笔者认为,L2 作为 L1 的补充,不应该只局限于生态的扩展,同时应该继承 L1 的安全性。
Bitlayer 作为第一个基于 BitVM 的 L2,实现了信任最小化,对安全性和扩展性实现了很好的平衡。接下来不妨跟随十四君的技术视角,探索 Bitlayer 是如何作为 L2 扩展 BTC 的同时又兼顾安全性的。
2、 Bitlayer -兼顾安全性和扩展性的 L2
2.1 Bitlayer 的基本架构
Bitlayer 的基本架构如下图所示。
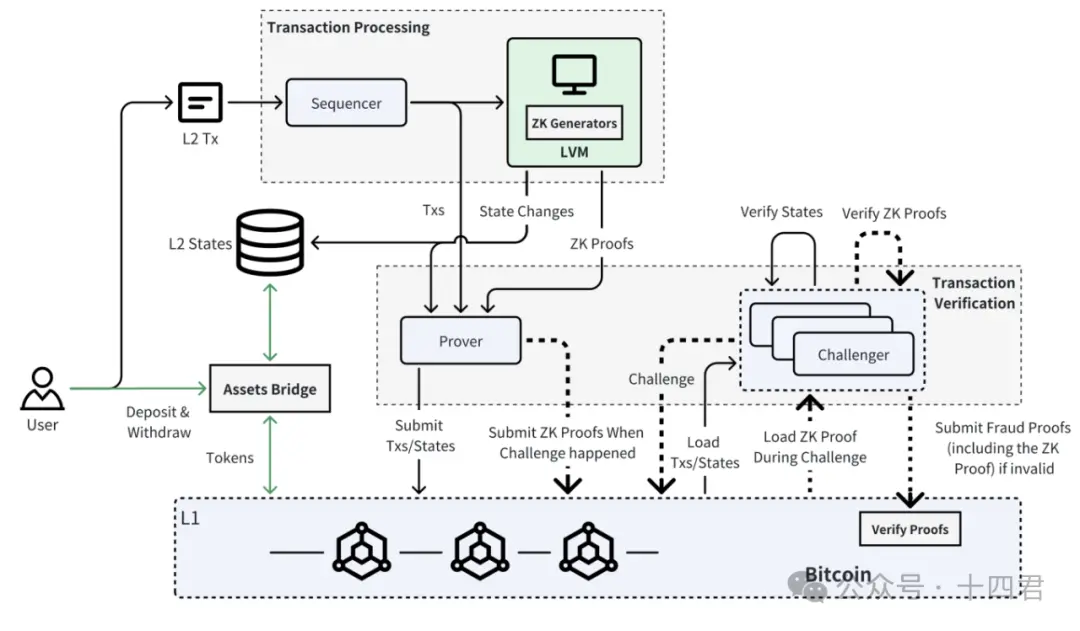
可以看到 Bitlayer 的业务流程主要可以划分为三个阶段,分别是交易处理阶段、交易验证阶段、最终验证阶段。每个阶段交互的组件与其大致的处理流程如下表所示:
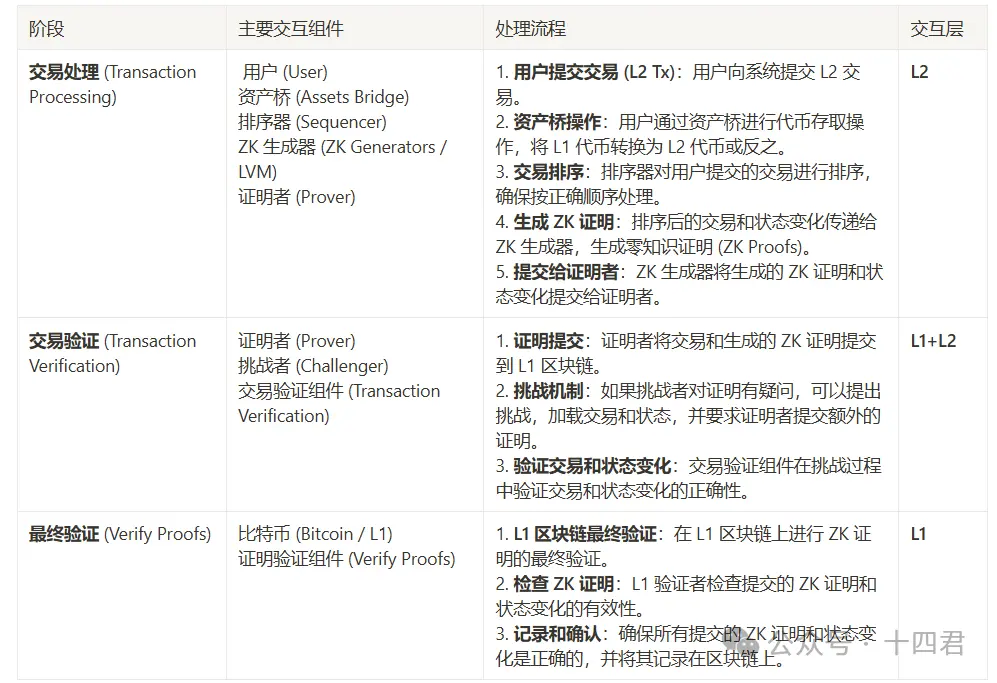
让我们一起来拆解 Bitlayer 的核心流程。
2.2 交易处理阶段-分层虚拟机 LVM
在 L2 的交易处理阶段,有排序器与 LVM (分层虚拟机)两个组件。
排序器不多赘述, Bitlayer 中的序列器负责收集缓存的交易并对其进行排序,是 Bitlayer 中交易的入口点。
LVM 是 Bitlayer 的计算组件,功能职责是负责执行智能合约并生成最新状态和零知识证明。
什么是分层虚拟机?
要解答这个问题,我们直接看下图。
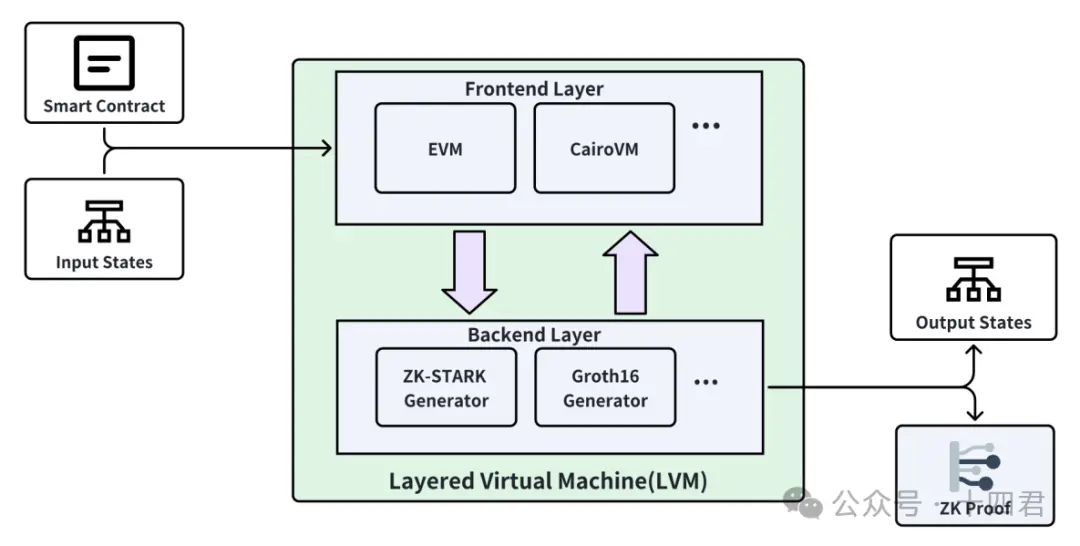
与常规印象的 VM 不同, Bitlayer 的 L VM 实现了前端智能合约的执行与后端的零知识证明器的解耦。 VM 与零知识证明器以组件的形式存在于L VM 。这种创新使得 Bitlayer 可以扩展支持各种合约类型,以及各种零知识证明验证器,大幅提高了系统的扩展性与安全性。
2.3 交易验证阶段-基于 ZKP 的 OP 桥
经典的 L2 跨链问题: L2 如何继承 L1 的安全性?
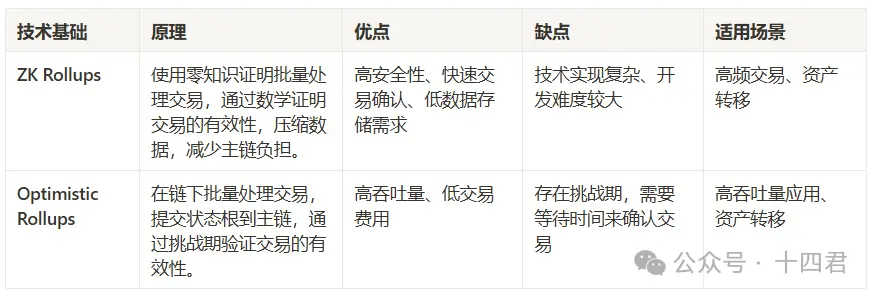
ZK 桥本身因为无需信任其实是目前安全性最高的跨链桥方案, OP 桥通过欺诈证明对无效的跨链数据进行链上挑战(1- N 的安全模型),保证跨链数据的安全。看起来,ZK桥比 OP桥要更安全,但实际上,Bitlayer 核心依赖的 BitVM 选择的是 OP 桥。
为什么是 OP 桥?
主要原因还是技术上的限制,目前只能实现 BTC L1 → L2 存款方向的 ZK 桥,对于 L2 → BTC L1 上提款,目前只支持多签桥或 OP 桥。 Bitlayer 出于安全考虑,选择了更安全的 OP 桥,这其实是一种折中的选择。
Bitlayer 跨链桥方案是 BitVM 桥 + OP - DLC 桥组合的形式, OP - DLC 桥是对 BitVM 桥的补充。
BitVM && OP - DLC 双组合桥流程解析
Bitlayer 使用 Bitvm 桥保障安全性,同时补充 OP - DLC 减少了对 BitVM 的依赖。截止目前, BitVM 桥已经经历了几番升级,实现了纯理论到可实践的飞跃。
BitVM 桥的最新的流程图如下:
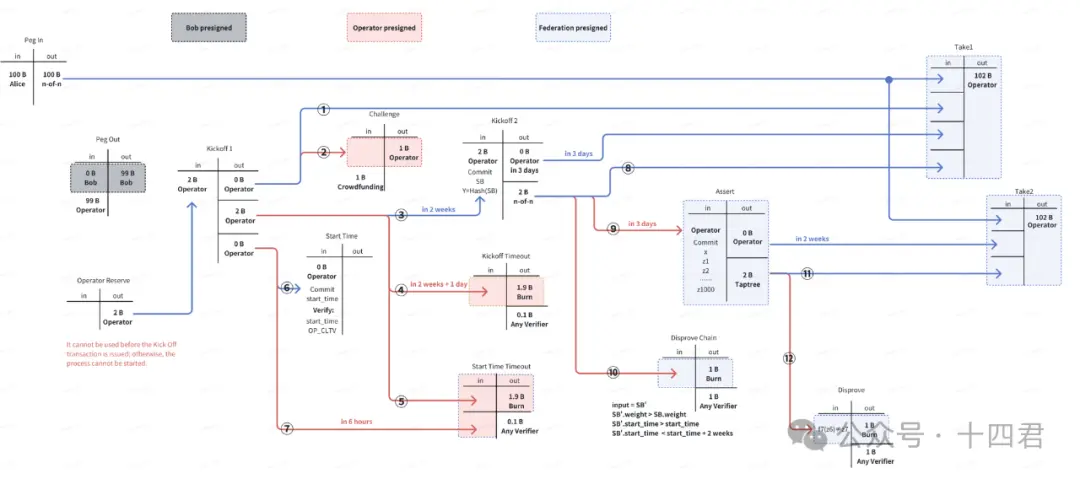
在整个流程中,一共有 5 个角色。
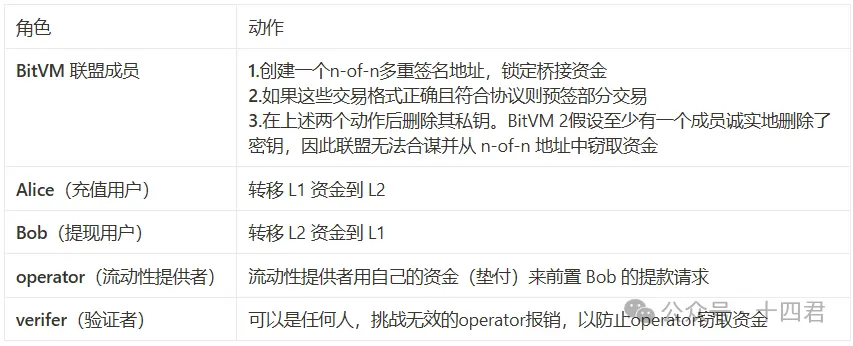
这种模式如何理解?
那么安全性有保障吗?
我们都知道,跨链资金转移的时候,依赖的是公共资金池(本质上是用户锁定的资产),资金池的安全问题是所有跨链桥要解决的核心问题。
传统的 BTC L2 方案一般是通过多签的形式进行公共资金池管理,这种方案显然存在信任风险。而 BitVM 桥采用的是类似闪电网络的思想,预指定资金可以被谁拿走。当用户把资金锁到公共资金池的时候,会与联盟进行通讯,使得资金锁在一个 Taproot 地址上,只能由 Operator 领取,Operator 只有在垫付完成,提供自己垫付的证明到链上,并且被挑战无误后,才能解锁相关的资金。
可以说,BitVM 桥通过引入 Operator 实现了资金池的拆分,这个思路确实新颖。根据以往的经验,我们会惯性地思考如何实现去中心化的资金管理手段,但忽略了资金池这个概念本身就是中心化的,BitVM桥通过资金池去中心化,从源头提升了链桥的安全性。
那么有什么不足之处?
但是,没有方案是十全十美的,总会有一些不尽人意的地方。
细心的朋友会发现,BitVM 桥这种 operator 先预付资金给用户再从公共账户报销形式,类似于资金池的形式。一个池子是公共账户(也就是用户真实锁定的资产,负责直接 给 operator 进行报销),一个池子是 operator 构成的池子,用来直接垫付用户的提现需求(这个池子是虚拟的,分散在不同的 operator 身上)。
用户发起提现的时候是直接与 operator 进行资金往来的,这就相当于,operator 的最终资金变成了资金池的资金 。
提现用户的资金经过了 operator 这一第三方,资金来源已经不是资金池了,与此同时还混杂着别的用户的资金。
受限于这种资金池模式,对于一些资金来源很看重的用户,BitVM 桥其实不能满足其对资金的独立性需求 。
针对这个问题同时减少对 BitVM 桥的过度依赖,Bitlayer 增设了 OP-DLC 的桥接方案,类似管道的思想,实现用户 P2P 的交易,OP-DLC 桥的安全性依赖于欺诈证明以及第三方预言机。
可用性上又如何呢?
BitVM桥的安全性毋庸置疑,但是可用性问题需要持续建设,比如,根据 BitVM 预期,需要大量联盟成员全部在线并正确进行预签名,才能确保流程的正确进行,这其实是一个挑战。
3.总结
在架构上,Bitlayer 的 LVM 实现了智能合约执行与零知识证明的解耦,这其实是一种前瞻的设计思想,使得 Bitlayer 在未来适配各种 VM 以及零知识证明器成为可能。
在跨链桥的技术选型上,Bitlayer 的 BitVM + OP-DLC 的双通道桥是基本上是目前 BTC L2 最安全的跨链桥实现方案(实现了最小化信任)。
Bitlayer 通过技术+工程的融合,基于 BitVM,构建了一套相对来说兼顾安全与扩展性的跨链桥方案,但这也只是一种过渡阶段,是权衡安全性与扩展性之后的折中。
最小化信任应当是 BTC L2 追求的目标,随着 BitVM 一点点变得更加实用化,并且据笔者了解,预计约三个月后 Bitalyer 在 BitVM 的建设上还有一个重大突破,期待 Bitlayer 一步步成为我们期待中的 BTC L2。
免责声明:本文章仅代表作者个人观点,不代表本平台的立场和观点。本文章仅供信息分享,不构成对任何人的任何投资建议。用户与作者之间的任何争议,与本平台无关。如网页中刊载的文章或图片涉及侵权,请提供相关的权利证明和身份证明发送邮件到support@aicoin.com,本平台相关工作人员将会进行核查。




